Azure Networking | Introduction to Azure Virtual Network 2022
Overview of Azure | Getting Familiar with IP Addressing | Azure Virtual Network (VNet) | Azure Network Security | Azure Network Models | Conclusion
Azure Networking is a communication protocol for connecting multiple resources via the Internet. Microsoft provides various services and tools under Azure that make your network strong and easy to manage. This blog will cover the basics of networking concepts and an overview of Azure networking architecture with the following topics.
Mục Lục
Overview of Azure
Azure is the name of the cloud computing service owned by Microsoft that provides Infrastructure as a Service (IaaS), Platform as a Service (Paas) and Software as a Service (SaaS). Azure’s cloud computing services are network, storage, compute, database, analytics, security, and many more. In this blog, we will only focus on the basics of network services.
What Is Azure Virtual Network?
An Azure Virtual Network (VNet) may be a network or environment which will be wont to run VMs and applications within the cloud.
When it’s created, the services and Virtual Machines within the Azure network interact securely with one another.
Advantages of Using Azure Virtual Network
Some of the foremost advantages of using Microsoft Azure VNet are as follows:
- It provides an isolated environment for your applications
- A subnet in a very VNet can access the general public internet by default
- We can easily direct traffic from resources
- It is a highly secure network
- It has high network connectivity
- It builds sophisticated network topologies in a very simple manner
Moving on, let’s have a glance at the components of Azure VNet.
Elements of Azure Virtual Network
Azure networking components provide a large range of functionalities that may help companies build efficient cloud applications that meet their requirements.
The components of Azure Networking are listed below, and we have explained each of those components in an exceedingly detailed manner:
- Subnets
- Routing
- Network Security Groups
Subnets
Subnets let users segment the virtual network into one or more sub-networks.
These sub-networks may be separated logically, and every subnet consists of a server.
We can further divide a subnet into two types:
- Private – Instances can access the web with NAT (Network Address Translation) gateway that’s present within the public subnet.
- Public – Instances can directly access the net.
Routing
- It delivers the information by choosing an appropriate path from source to destination.
- For each subnet, the virtual network automatically routes traffic and creates a routing table.
Network Security Groups
- It is a firewall that protects the virtual machine by limiting network traffic.
- It restricts inbound and outbound network traffic depending upon the destination IP addresses, port, and protocol.
How to Launch an Instance using Azure VNet?
- First, create a virtual network within the Azure cloud
- Next, create subnets into each virtual network
- Now, assign each subnet with the respective instance or Virtual Machine
- After which you’ll connect the instance to a relevant Network Security Group
- Finally, configure the properties within the network security and set policies
- As a result, you’ll be able to launch your instance on Azure
Moving forward, we’ll see an indication on creating an Azure virtual machine and virtual network step-by-step.
Demo: Step-By-Step Demo of Creating Azure Virtual Machine and Virtual Network
Step 1 − First, log into your Azure Management Portal, select ‘New’ at the underside left corner.
Step 2 − Next, on the Network Services visit Virtual Network -> Quick create.
Step 3 – Now, enter the name and leave all other fields empty and click on ‘next’.
Step 4 − Finally, click on ‘Create a Virtual Network,’ and it’s done.
Note: Now, within the same VNet, create a Virtual machine
Step 5 – First, select ‘create’ to create a replacement Virtual Machine with Windows Server 2012 R2 Datacenter.
Step 6 – Once the fields are entered, select the present resource group that you just had created for the virtual network and choose OK.
Step 7 – Now, choose a desired size and configuration by selecting DS1_V2 Standard type
Note: By default, we might choose a Virtual Network.
Step 8 – Now select the subnet as FrontEndSubnet and don’t change the general public IP address. Also, keep the Network Security Group as none.
Step 9 – Create a brand new availability set and set a replacement name thereto.
Next, set the fault domains as 2 and so disable the Guest OS Diagnosis section.
Step 10 – Finally, click and choose ‘create’.
Congratulations, you’ve got successfully created a VM.
This is all the fundamental information you wish to grasp about Microsoft Azure Virtual Network.
Getting Familiar with IP Addressing
Before understanding IP Address, we need to learn the binary numbers. If you are not familiar with binary and decimal conversion, look at the brief explanation below.
