Splunk SIEM Review & Alternatives

Splunk is a free network monitor that captures data from IT systems and stores it.
Although the tool is free, the business that produces it is worth $32 billion. How does Splunk, Inc make its money? Only the core Splunk system is free to use and the expanded version, which would be of interest to large corporations, is a paid system. One of those paid extras is Splunk Enterprise Security, which is the Splunk SIEM.
What is a SIEM?
SIEM is a category of security monitoring software that is intended to identify malicious behavior on a network, on servers, and on endpoints. The purpose of SIEM is to be the second line of defense. It is a backup to border access controls and works on the assumption that some hackers are going to get through any gateway security, either by slipping through undetected or through cooperation by an authorized user.
The types of actions that SIEM aims to spot are insider threats and Advanced Persistent Threats (APTs). An advanced persistent threat is a situation where a hacker group gains access to a network and is able to return at will undetected over a long period of time.
SIEM stands for Security Information and Event Management. It is a hybrid methodology that blends two types of Intrusion Detection Systems (IDSs). These are Host-based Intrusion Detection Systems (HIDSs), which search through log files for signs of unauthorized activity and Network-based Intrusion Detection Systems (NIDSs), which searches passing network traffic for anomalies that indicate an intrusion.
In SIEM terminology, HIDS is called Security Information Management (SIM) and NIDS is called Security Event Management (SEM). SIM + SEM = SIEM.
A SIEM system should also include a threat intelligence feed, a set of detection rules that identify a string of events that sum up to being anomalous behavior, an analytical tool for retrospective root cause analysis, and data protection standard auditing and reporting.
About Splunk, Inc
Splunk, Inc was founded in 2003 and has its headquarters in San Francisco, California. The business first turned a profit in 2009 and it floated on the stock market in 2012. Over the years, the business has added to its original network analyzer product by acquiring related products and integrating its functionality into Splunk.
Splunk, Inc. has mainly expanded into security products with specialized adaptations that include Splunk Insights, to block ransomware, Splunk Enterprise Fraud Monitoring, and Splunk for Industrial IoT, which includes security monitoring for the Internet of Things (IoT) devices.
Splunk Security Operations Suite
Splunk Enterprise Security is part of a group of security modules that is called the Splunk Security Operations Suite. This includes two other packages, which are Splunk User Behavior Analytics, and Splunk Phantom.
User Behavior Analytics is what other SIEM producers call User and Entity Behavior Analytics (UEBA), which rivals integrate into their main SIEM system. This service establishes a baseline of what should be considered normal behavior on the system. UEBA implements machine learning to adjust the thresholds of what the system rule base would be considered to be anomalous behavior. This is a useful feature because SIEMs that use out-of-the-box rules tend to identify legitimate behavior as anomalous and generate too many alerts.
A security system that flags all behavior as suspicious is no use at all and so the inclusion of UEBA has become an industry standard. Therefore, it is highly recommended that anyone considering implementing Splunk Enterprise Security should use this module as well.
Splunk Phantom is a Security Orchestration, Automation, and Response (SOAR) system. This is a concept taken from Intrusion Prevention Systems (IPSs) to connect together access rights management systems and firewalls with the SIEM. This enables mitigation action to be triggered automatically. Typical automated responses would be to block access to specific IP addresses or suspend a user account that has been behaving suspiciously.
Splunk Enterprise Security overview
Splunk Enterprise Security is the core of the Splunk Security Operation Suite. It can be used by itself or combined Splunk User Behavior Analytics and Splunk Phantom.
Splunk’s operating purpose is to collect data about activity on a computer system and store it in a searchable format. This action is the heart of any SIEM system. Ordinarily, a SIEM collects and consolidates the log messages generated by software, operating systems, and firmware on all of the equipment that makes up the whole IT system. A SIEM adds live traffic analysis results to that pool of log data.
Mục Lục
Log Management
The standard Splunk, either the free Splunk or the larger Splunk Enterprise, includes a log server and log file management system. Splunk can be set up to gather log messages from all possible sources and store them centrally in an accessible format. One of the main motivations for a business to get a SIEM is to comply with data security standards. These standards, such as HIPAA, and GDPR require that all actions relating to sensitive data be logged and those logs need to be made available for auditing. So, regular Splunk takes care of that requirement.
