Top 21 security zones in network security in 2022
Below are the best information and knowledge on the subject security zones in network security compiled and compiled by our own team evbn:
Mục Lục
1. Network Security Zones
Author: www.kwtrain.com
Date Submitted: 01/31/2021 05:48 PM
Average star voting: 5 ⭐ ( 46231 reviews)
Summary: One of the most foundational ways to accomplish this is through the use of network security zones, which we’ll take a look at in this blog post. We’ll cover common security zone types, and also zone filtering policy considerations for each.
Match with the search results: A security zone is a portion of a network that has specific security requirements set. Each zone consists of a single interface or a group of ……. read more

2. What is a Security Zone? — Definition by Techslang
Author: www.ibm.com
Date Submitted: 01/30/2021 03:15 PM
Average star voting: 3 ⭐ ( 54447 reviews)
Summary: A security zone is a part of the network to define specific policies and protocols to keep the entire network threat-free. Read more about it here.
Match with the search results: A network security zone is an administrative name for a collection of systems that require the same access control policy. IP addresses are used to map ……. read more
![]()
3. Security Zones: Definition & Purpose | Study.com
Author: www.techslang.com
Date Submitted: 07/19/2020 06:32 AM
Average star voting: 3 ⭐ ( 88684 reviews)
Summary: In this lesson, we will define a security zone and discuss the importance of these zones. We will also discuss the goals of a security zone and how…
Match with the search results: A security zone is a part of the network to define specific policies and protocols to keep the entire network threat-free. The components of a security zone ……. read more

4. About Security Zones
Author: study.com
Date Submitted: 01/21/2020 02:47 PM
Average star voting: 3 ⭐ ( 68829 reviews)
Summary:
Match with the search results: The main objectives of security zones are to protect the network, detect intruders, contain attacks, and prevent these interferences from reaching the internal ……. read more
5. Baseline security requirements for network security zones (version 2.0) – ITSP.80.022 – Canadian Centre for Cyber Security
Author: www.cisco.com
Date Submitted: 03/12/2021 06:04 PM
Average star voting: 5 ⭐ ( 67324 reviews)
Summary: Baseline security requirements for network security zones (version 2.0) – ITSP.80.022
Match with the search results: A security zone is a group of interfaces to which a security policy can be applied to control traffic between zones. For ease of deployment, the Cisco ……. read more

6. Network security zoning – Design considerations for placement of services within zones (ITSG-38) – Canadian Centre for Cyber Security
Author: cyber.gc.ca
Date Submitted: 07/22/2020 09:31 AM
Average star voting: 3 ⭐ ( 23639 reviews)
Summary: Network security zoning – Design considerations for placement of services within zones (ITSG-38)
Match with the search results: Network security zones are the foundations of a balanced and layered security architecture that can support a range of security solutions for ……. read more

7. Bookshelf v8.1/8.2: Network Zones and Firewalls
Author: www.cyber.gc.ca
Date Submitted: 02/04/2021 04:18 PM
Average star voting: 3 ⭐ ( 15442 reviews)
Summary:
Match with the search results: A zone is a construct to define standard baseline security requirements that if adopted by GC departments will lead to consistency in their ……. read more
8. Security Zones | Junos OS | Juniper Networks
Author: docs.oracle.com
Date Submitted: 01/21/2021 04:56 PM
Average star voting: 3 ⭐ ( 70517 reviews)
Summary: A security zone is a collection of one or more network segments requiring the regulation of inbound and outbound traffic through policies. Security zones are logical entities to which one or more interfaces are bound. You can define multiple security zones, the exact number of which you determine based on your network needs.
Match with the search results: To secure a network, divide the network into zones of control by considering factors, such as the type of information contained in the zone and who needs ……. read more
9. Security Zoning in Network Architecture
Author: www.juniper.net
Date Submitted: 04/21/2020 10:38 PM
Average star voting: 3 ⭐ ( 29951 reviews)
Summary: Many organizations struggle to implement the secured Network Architecture that can optimize the Network Security. Organizations usually spend a lot of time, effort, and money deploying the latest and…
Match with the search results: A security zone is a collection of one or more network segments requiring the regulation of inbound and outbound traffic through policies. Security zones ……. read more
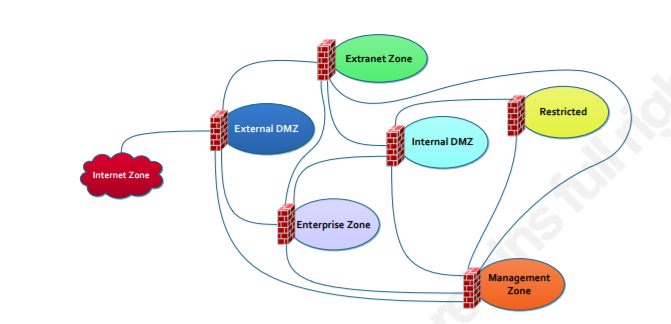
10. Security zoning
Author: medium.com
Date Submitted: 12/15/2020 10:43 AM
Average star voting: 5 ⭐ ( 95860 reviews)
Summary: Information about security zoning in industrial networks, and how this can be achieved using ABB’s routers and firewalls.
Match with the search results: Internet Zone — No Trust · External DMZ — Low Trust · Enterprise Zone — Medium Trust · Extranet Zone — Medium Trust · Internal DMZ — High Trust ……. read more
11. Dividing a Network into Security Zones – Huawei Firewall Security Policy Essentials – Huawei
Author: new.abb.com
Date Submitted: 02/26/2021 12:12 PM
Average star voting: 4 ⭐ ( 50316 reviews)
Summary: null
Match with the search results: A security zone is a portion of a network that has specific security requirements set. Each zone consists of a single interface or a group of ……. read more
12. Security Zones
Author: support.huawei.com
Date Submitted: 01/27/2019 05:36 PM
Average star voting: 5 ⭐ ( 55349 reviews)
Summary:
Match with the search results: A network security zone is an administrative name for a collection of systems that require the same access control policy. IP addresses are used to map ……. read more
13. Placement of Computing Devices in Network Security Zones | IT Services
Author: sc1.checkpoint.com
Date Submitted: 09/25/2021 03:03 AM
Average star voting: 3 ⭐ ( 36063 reviews)
Summary:
Match with the search results: A security zone is a part of the network to define specific policies and protocols to keep the entire network threat-free. The components of a security zone ……. read more
14. The Value of Network Security Zoning
Author: www.youtube.com
Date Submitted: 02/18/2019 08:36 AM
Average star voting: 3 ⭐ ( 38302 reviews)
Summary:
Match with the search results: The main objectives of security zones are to protect the network, detect intruders, contain attacks, and prevent these interferences from reaching the internal ……. read more