In the decimal number system, the combinations are made using only the numbers from 0 to 9. In other words, it is the number system with a base of 10 (0 to 9). Similarly, in the Binary Number System base of 2 (0 and 1) is used. Each value in a binary number is made with 2N (‘N’ is the place value that increases from right to left). The below table shows the basic conversion between binary and decimal.
Binary
Conversion
Decimal
000
0x22+0x21+0x20
0
001
0x22+0x21+1×20
1
010
0x22+1×21+0x20
2
011
0x22+1×21+1×20
3
100
1×22+0x21+0x20
4
101
1×22+0x21+1×20
5
Also Check: ARM Template.
What is IP Address?
IANA is the Internet Assigned Numbers Authority that manages and assigns the IP address in the world. IP Address identifies each device on a network uniquely. There are currently two IP Adress that is IPv4 and IPv6. An IPv4 address contains a total of 32 binary bits divided into 4 equal octets (8-bit block), whereas IPv6 is written in hexadecimal notation, separated into 8 groups of 16 bits by the colons, thus (8 x 16 = 128) bits in total. We will focus on IPv4 as it is the most used. Each octet of an IP Address is separated by a decimal and ranges from 0 to 255. You will clearly understand the binary number, octets, and IP address formation in the below table.
IP Address
Octet 1
Octet 2
Octet 3
Octet 4
10.2.7.4
00001010
00000010
00000111
00000100
192.124.249.161
11000000
01111100
11111001
10100001
255.255.140.40
11111111
11111111
10001100
00101000
There are two different IP address one is private, and the other is public.
- Private IP is accessed only within a network like a simple school network with a LAN connection.
- Public IP is accessed globally via the Internet.
The table below shows the Private IP address range assigned by IANA, and the rest are all Public IP address.
Private IP Range
10.0.0.1 – 10.255.255.255
172.16.0.0 – 172.31.255.255
192.168.0.0 – 192.168.255.255
Check Out: Azure Service Bus Pricing.
What is IP Subnetting?
Subnetting is the process of dividing a network into many smaller networks. There are 5 classes of IP address and each with a unique purpose. Only the first octet is used for dividing an IP Address into different classes. The table below shows the range of IP address of the 5 classes.
Class
Octet 1 Range (in Binary)
Octet 1 Range (in Decimal)
Class A
00000000-01111111
0-126
Class B
10000000-10111111
128-191
Class C
11000000-11011111
192-223
Class D
11100000-11101111
224-239
Class E
11110000-11110111
240-255
Class D is reserved for multitasking and broadcasting purpose, whereas Class E is reserved for research and development. So both these classes are reserved and can not be used. The below table shows the range of the first octet in an IP address with each class.
Note: The IP address with the first octet as 127 (in decimal) is a loopback address to check the network and address of the machine itself.
An IP address can further be divided into small networks depending on the use and purpose. The above classes are not sufficient for real-life use. Only 5 classes can not hold all the hosts on the same network, and the loss of IP address will be huge. So, the CIDR method was introduced.
CIDR (Classless Inter-Domain Routing)
CIDR is a method for allocating IP Address. Using this method, we can apply a subnet mask to an IP Address. This mask defines the number of bits used as a network, and the host will use the other bits that left. To understand CIDR better, we will decode a simple IP address with a subnet mask.
Suppose 192.168.1.30/28 is an IP address with 28 as the subnet mask. By comparing with IP address classes in the above table, this IP comes under Class C. Now, 24 bits are made of 3 octets, so the network will take four extra bits from the next octet to complete 28 bits. Using 2N(‘N’ is the number of borrowed bits from the host), a total of 16 subnets is formed. After taking the four bits, the last octet is left with only 4 bits that a host will use. Using 2H(‘H’ is the number of host bits left), each subnet will contain a block of 16 IP address. The first and last IP is reserved for network and broadcast in each subnet, so the total number of hosts will be 2H-2(‘H’ is the number of host bits) equals 14.
Although a total of 16 subnets or network are possible for this example, the table below listed the initial 4 subnets that can be formed using 28 as the subnet mask. Each subnet contains a total of 16 IP address, and the number of hosts will be 14 as the other two are reserved for network and broadcast.
After comparing the IP given in the example that is 192.168.1.30/28 with the table below, it is clearly visible that it belongs to the second subnet ranging from 192.168.1.16 to 192.168.1.31.