Standard Splunk also includes log management functions that enable meaningful searches on data. Splunk Enterprise Security relies on this underlying service for its SIM functions.
Network traffic monitoring
The functions of standard Splunk gather network data and store it for analysis. A SIEM needs to be able to correlate events occurring on the network and on endpoints and servers around the system. Splunk excels at unifying different data sources for investigation.
Threat intelligence
Essentially, threat intelligence is the essence of Splunk Enterprise Security. It is the extra bit that the SIEM tool adds to all of the data collection and analysis functions that are built into the standard Splunk package.
Splunk enables users to examine data through searching, sorting, and aggregating system data. Splunk Enterprise Security provides pre-written search strings, which are derived from threat intelligence.
When competitor SIEM systems talk about threat intelligence, they mean a constantly updated feed of new attack vectors that can be input directly into the SIEM tool to add new detection rules. Splunk Enterprise Security doesn’t automatically include this service because Splunk doesn’t have a research lab to supply it. Instead, Splunk recommends seven sources of threat intelligence, which are all delivered in a format that Splunk can read and the user can elect to add to Splunk Enterprise security in the settings of the system.
The options are:
-
Emerging Threats
-
Hail a TAXII.com
-
I-Blocklist
-
Malware Domains
-
abuse.ch
-
Phishtank
-
SANS
Users can also explore other threat intelligence sources as long as the delivery format is compatible with Splunk.
Vulnerability scanning