15. Security Zone Overview
Author: its.uchicago.edu
Date Submitted: 02/03/2020 03:52 PM
Average star voting: 4 ⭐ ( 19822 reviews)
Summary:
Match with the search results: A security zone is a group of interfaces to which a security policy can be applied to control traffic between zones. For ease of deployment, the Cisco ……. read more
![]()
16. Best Firewall Security Zone Segmentation Free Guide
Author: fallbackstatus.com
Date Submitted: 01/22/2021 12:03 PM
Average star voting: 5 ⭐ ( 91585 reviews)
Summary: Best Firewall Security Zone Segmentation – Free Guide for Network Security Pros – Hardware firewalls, cornerstone of network security for TCP/IP networks.
Match with the search results: Network security zones are the foundations of a balanced and layered security architecture that can support a range of security solutions for ……. read more
![]()
17. Using Security Zones to Protect Your Network Against IoT Security Risks
Author: docs.paloaltonetworks.com
Date Submitted: 10/13/2019 02:16 AM
Average star voting: 5 ⭐ ( 17523 reviews)
Summary: The Internet of Things (IoT) is an emerging industry with the expectation that by 2020, we will have 30 billion connected devices. Because IoT is relatively
Match with the search results: A zone is a construct to define standard baseline security requirements that if adopted by GC departments will lead to consistency in their ……. read more

18. Isolated security zones yield stronger network protection
Author: www.titanhq.com
Date Submitted: 08/05/2019 05:51 AM
Average star voting: 3 ⭐ ( 98977 reviews)
Summary: Limiting interactions among hosts on your network can keep malware from running rampant
Match with the search results: To secure a network, divide the network into zones of control by considering factors, such as the type of information contained in the zone and who needs ……. read more

19. OpenShift and Network Security Zones: Coexistence Approaches
Author: www.zones.com
Date Submitted: 10/20/2019 04:54 PM
Average star voting: 4 ⭐ ( 25542 reviews)
Summary: OpenShift and Network Security Zones: Coexistence Approaches
Match with the search results: A security zone is a collection of one or more network segments requiring the regulation of inbound and outbound traffic through policies. Security zones ……. read more

20. Maximize your cloud security with isolation zones
Author: www.vircom.com
Date Submitted: 12/25/2021 11:20 AM
Average star voting: 3 ⭐ ( 64310 reviews)
Summary: Security zones keep your applications and their data safe from bad actors and can help limit the impact of a security breach.
Match with the search results: Internet Zone — No Trust · External DMZ — Low Trust · Enterprise Zone — Medium Trust · Extranet Zone — Medium Trust · Internal DMZ — High Trust ……. read more

21. How to Define Zones and Conduits
Author: www.sciencedirect.com
Date Submitted: 12/07/2019 06:13 PM
Average star voting: 4 ⭐ ( 46382 reviews)
Summary: A good understanding of zones and conduits, as introduced in the ISA/IEC 62443 series of standards, is fundamentally important to industrial cybersecurity.
Match with the search results: A security zone is a portion of a network that has specific security requirements set. Each zone consists of a single interface or a group of ……. read more
















![Toni Kroos là ai? [ sự thật về tiểu sử đầy đủ Toni Kroos ]](https://evbn.org/wp-content/uploads/New-Project-6635-1671934592.jpg)


