Windows 10 Enterprise E3 vs E5: What’s the Difference?
Windows 10 Pro is the business version of Windows 10 that comes pre-installed on most PCs when you buy them from Dell, HP, Microsoft etc… Windows 10 Enterprise, is an add-on that sits on top of Windows 10 Pro for added security and mobile device management benefits. Windows 10 Enterprise can be purchased as a monthly subscription for $7 or $11 per user/month depending on which license you purchase, similar to the other Office 365 licenses. There are two Windows 10 Enterprise licenses, called Windows 10 E3 and Windows 10 E5. Both E3 and E5 take all of the features of Windows 10 Pro and kick them up a notch. A HUGE notch. Still, there are some important differences. In this blog, I’ll explain those differences so you can better choose which is right for you: Windows 10 Enterprise E3 or E5.
Note: This blog was last reviewed 2/2022. We do our best to keep all of our blogs up to date to offer you the best, most accurate guidance possible. If you notice otherwise, please drop a comment so we can update the blog. Thank you!
What Is Windows 10 Enterprise?
Despite what the name may entail, Windows 10 Enterprise is not a standalone Windows license. In fact, it is an add-on to Windows 10 Pro. That means you MUST have a current and valid Windows 10 Pro license to use Windows 10 for Enterprise.
Windows 10 for Enterprise is basically the fanciest anti-malware/anti-virus on the planet, and Windows 10 E5 is out of this world. Windows 10 E5 can operate on all your devices no matter the OS (Linux, macOS, Windows 10). It automatically cleans up any virus/malware it finds and then gives you a detailed report as to whose devices are causing problems and where attacks originated. It is seamlessly beautiful, doing all the work for you.
Windows 10 E3 & E5 Feature Differences
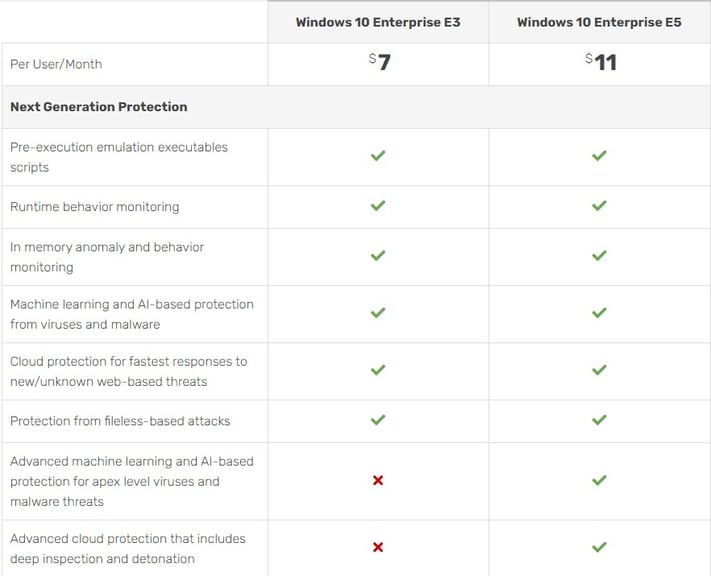
What do you get for an extra $4 per user/month? With Windows 10 Enterprise E5 you get the following 10 additional features, the most important ones are highlighted:
-
Advanced machine learning and AI based protection for apex level viruses and malware threats
-
Advanced cloud protection that includes deep inspection and detonation
-
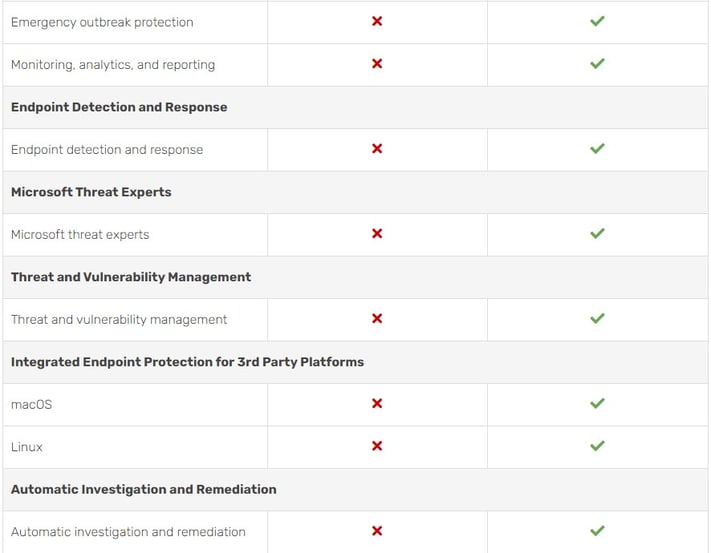
Emergency outbreak protection
-
Monitoring, analytics, and reporting
-
Endpoint detection and response
-
Microsoft Threat Experts
-
Threat and Vulnerability Management
-
Integrated Endpoint Protection across Windows 10, macOS, and Linux
-
Automatic Investigation and Remediation
-
Centralized Configuration and Administrations, APIs
Speaking of security features, the main difference regarding security, between Windows 10 E3 & E5 is that E5 includes Microsoft Defender for Endpoint. FYI, Endpoint is the same thing as Microsoft Defender ATP and Windows Defender ATP, Microsoft just keeps changing the name, making it really confusing. Anyhow…
Microsoft Defender for Endpoint is an enterprise endpoint security platform designed to help enterprise networks prevent, detect, investigate, and respond to advanced threats.
