Popular Network Protocols | Baeldung on Computer Science
Mục Lục
1. Overview
In this tutorial, we’ll present a set of the most used and popular network protocols.
2. Introduction to the Network Protocol
Communication and the exchange of information are the most important and powerful skills in today’s modern world. Computer networking is the interconnection of multiple computers and devices by cables and satellites, allowing them to share information, resources, databases, and more regardless of the distance between them.
To ensure efficient and secure communication within networks, many protocols were designed. A protocol is a set of rules that define how communication occurs in a network.
Essentially, it allows connected devices to communicate with each other, regardless of any differences in their internal processes, structure, or design. We can easily communicate with people all over the world by using various network protocols, and thus it plays a critical role in modern digital communications.
3. Ethernet
Ethernet is a protocol made for Local Area Networks (LAN). It was first standardized in 1983 as IEEE 802.3 and used with thick single coaxial cable 10BASE-5.
The Ethernet 802.3 protocol defines the physical layer in wired networking models, as well as the medium access control (MAC) sub-layer of the data link layer.
There are several versions of the IEEE 802.3 protocol, e.g., 802.3a, 802.3i, 802.3j. Each version is designed to work on different types of cables.
Another widely used protocol is IEEE 802.11, which specifies the physical layer and media access control (MAC) protocols for implementing wireless local area network (WLAN). This protocol is a wireless computer networking standard and used to allow laptops and smartphones to communicate without being connected with a cable.
Let’s see the frame format of Ethernet 802.3 and Ethernet 802.11 protocols:
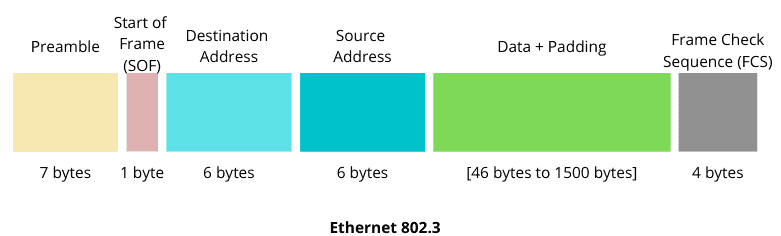
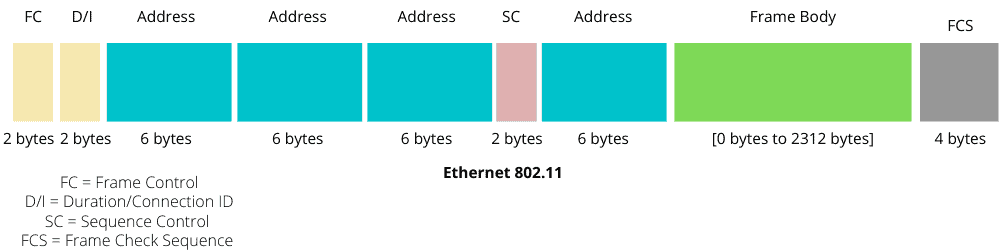
The main differences between 802.3 and 802.11 are in the frames sizes, the fields, and the size of transported data. Ethernet 802.11 protocol has two more address fields than the 802.3, and its frame body size is larger than 802.3 (a maximum of 1500 bytes for 802.3 and 2312 bytes for 802.11).
4. Internet Protocol (IP)
Standardized by IEEE in 1974, this protocol is responsible for addressing and fragmenting data packets in digital networks. Its goal is to ensure the successful delivery of packets from source to destination. For this purpose, the IP specifies a format that defines the type of description of data packets called IP datagrams.
The first major version of IP is IPv4, and it was first deployed on SATNET in 1982. It uses a 32-bit address space. The latest version of the internet protocol, IPv6, uses 128-bit address space to create unique TCP/IP address identifiers.