Note: Every subnet’s first and last address is not allocated to any host as it is reserved for network and broadcast.
SubNet
Total IP
Network IP
Broadcast IP
Range of Hosts
Total Hosts
1
16
192.168.1.0
192.168.1.15
192.168.1.1-192.168.1.14
14
2
16
192.168.1.16
192.168.1.31
192.168.1.17-192.168.1.30
14
3
16
192.168.1.32
192.168.1.47
192.168.1.33-192.168.1.46
14
4
16
192.168.1.48
192.168.1.65
192.168.1.49-192.168.1.64
14
Check Out: Azure Bastion.
IP Address in Azure
The two different types of IP Address used and allocated in Azure are Public IP and Private IP.
- Private – The Private IP address allows communication of resources within the azure resource group. In other words, resources can not access a private IP outside the network. The resources that can be connected using a private address are VM Network Interface, ILB (Internal Load Balancer) and Application Gateway.
- Public – The Public IP address allows Azure Resources to communicate with public-facing Azure services via the Internet. In other words, resources can access public IP outside the network. Some resources that can be connected using public address are VM Network Interface, Public Facing ILB, Application Gateway, VPN Gateway and Azure Firewall.
IP Allocation
- Dynamic IP – The default allocation method by which Azure can automatically assign the available and unreserved IP address from the subnet’s address range. Also, the Dynamic IP is not fixed and changes with time.
- Static IP – This is the custom allocation method to assign the available and unreserved IP address from the subnet’s address range. The Static IP is fixed and does not vary with time.
Also Read: Azure Load Balancer.
Azure Virtual Network
Azure Network is the interlinking and communication of all the Azure Resources in an organization. Networking leads to efficient resource work with better consistency and coordination.
Virtual Networking is the communication between devices, servers, virtual machines over the internet. Similarly, Azure Virtual Network (VNet) is a private network with interconnected Azure Resources like Azure Virtual Machines, Infrastructure and Network. It enables communication between various Azure Resources via the Internet. In a Virtual Network, a continuous block of IP Address is used to create multiple subnet networks.
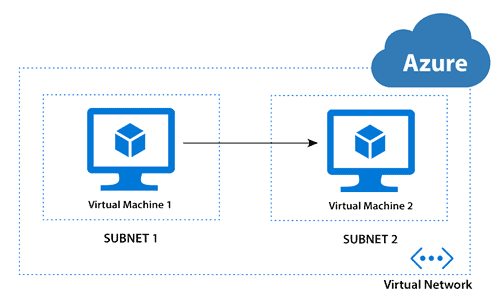
Azure Subnet
As we know, the subnet is a part of a network that covers a range of IP Address. In Azure, VNet can be divided into smaller subnets for organizations. When a VNet is created in Azure, the subnet range and topology needs to be specified. In Subnet, the IP Address range will be a subpart from a big block of IP Address used in Virtual Network (VNet). The Virtual Machines and resources in a network will be assigned the IP Address from these subnets.
Azure Network Interface
In Azure, NIC is virtual ethernet cards that help communicate the Virtual Machines present in a network. When a Virtual Machine is created in Azure, the NIC with default settings is automatically created. Also, Network Interface settings in Azure can be customized using command tools like Azure CLI and PowerShell.
Network Security
Azure provides various protection methods for securing a service in a network. I have listed down some of the basic network security tools with a short description.
