DMZ Network: What Is a DMZ & How Does It Work? | Okta
A demilitarized zone network, or DMZ, is a subnet that creates an extra layer of protection from external attack.
Network administrators must balance access and security. Your employees must tap into data outside of the organization, and some visitors need to reach into data on your servers. But some items must remain protected at all times.
A DMZ network could be an ideal solution. Use it, and you’ll allow some types of traffic to move relatively unimpeded. But you’ll also use strong security measures to keep your most delicate assets safe.
Mục Lục
What Is a DMZ Network?
The internet is a battlefield. Some people want peace, and others want to sow chaos. The two groups must meet in a peaceful center and come to an agreement. When developers considered this problem, they reached for military terminology to explain their goals.
In military terms, a demilitarized zone (DMZ) is a place in which two competing factions agree to put conflicts aside to do meaningful work. A strip like this separates the Korean Peninsula, keeping North and South factions at bay.
A DMZ network, in computing terms, is a subnetwork that shears public-facing services from private versions. When implemented correctly, a DMZ network should reduce the risk of a catastrophic data breach. Public-facing servers sit within the DMZ, but they communicate with databases protected by firewalls.
In 2019 alone, nearly 1,500 data breaches happened within the United States. Sensitive records were exposed, and vulnerable companies lost thousands trying to repair the damage.
While a network DMZ can’t eliminate your hacking risk, it can add an extra layer of security to extremely sensitive documents you don’t want exposed.
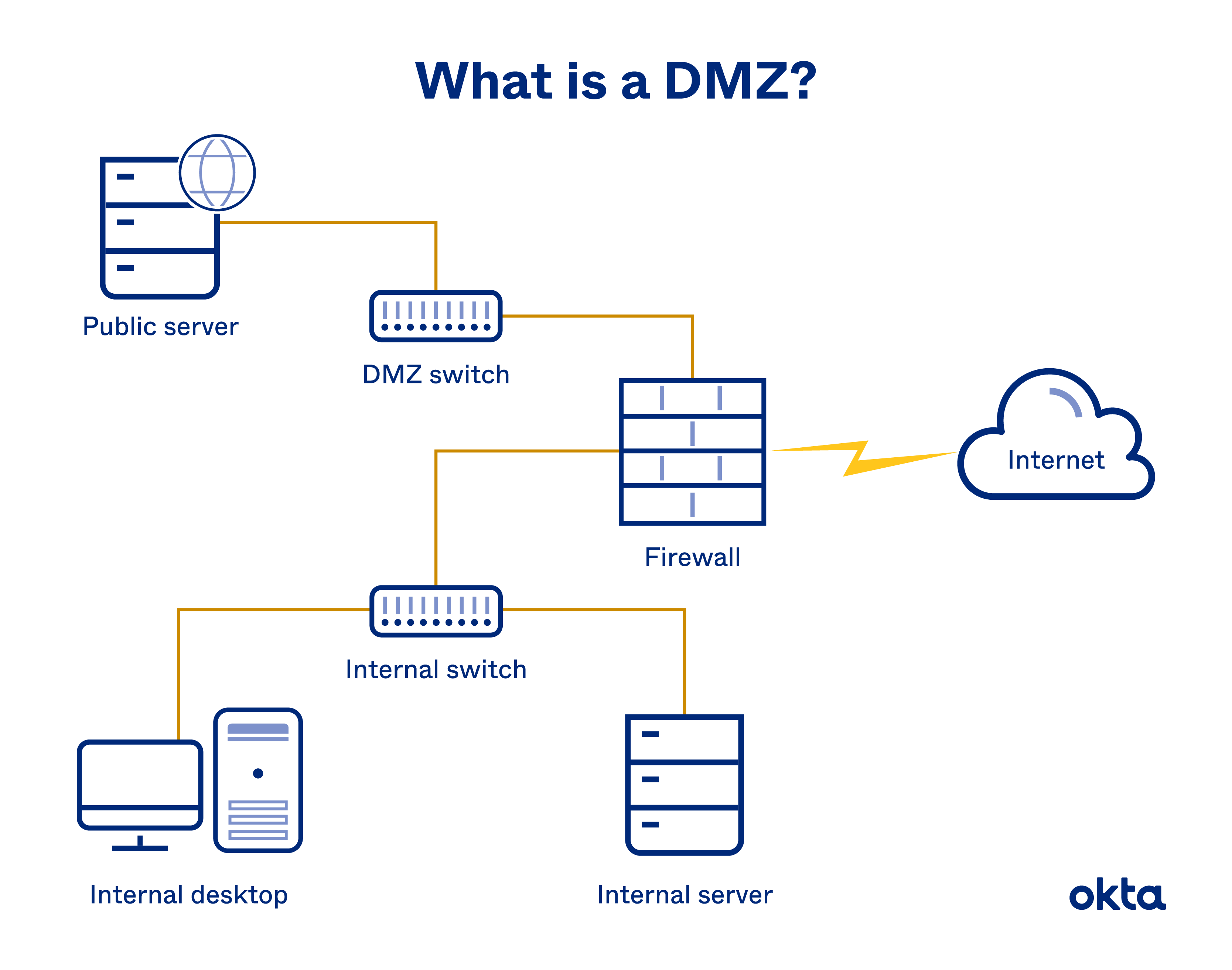
Sample DMZ Networks
Any network configured with a DMZ needs a firewall to separate public-facing functions from private-only files. But developers have two main configurations to choose from.