Another huge difference between Windows 10 E3 and E5 is that with E3 it will protect your Windows users from 99.9% of attacks, whereas Windows 10 E5 will protect your Windows, Mac, and Linux users from 99.9% of attacks AND when it fails 00.1% of the time, it will clean up the mess automatically for you. For an extra $4 user/month, it’s a far better deal, hands down.
Windows 10 Enterprise Pricing
Now that you know what Windows 10 for Enterprise is you may be wondering how to get it. Actually, there are a few ways. Windows 10 Enterprise is included with Microsoft 365 E3 & E5 licenses. I’m sure you can guess which license offers which version of Windows 10. For Microsoft 365 E3 (which includes Windows 10 Enterprise E3) the cost is $32 per month/user. For Microsoft 365 E5 (which includes Windows 10 Enterprise E5), the cost is $57.50 per month/user. Check out our blog posts, What is Microsoft 365? and Microsoft 365 vs Office 365 to learn more about those hefty price tags.
You can also purchase either Windows 10 Enterprise add-ons by themselves. The pricing and features to compare the two are as follows:
Windows 10 Enterprise Features
Advanced ML and AI-based protection for Apex-level viruses and malware threats
Behavior data is a great basis for robust, generic detections of malicious cyber activities. This data is made available to Microsoft Defender for Endpoint by sensors built into Windows 10.Microsoft Defender for Endpoint converts these behavioral events into sets of components or features that can be consumed by powerful machine learning technologies like process behavior trees. It also leverages the Microsoft Intelligent Security Graph to augment collected behaviors with important contextual information while applying Microsoft machine learning algorithms, delivering state-of-the art detection of advanced persistent threats (APTs) and the cyberattacks they enable.
Advanced cloud protection that includes deep inspection and detonation
The Deep analysis feature executes a file in a secure, fully instrumented cloud environment. Deep analysis results show the file’s activities, observed behaviors, and associated artifacts, such as dropped files, registry modifications, and communication with IPs. Deep analysis currently supports extensive analysis of portable executable (PE) files (including .exe and .dll files).
Emergency outbreak protection Monitoring, Analytics and Reporting
Emergency security intelligence updates are fast delivery method for protection knowledge. In the event of an outbreak, the Microsoft Defender research team can now issue an emergency request to all cloud-connected enterprise devices to immediately pull dedicated intelligence updates directly from the Windows Defender ATP cloud. This reduces the need for security admins to take action or wait for internal client update infrastructure to catch up, which often takes hours or even longer, depending on configuration. There’s no special configuration for this other than ensuring cloud-delivered protection is enabled on devices.
Monitoring, Analytics and Reporting
Your personalized dashboard answer the three important questions you need to know about each threat: Am I hit? Can I stop it? Am I exposed? Analytics will show you current threats plus recommended actions to take to contain and prevent the threat. Stay up to date with emerging issues and improve your response resiliency.
Endpoint Detection and Response
When a threat is detected, alerts are created in the system for an analyst to investigate. Alerts with the same attack techniques or attributed to the same attacker are aggregated into an entity called an incident. Aggregating alerts in this manner makes it easy for analysts to collectively investigate and respond to threats. Inspired by the “assume breach” mindset, Microsoft Defender ATP continuously collects behavioral cyber telemetry. This includes process information, network activities, deep optics into the kernel and memory manager, user login activities, registry and file system changes, and others. The information is stored for six months, enabling an analyst to travel back in time to the start of an attack. The analyst can then pivot in various views and approach an investigation through multiple vectors.
Microsoft Threat Experts
Threat Experts provides targeted alerts and on-demand expertise for the most important threats to your organization. The video below shows you how to use notifications and experts on-demand.
Threat and Vulnerability Management
Also known as TVM, helps to reduce your overall exposure to threats by providing actionable information all in near real-time. The video below shows the information and actionable insights available through Threat and Vulnerabilty Management.
Integrated Endpoint Protection across Windows 10, macOS, and Linux
Unlike the E3 plan, Window 10 E5 comes with Microsoft Defender for Endpoint, which is the fancy anti-virus / anti-malware that works on all the operating systems. This is so nice because I can use the same software for my PC and Mac users, and is integrated into the Microsoft Admin portal like all the other products. Now you can go to any user and see who they are, what rights/groups they are in, the devices they have joined to your network, and all the possible malware/virus problems they have all in one place, it really is a 360 degree view of everything IT and security related in one place.
Automatic Investigation and Remediation
Automated investigation and response means that you and your team don’t have to keep track of and remediate every threat to your organization, saving you and an your team time and money.
Centralized Configuration and Administration, APIs
The raw data streaming API can ship event information directly to Azure Storage for long-term data retention or to Azure Event Hubs for consumption by visualization services or data processing engines. Both processes allow for real-time events and alerts from instances in a single data stream.
The Wrap Up
While the options (and the name changes) with Microsoft may seem endless, so too are the endlessly ever-increasing improvements in security and functional features. Hopefully, this blog provided a bit more clarity into the offerings your company needs. As always, if you have any questions, please feel free to reach out to us!
Questions? Comments? We want to hear from you! Leave us a note in the comments section below or schedule a 15-minute meeting with me below:
















![Toni Kroos là ai? [ sự thật về tiểu sử đầy đủ Toni Kroos ]](https://evbn.org/wp-content/uploads/New-Project-6635-1671934592.jpg)