Let’s see the header format for IPv4 and IPv6:
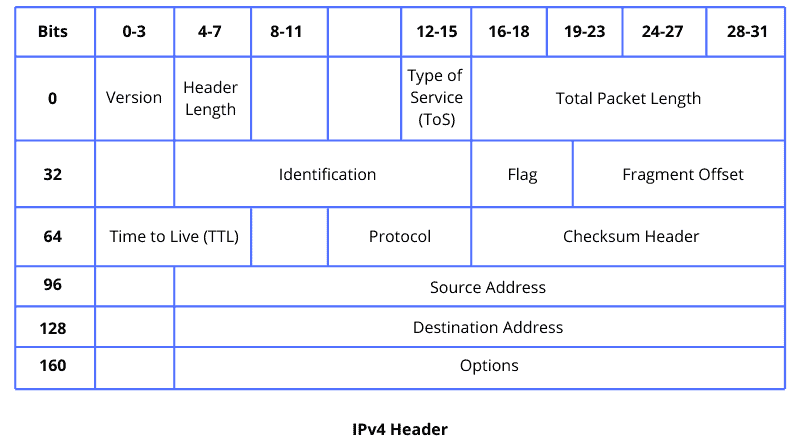
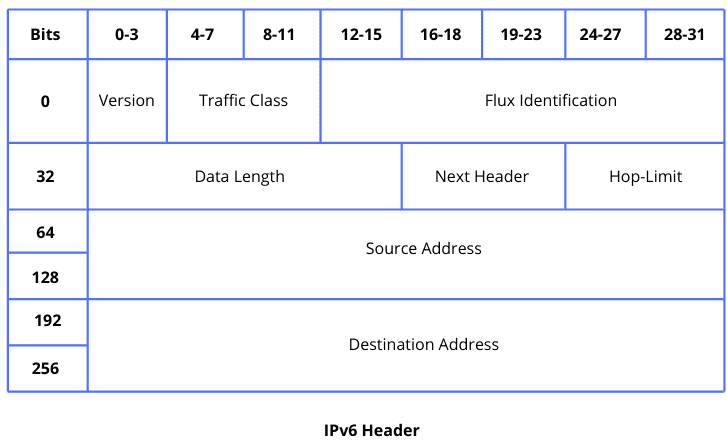
The main difference between IPv4 and IPv6 is the use of address space. The difference between these two can be found in the header, where multiple fields are present in one header but absent from the other. The IPv4 format was reviewed and improved to IPv6, which is more efficient and less complicated.
5. Internet Control Message Protocol (ICMP)
ICMP protocol is made to send error messages in a network. It works with the IP protocol. It helps to diagnose network communication issues. ICMP is mainly used to determine whether or not data is reaching its specified destination in the best ways.
Let’s see what the ICMP header looks like:
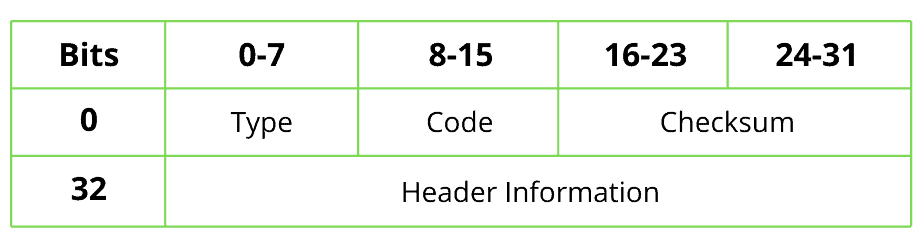
Since this protocol sends error messages, those errors are determined by a code and type. A checksum specifies the message’s precision, and further information about the error will be saved in the header information field.
Unlike IP, ICMP is a connectionless protocol. To send an ICMP message from one system to another, it is not needed to establish a connection between systems.
Generally, ICMP is found on network devices like routers. It is also used in distributed denial-of-service(DDoS) attacks.
6. Address Resolution Protocol (ARP)
Computer applications use the logical address to communicate with other applications. But to communicate with other applications, we need a physical address (MAC address). This is where we need the Address Resolution Protocol (ARP).
It maps network addresses to the physical addresses used by a data link protocol. It is the process of finding an address of a computer in a network. The ARP translates addresses of the network layer to addresses of the data link layer from the OSI networking model.