In Splunk Enterprise Security, vulnerability scanning is a by-product of the standard threat intelligence-driven data searches. Splunk is expandable with many plugins and add ons available from the user community forum, which is called Splunkbase. Most of the apps available at Splunkbase are free and there are also paid tools in the library.
There are a number of vulnerability scanning apps available from this source. However, it is more common for users to deploy a separate vulnerability scanner and feed data from that into Splunk.
Splunk SIEM configuration options
All Splunk Security Operation Suite components can be installed on Windows, Linux, macOS, FreeBSD, Solaris 11, and AIX. The service is also available in the cloud, which includes storage space and processing power as well as the Splunk Enterprise Security software.
Dashboard
Whether on-premises or in the cloud, the Splunk dashboard is accessed through a web browser. The following browsers can be used:
-
Google Chrome
-
Mozilla Firefox
-
Internet Explorer 11 (not in Compatibility mode)
-
Safari
The dashboard is that of Splunk Enterprise with the Enterprise Security system classified as an add-on. The user selects the security app from a dropdown list next to the Splunk Enterprise at the top left of the screen.
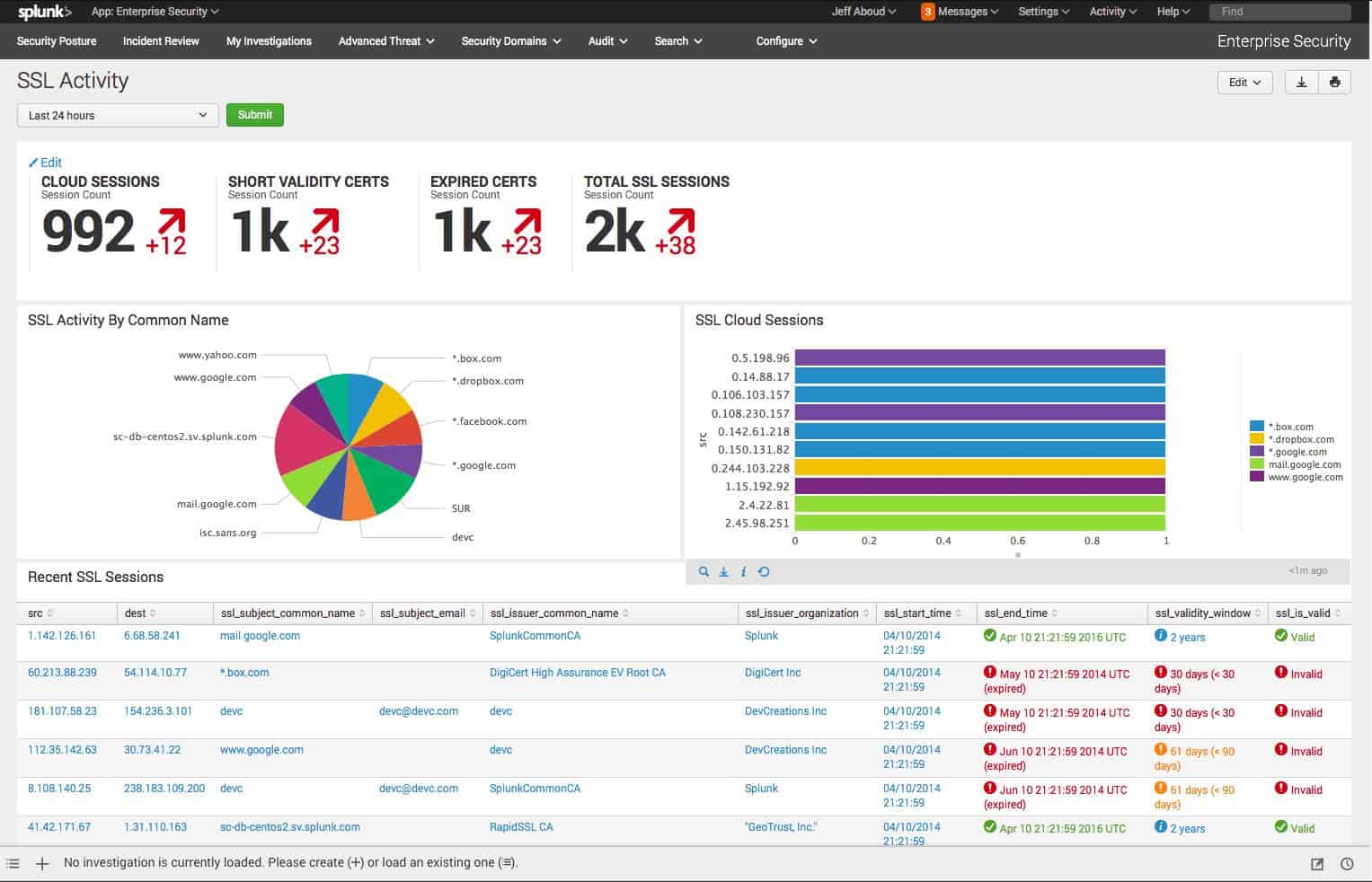
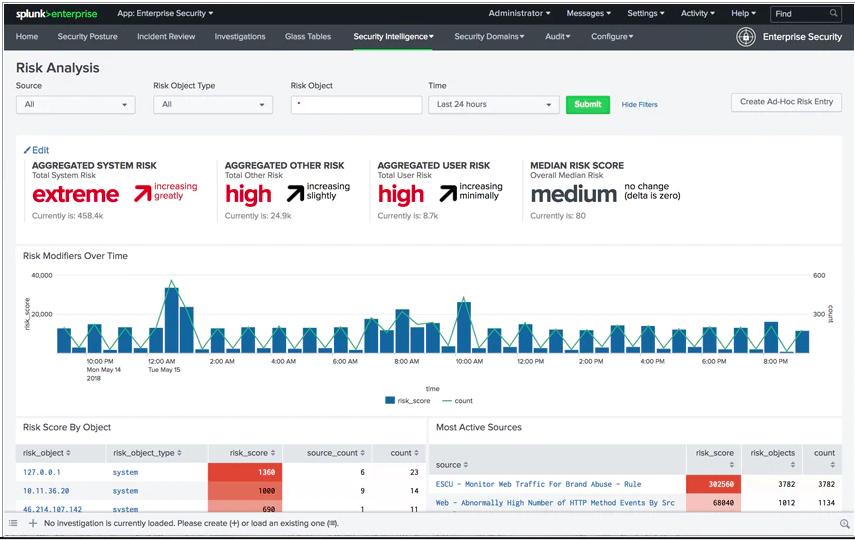
The service includes more than 100 standard screens. The console can be customized. Each element in each screen is supplied with data by a search string. This string can be adapted to create custom results. Many of the screens, such as the Risk Analysis screen shown below, include attractive graphs and charts – all of these can be altered by changing the queries that supply data to them.