Single Firewall DMZ Network
This configuration is made up of three key elements.
- Firewall: Any external traffic must hit the firewall first.
- Switches: A DMZ switch diverts traffic to a public server. An internal switch diverts traffic to an internal server.
- Servers: A public and private version is required.
Configure your network like this, and your firewall is the single item protecting your network. Switches ensure that traffic moves to the right space.
A single firewall with three available network interfaces is enough to create this form of DMZ. But you’ll need to create multiple sets of rules, so you can monitor and direct traffic inside and around your network.
Dual Firewall DMZ Network
Is a single layer of protection enough for your company? If not, a dual system might be a better choice. It consists of these elements:
- Firewalls: Public traffic moves through just one layer of security. But to tap into more sensitive files, users must move past a second firewall.
- DMZ: Public resources reside in this area, and they can be accessed after moving through the first firewall.
- LAN: Private resources exist here, and they can only be accessed after moving through the second firewall.
Set up your front-end or perimeter firewall to handle traffic for the DMZ. Set up your internal firewall to allow users to move from the DMZ into private company files.
Other Setup Options
Companies even more concerned about security can use a classified militarized zone (CMZ) to house information about the local area network. Choose this option, and most of your web servers will sit within the CMZ.
Who Uses a Network DMZ?
A firewall doesn’t provide perfect protection. Hackers often discuss how long it takes them to move past a company’s security systems, and often, their responses are disconcerting. But a DMZ provides a layer of protection that could keep valuable resources safe.
Companies often place these services within a DMZ:
- Email servers: Users need internet access to send and receive email messages. But those documents can be extremely sensitive, and when hackers get them, they can sell the data on the dark web or ask for ransom.
An email provider found this out the hard way in 2020 when data from 600,000 users was stolen from them and sold. Place your server within the DMZ for functionality, but keep the database behind your firewall.
- FTP servers: Moving and hosting content on your website is easier with an FTP. But this functionality comes with extreme security risks. Allow for access and use within the DMZ, but keep your servers behind your firewall.
- Web servers: Obviously, you need to allow traffic into and out of your
company to access the web. Keep the server within the DMZ, but shield the database behind your firewall for added protection. A breach of your website can be extremely hard to detect.For example, one company didn’t find out they’d been breached for almost two years until a server ran out of disc space. A DMZ network makes this less likely.
In general, any company that has sensitive information sitting on a company server, and that needs to provide public access to the internet, can use a DMZ. In fact, some companies are legally required to do so.
For example, some companies within the health care space must prove compliance with the Health Insurance Portability and Accountability Act. They must build systems to protect sensitive data, and they must report any breach. Building a DMZ network helps them to reduce risk while demonstrating their commitment to privacy.
Benefits & Vulnerabilities of DMZ Servers
Network administrators face a dizzying number of configuration options, and researching each one can be exhausting. Understanding the risks and benefits can help you decide whether to learn more about this technique or let it pass you by.
DMZ server benefits include:
- Potential savings. On average, it takes 280 days to spot and fix a data breach. During that time, losses could be catastrophic. Set up your DMZ server with plenty of alerts, and you’ll get notified of a breach attempt.
You’ll also set up plenty of hurdles for hackers to cross. You could prevent, or at least slow, a hacker’s entrance.
- Continued access. Traffic must flow into and out of your company. A tightly controlled system doesn’t allow that movement. A DMZ network allows people to do their work while you protect security.
- Relative simplicity. A single-wall configuration requires few tools and very little technological know-how. You could be set up quickly.
DMZ server drawbacks include:
- No internal protections. Your employees and authorized users will still tap into the very sensitive data you store for your company.
- A false sense of security. Every day, hackers come up with new and nefarious ideas about slipping past security systems. Even DMZ network servers aren’t always safe. You must still monitor the environment, even when your build is complete.
- Wasted time. Some experts claim that the cloud has made the DMZ network obsolete. If you don’t have network servers, you may not have anything to protect.
Only you can decide if the configuration is right for you and your company. But know that plenty of people do choose to implement this solution to keep sensitive files safe.
Work With Okta
If you’re struggling to balance access and security, creating a DMZ network could be an ideal solution. By housing public-facing servers within a space protected by firewalls, you’ll allow critical work to continue while offering added protection to sensitive files and workflows.
If you need extra protection for on-prem resources, learn how Okta Access Gateway can help.
References
Cyber Crime: Number of Breaches and Records Exposed 2005-2020. (October 2020). Statista.
As a Hacker, How Long Would It Take to Hack a Firewall? Quora.
Company Discovered It Was Hacked After a Server Ran Out of Free Space. (November 2019). ZD Net.
Email Provider Got Hacked, Data of 600,000 Users Now Sold on the Dark Web. (April 2020). ZD Net.
FTP Remains a Security Breach in the Making. (July 2014). TechRepublic.
Cost of a Data Breach Report 2020. IBM Security.















![Toni Kroos là ai? [ sự thật về tiểu sử đầy đủ Toni Kroos ]](https://evbn.org/wp-content/uploads/New-Project-6635-1671934592.jpg)