Let’s see an example of an ARP message for MAC hardware address resolving:
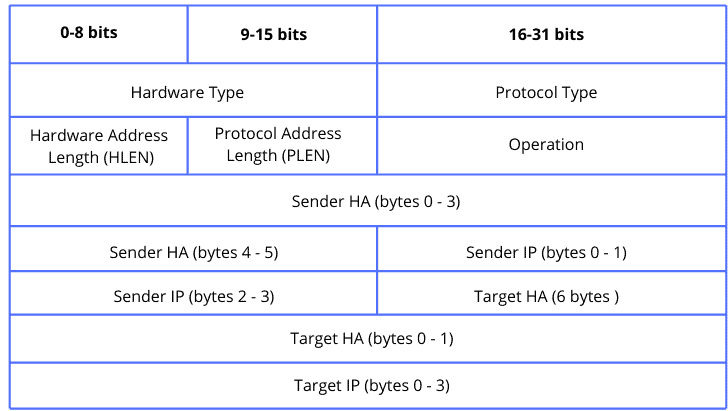
The ARP is one of the most important pillars in the networking process, and it is commonly used with the IP protocols suite.
7. Transmission Control Protocol (TCP)
The Transmission Control Protocol (TCP) is a standard that defines how to establish and maintain a network connection through which application programs can exchange data. It is used on the top of IP to provide reliable transmission of packets.
TCP is a connection-oriented reliable protocol. Two devices need to establish a connection before start using TCP and sending the data. It also provides an acknowledgment to the sender device regarding the status of the data being sent. So in case, the sender receives a negative acknowledgment, it resends the data:
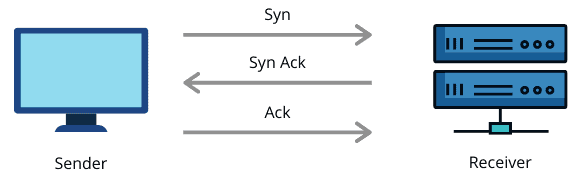
During the data transmission, some data may get lost, or some error may occur. TCP provides an error-checking and recovery mechanism to handle such situations.
Because TCP uses the direct connection, TCP packet header must contain source and destination port information to exchange messages within a network:
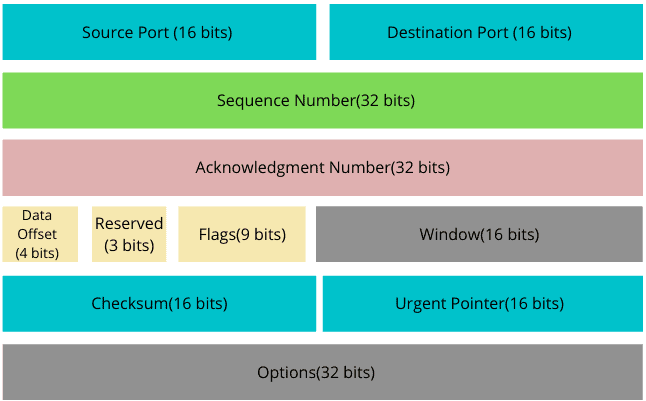
We can find many applications for the TCP protocol, including the secure shell, the file transport protocol, and the web accessing through the HTTP, World Wide Web (WWW), and email.
8. User Datagram Protocol (UDP)
The User Datagram Protocol (UDP) is a transport layer protocol used for communication through internet networks for time-sensitive transmissions. It sends messages without the initiation of a connection, which makes the data transfer real quick.
UDP is a connectionless and unreliable protocol. Unlike TCP, there is no mechanism in UDP for packet recovery in case of packet loss. Also, it doesn’t have any error checking process. But in terms of latency and bandwidth, UDP is more efficient than TCP.