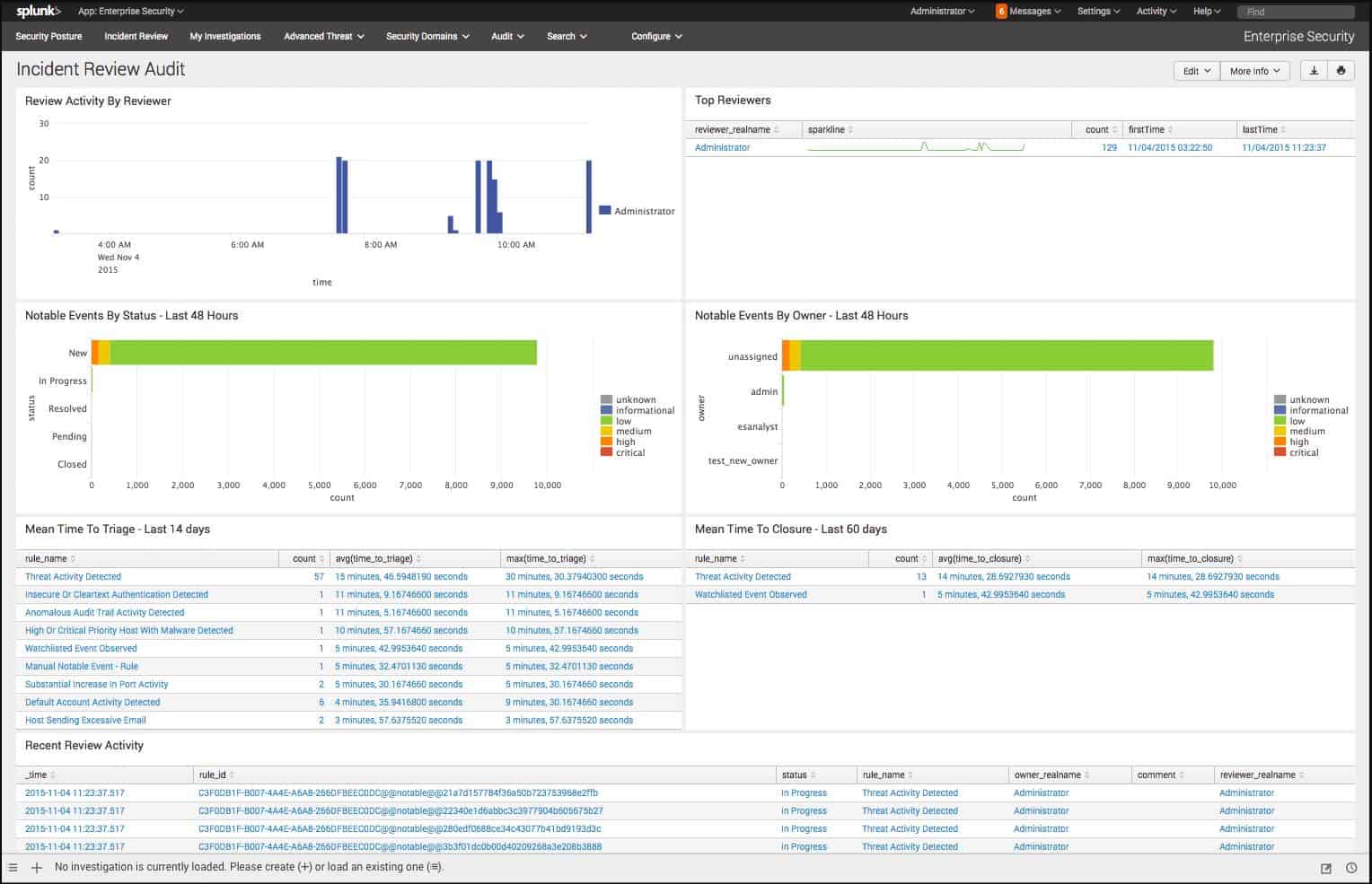
Incident data viewing screens don’t need to be customized because they have search filters and column selection features in the structure of the display that allows data to be analyzed and manipulated. This is shown in the image of an incident report below.