Network Security Group (NSG)
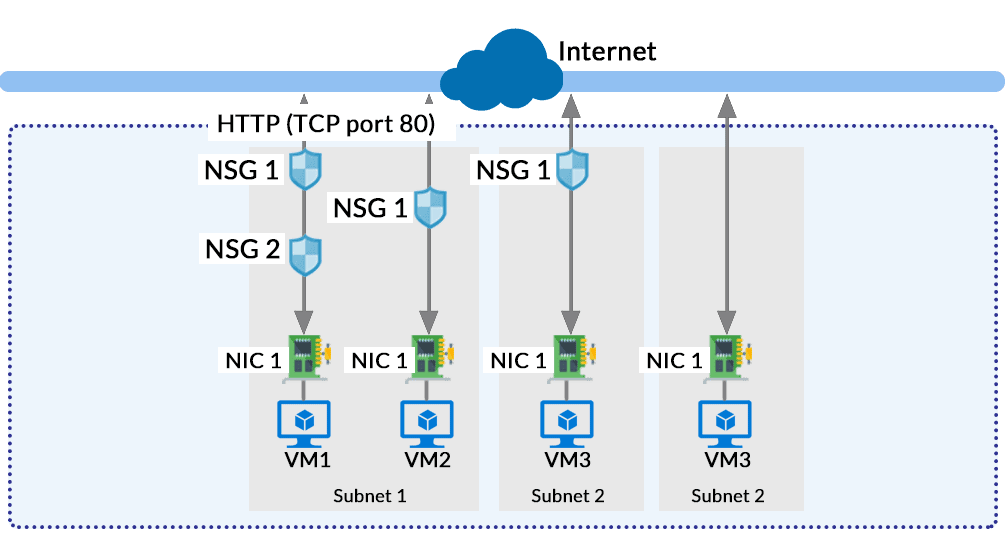
The Network Security Group in Azure acts like a firewall at the network level. It filters the traffic passing through Azure Resources in a virtual network. NSG is a group of security rules that defines the priority, source or destination, protocol, direction, port range and action. Using these rules, NSG allows or deny inbound and outbound traffic. The rules for entering traffic inside a resource is also called ‘Ingress‘, and the rules for exiting the traffic or going out of the resource is called ‘Egress‘. When all the rules are created, the NSG can be used in a Virtual Machine that will interact with a network.
Service Endpoints
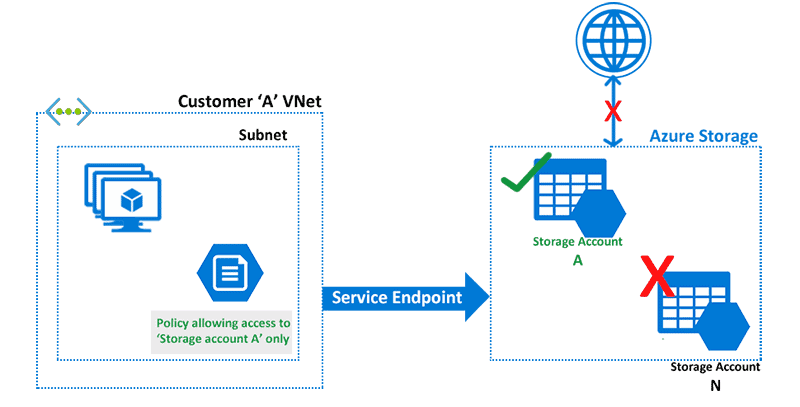
Service Endpoints in Azure provides secure connectivity over the optimized route of the Azure Network. Without needing a public IP address, Service Endpoints allows Private IP address in a VNet to reach the endpoint of an Azure Service. It is simple to set up and improves security for the Azure resources in a network. The services here can be Azure Storage, Azure Database, etc.
Web Application Firewall (WAF)
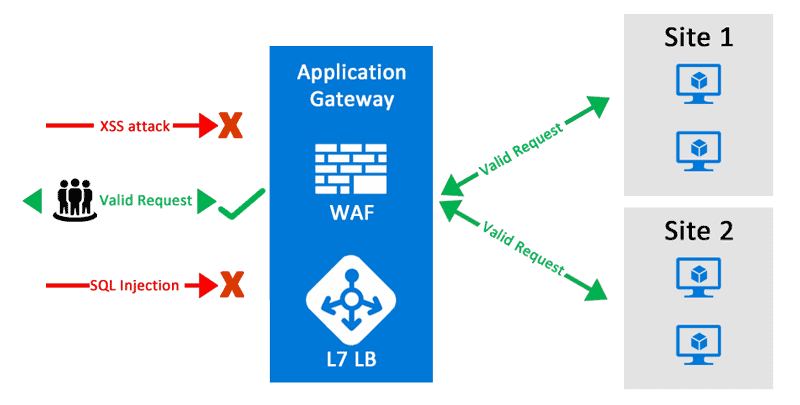
Web applications are a common target for hackers to steal user information. So, protection from the most common attacks like SQL injection, cross-site scripting, etc., is a must. Web Application Firewall by Azure is a firewall for protecting the web application from these common threats. It provides an easy setup for applying various protection of layers that results in better security management. A user can deploy the WAF with other services like Azure Application Gateway, Azure Content Delivery Network (CDN) and Azure Front Door.