Since TCP keeps a conversation flow between connected devices, there is always the need to synchronize and receive the acknowledgment for the sent messages. However, UDP doesn’t maintain such a connection, which means the sender device will keep sending responses to a request without the necessity for an acknowledgment message:
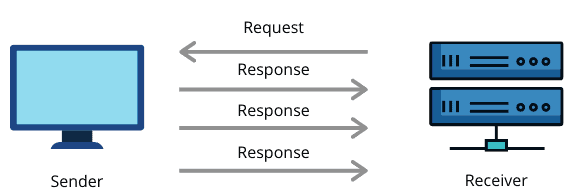
Let’s now see how a UDP header looks like:
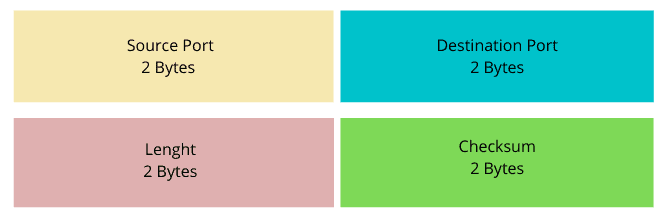
More differences between UDP and TCP can be found in our comparison between UDP and TCP.
UDP is used in real-time services like video communication, online gaming, live streaming of videos, etc.
9. Hypertext Transfer Protocol (HTTP)
The Hypertext Transfer Protocol (HTTP) is the foundation of the World Wide Web (WWW) and is used to load web pages using hypertext links. HTTP is an application layer protocol, which allows the user to see a user-friendly interface designed to transfer information between networked devices. It is the protocol helping applications to communicate with the users.
A web client is any user application like a web browser. A server is a computational system usually stored in the cloud. When a web client wants to communicate with a web server through WWW, it sends an HTTP request to the server. As soon as the server receives the request, it processes the request and sends an HTTP response to the client. The client receives the HTTP response.
It should be noted that an HTTP request header is not the same as a response header:
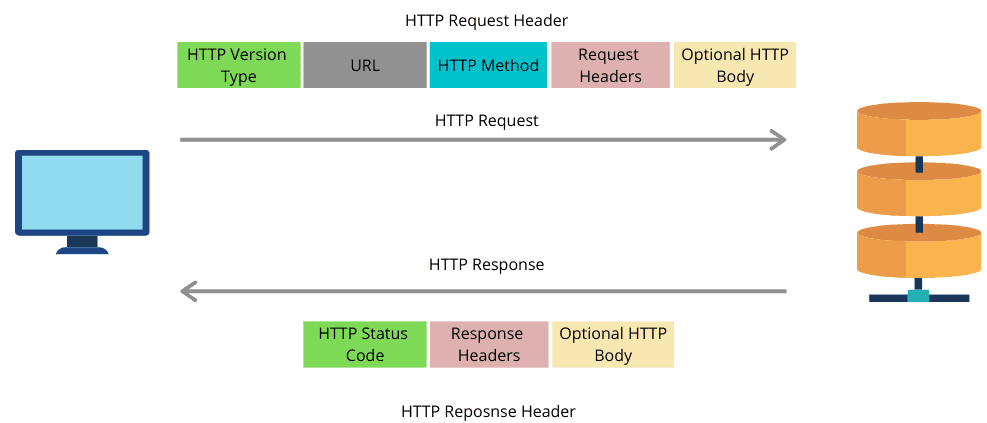
HTTP is a connectionless and stateless protocol. A client and server know each other only during communication. As soon as they complete their communication, both of them forget about each other. It is also media independent. Any data can be sent through HTTP.
10. Dynamic Host Configuration Protocol (DHCP)
This protocol works on IP networks, assigning IP addresses to devices and hosts connected to the network. It also allows them to communicate with each other efficiently.
In addition to the IP address, DHCP also assigns the subnet mask, default gateway address, the domain name server (DNS) address, and other pertinent configuration parameters.