Attack mitigation
Automated attack response isn’t included with Splunk Enterprise Security but it is available with the wider Security Operation Suite through Splunk Phantom. Customers who want to add in automated response workflows should add Splunk Phantom to Splunk Enterprise Security for their SIEM solution.
Compliance reporting
Just as the standard Splunk Enterprise dashboard is adapted by the Enterprise Security app, special apps can be added on to ensure security standard compliance. These adapted screens are accessed by selecting the specific compliance standard from the dropdown list of installed apps that is next to the Splunk Enterprise title at the top left of the dashboard.
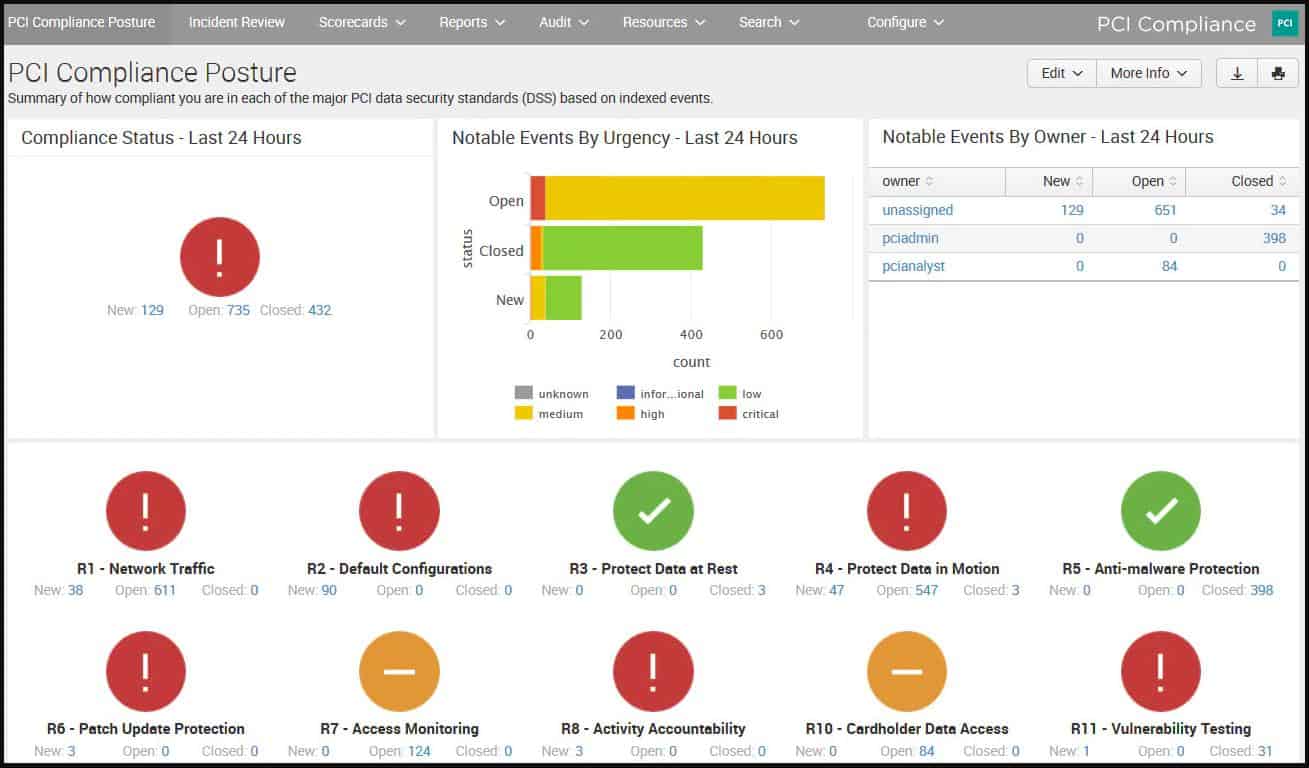
Splunk has adaptations for PCI DSS, GDPR, HIPAA, and ISO/IEC 27001.