Azure Network Models
Network Models are the representation and methods of connecting multiple networks. In Azure also, Microsoft enables some ways to connect multiple networks. I have listed down some of the most used network models.
VNet Peering
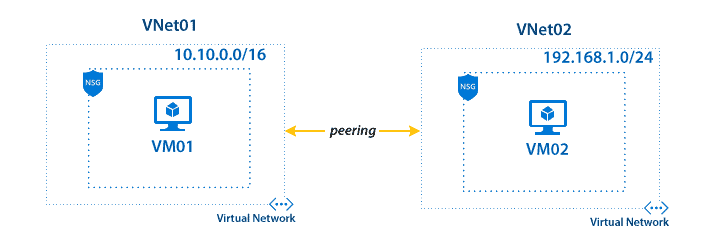
Virtual Network peering enables to connect the two or more Virtual Networks in Azure. It also allows transferring data between deployment models, Azure Subscriptions, Azure Active Directory Tenants and Azure regions without downtime and failure. The traffic between the peered virtual networks use Microsoft’s backbone infrastructure and is routed through a private network. Thus, gateways, encryption and public internet are not required.
There are two types of Virtual Network Peering:
- Regional VNet Peering – When the two networks needed to peer are in the same region, the peering is called Regional VNet Peering.
- Global VNet Peering – When the two networks are from different regions, the peering is called Global VNet Peering.
See More: VNet Peering in Azure
Virtual WAN (Wide Area Network)
Virtual WAN in Azure allows creating a web of multiple networks that are interconnected to each other. It brings multiple networking, security, and routing functionalities together to provide a new single operational interface.
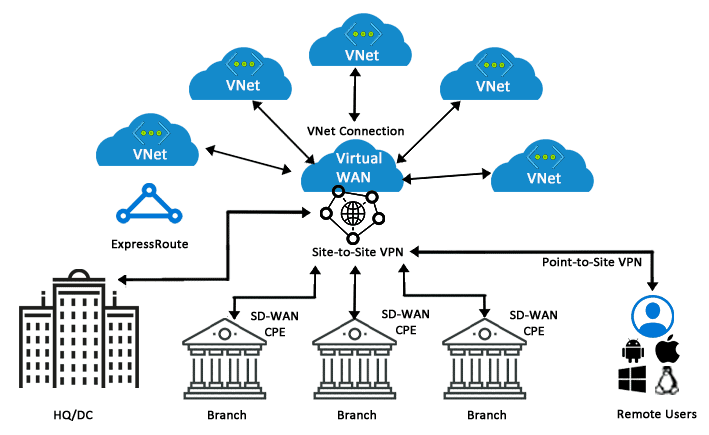
In the above diagram, a Virtual WAN at the centre acts as a single operational hub to manage all the traffic coming from multiple resources in a VNet. Instead of contacting the multiple branches separately, a VNet can contact the central hub to connect with all the branches connected to it.
More Azure Virtual Network Information
Pricing
There is no charge for using Azure VNet; it’s freed from cost. Standard charges are applicable for resources, like Virtual Machines (VMs) and other products. to be told more, see VNet pricing and the Azure pricing calculator
Protecting Resources
Network security may well be defined because the process of protecting resources from unauthorized access or attack by applying controls to network traffic. The goal is to confirm that only legitimate traffic is allowed. Azure includes a sturdy networking infrastructure to support your application and repair connectivity requirements. Network connectivity is feasible between resources located in Azure, between on-premises and Azure hosted resources, and to and from the net and Azure.
Conclusion
Azure Networking allows secure communication between multiple resources in a network. From this blog, we understand the IP Address and created a subnet mask using the CIDR method. Also, we covered the basic Azure Networking topics like VNet (Virtual Network), Azure Subnet, Azure Network Interface, Network Security Group (NSG), Service Endpoints, Web Application Firewall (WAF), VNet Peering and Virtual WAN.