A client device sends discovery messages through a network to a DHCP server, which sends the client an offer. The client then sends back its request allowing the DHCP server to acknowledge the query:
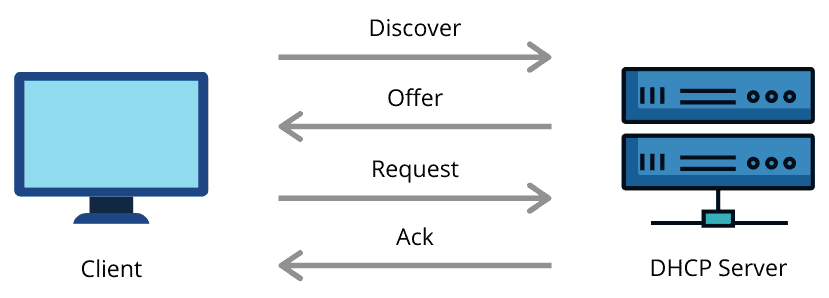
Let’s now look at the DHCP header format:
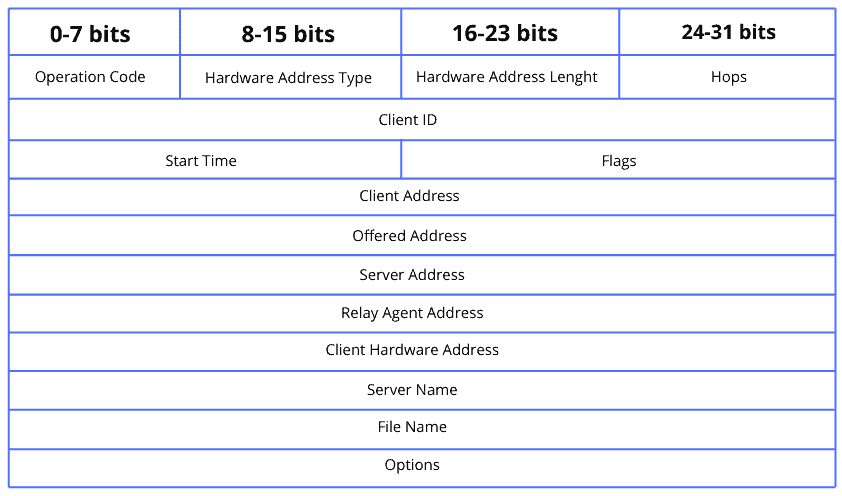
11. Spanning Tree Protocol (STP)
Defined by IEEE 802.1d, this protocol prevents loops on LAN. The STP deals with issues related to networks with bridges. It eliminates redundant links and process network changes and failures.
The STP monitors all the links in the network. To find any problem present in the links or a redundant link, it applies the spanning-tree algorithm (STA). The STA builds a topology out of the current network and removes the redundant links. When a new link is added to the existing network, the STP reruns the STA to ensure the new link is not redundant.
The STP protocol uses configuration messages as its protocol frames. Networking devices that support the STP exchange configuration messages to create a spanning tree. We’re presenting here a standard format of a configuration message:
12. File Transfer Protocol (FTP)
The File Transfer Protocol (FTP) is a standard network protocol provided by TCP/IP, and it is used to transfer files from one server to another. It is responsible for the reliably and efficient transfer of files.
Transferring a file from one server to another is simple, but several problems may arise. The sender system and the receiver server may have different file conventions or different ways to represent data. In some cases, the directory structures of two systems may differ from each other. FTP resolves all of these issues.
While transferring a file between two systems, it establishes two connections. One connection is for the data transfer, and the other one is for control connection:
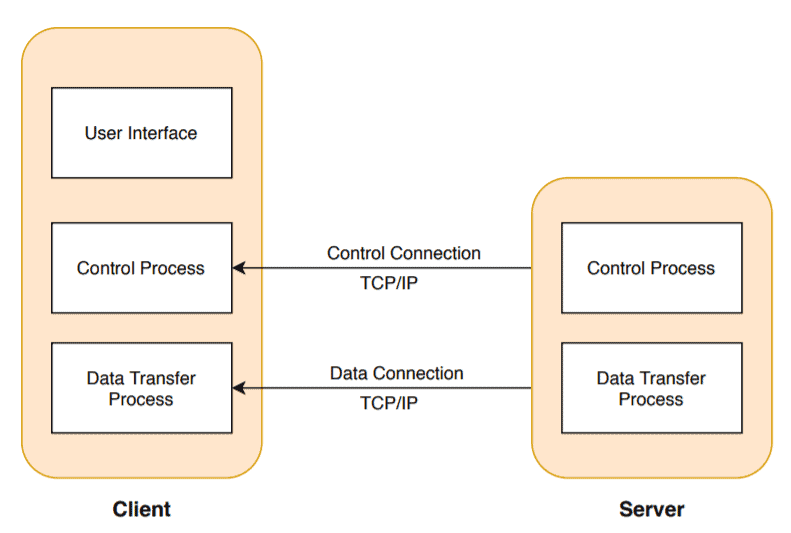
The advantage of the FTP is speed and efficiency. Also, it provides security. The user needs to have a username and password to access the data from the FTP server. The FTP supports the back and forth movement of the data. So sender and receiver both can send data to each other.