The best Splunk SIEM Alternatives
Splunk markets Splunk Enterprise Security as being suitable for large businesses. The system needs a lot of set up in order to get it fully working as a SIEM. For example, threat intelligence is not automatically fed into the system, but an external source of this information has to be assessed and included in the service.
The Splunk SIEM is very flexible and those who are familiar with the Splunk system will enjoy exploring extra plugins and add-ons that will enable them to get the most out of the system. People who are not so comfortable with Splunk would probably worry that they hadn’t done enough to get the system working fully. The need to study how Splunk could be adapted would be off-putting for most time-pressed system managers.
Network managers who are looking for an easier, plug-and-play SIEM solution have a lot of options because there are a lot of SIEM systems on the market today. To find out more about SIEM and the best systems that compete in the market, take a look at our best SIEM tools post. Alternatively, if you are looking to outsource the work and employ a team of SIEM experts instead, check out the best managed SIEM services post.
Here is our list of the best alternatives to Splunk SIEM:
- SolarWinds Security Event Manager
(FREE TRIAL)
A strong log management and analysis system that provides the SIM part of SIEM. The tool includes automated response options and good analysis support with strong data visualizations. This virtual appliance installs on VMWare vSphere or Microsoft Hyper-V. Start a 30-day free trial
- ManageEngine EventLog Analyzer
(FREE TRIAL)
Log360 tool to get network analysis functions. It installs on Windows and Linux. Start a
A SIM service that manages logs and provides data analysis tools. Add on thetool to get network analysis functions. It installs on Windows and Linux. Start a 30-day free trial
- Datadog Security Monitoring
A SIEM system that is one of the configuration options of this comprehensive system monitoring cloud-based service. It requires agent software to be installed on-premises.
- McAfee Enterprise Security Manager
A comprehensive SIEM backed by threat intelligence feeds from a leading cybersecurity research lab. Includes log and traffic analysis and has the option for an automated response. This system is particularly strong on Active Directory management. It installs on Windows and macOS.
- Fortinet FortiSIEM
An advanced cloud-based SIEM system that is delivered from the cloud and includes agent software for each monitored device so it can still function if the internet connection fails. It includes UEBA and automated defense responses
- Rapid7 InsightIDR
A complete security package that involves threat detection and automated response mechanisms. This is a cloud-based service that also needs agent software installed on each on-premises device to ensure continuity of service.
- OSSEC
A free open-source HIDS that takes care of the log analysis part of SIEM. Feed-in network traffic through files sourced from other monitors to get a full SIEM solution. Installs on Windows, macOS, Linux, and Unix.
- LogRhythm NextGen SIEM Platform
An advanced SIEM that includes uses AI methods to reduce false positives. The tool covers both traffic inspection and log analysis. The software installs on Windows and Linux.
- AT&T Cybersecurity AlienVault Unified Security Management
AlienVault is a well-established brand in cybersecurity and now it is backed by the big-budget of AT&T. It installs on Windows and macOS.
Splunk SIEM FAQs
Is Splunk the best SIEM?
Splunk by itself is a data management and analysis tool but the business behind the tool has added on many new services, which include a really great SIEM system.
Is Splunk good for security?
Splunk is a flexible tool that you can use to build your own data analysis systems – even a threat detection package. However, thanks to the pre-written Splunk Enterprise Security service, you don’t need to go to those lengths. The core of Splunk Enterprise Security is its SIEM system.
Related Posts:
Sumo Logic vs Splunk
Graylog Vs Splunk















![Toni Kroos là ai? [ sự thật về tiểu sử đầy đủ Toni Kroos ]](https://evbn.org/wp-content/uploads/New-Project-6635-1671934592.jpg)