The FTP has some drawbacks as well. The data that can be sent through the FTP is limited to 2GB. Therefore any file bigger than 2GB can’t be transferred through the FTP. Also, it is not compatible with every system.
13. Secure Shell (SSH)
Secure Shell (SSH) is a network protocol that uses cryptography in order to secure network services over unsecured networks. Many applications like the execution of a comment remotely, access to a remote computer can be secured with SSH. More details about SSH can be found in our introduction to SSH.
14. SSH File Transfer Protocol (SFTP)
The SSH File Transfer Protocol (SFTP) also known as secure FTP is used to secure the connection when a file is sent remotely from one system to another. It uses s public-key encryption to secure communication over the Internet as well as facilitate strong user authentication. The Internet Engineering Task Force (IETF) developed this protocol in 2006 to provide security to the shell protocols.
There are two ways a user can establish a connection with an SFTP server: either by password authentication or using private/public-key authentication.
FTP uses two connections to send the data. SFTP can send a file through a single connection. This eliminates the inconvenience to server administrators:
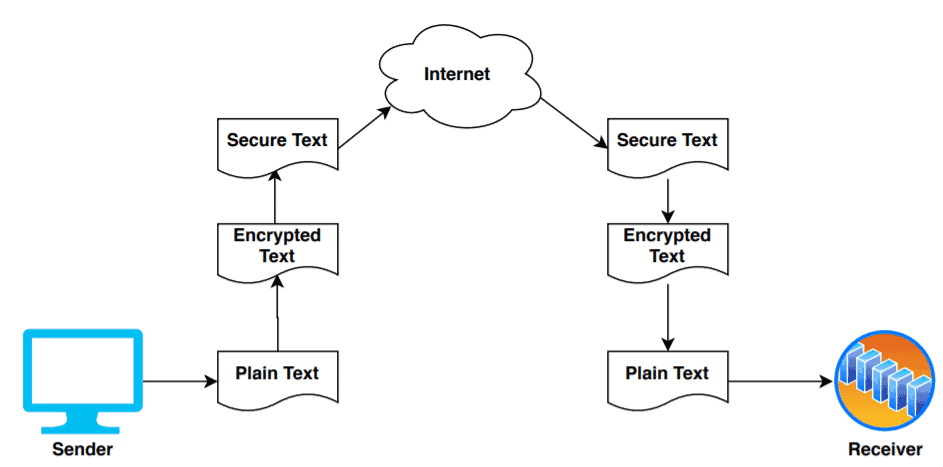
Also, file transfer using SFTP is much faster as it transfers files in binary format. It supports operations related to permission and attributes manipulation and file locking.
15. Conclusion
In this tutorial, we’ve discussed 12 network protocols that are most widely used and extremely popular. We presented a concise introduction and some applications of these protocols.
Though the presented protocols might have some limitations regarding their efficiency and complexity, they still remain the most used ones in networking technologies.
Protocols are designed and developed to properly build, maintain and secure information sharing through networks, leading most businesses and companies to rely on such way of communication, and connecting people through the internet where they can share and receive knowledge and experience.















![Toni Kroos là ai? [ sự thật về tiểu sử đầy đủ Toni Kroos ]](https://evbn.org/wp-content/uploads/New-Project-6635-1671934592.jpg)