We only covered the basic terminology in Azure Networking. If you want to learn more about Azure Networking and get your Hands-on Azure, please check our Microsoft Certified Azure Solutions Architect course. It covers all the basic and expert-level knowledge in Azure and helps you to become a certified Solutions Architect in Azure.
FAQs
Q1. Can I modify Vnet after I created them?
Yes. you’ll be able to add, remove, and modify the CIDR blocks utilized by a VNet.
Q2. Can I perform WAN optimization between VNets or a VNet and my on-premises data center?
Yes. you’ll be able to deploy a WAN optimization network virtual appliance from several vendors through the Azure Marketplace.
Q3. What tools do i exploit to make a VNet?
You can use the subsequent tools to make or configure a VNet:
- Azure portal
- PowerShell
- Azure CLI
- A network configuration file (netcfg – for traditional VNets only). See the Configure a VNet employing a network configuration file article
Q4. What address ranges am i able to use in my VNets?
We recommend that you simply use the address ranges enumerated in RFC 1918, which are put aside by the IETF for personal, non-routable address spaces:
10.0.0.0 – 10.255.255.255 (10/8 prefix)
172.16.0.0 – 172.31.255.255 (172.16/12 prefix)
192.168.0.0 – 192.168.255.255 (192.168/16 prefix)
You can also deploy the Shared Address space reserved in RFC 6598, which is treated as Private IP Address space in Azure:
100.64.0.0 – 100.127.255.255 (100.64/10 prefix)
Other address spaces, including all other IETF-recognized private, non-routable address spaces, may go but may have undesirable side effects.
In addition, you can’t add the subsequent address ranges:
224.0.0.0/4 (Multicast)
255.255.255.255/32 (Broadcast)
127.0.0.0/8 (Loopback)
169.254.0.0/16 (Link-local)
168.63.129.16/32 (Internal DNS)
Q5. Can I have public IP addresses in my VNets?
Yes. For more information about public IP address ranges, see Create a virtual network. Public IP addresses aren’t directly accessible from the net.
Q6. Is there a limit to the amount of subnets in my VNet?
Yes. See Azure limits for details. Subnet address spaces cannot overlap each other.
Q7. Are there any restrictions on using IP addresses within these subnets?
Yes. Azure reserves the primary four and last IP address for a complete of 5 IP addresses within each subnet.
For example, the IP address range of 192.168.1.0/24 has the subsequent reserved addresses:
- 192.168.1.0 : Network address
- 192.168.1.1 : Reserved by Azure for the default gateway
- 192.168.1.2, 192.168.1.3 : Reserved by Azure to map the Azure DNS IPs to the VNet space
- 192.168.1.255 : Network broadcast address.
Q8. How small and the way large can VNets and subnets be?
The smallest supported IPv4 subnet is /29, and therefore the largest is /2 (using CIDR subnet definitions). IPv6 subnets must be exactly /64 in size.
Q9. Can I bring my VLANs to Azure using VNets?
No. VNets are Layer-3 overlays. Azure doesn’t support any Layer-2 semantics.
Q10. Can I peer a VNet to 2 different VNets with the ‘Use Remote Gateway’ option enabled on both the peerings?
No. you’ll only enable the ‘Use Remote Gateway’ option on one peering to at least one of the VNets.
Q11. What would be the behavior after I apply both NSG and UDR at subnet?
For inbound traffic, NSG inbound rules are processed. For outbound, NSG outbound rules are processed followed by UDR rules.
Q12. How much do VNet peering links cost?
There is no charge for creating a VNet peering connection. Data transfer across peering connections is charged
Q13. Do VNets support multicast or broadcast?
No. Multicast and broadcast aren’t supported.
Q14. Can I ping default gateway within a VNet?
No. Azure provided default gateway doesn’t respond ping. But you’ll be able to use ping in your VNets to test connectivity and troubleshooting between VMs.
Q15. Can I use tracert to diagnose connectivity?
Yes.
Q16. Can I add subnets after the VNet is created?
Yes. Subnets are often added to VNets at any time as long because the subnet address range isn’t a part of another subnet and there’s available space left within the virtual network’s address range.
Q17. Can I modify the scale of my subnet after I create it?
Yes. you’ll be able to add, remove, expand, or shrink a subnet if there aren’t any VMs or services deployed within it.
Q18. Do VNets support IPv6?
Yes, VNets is IPv4-only or dual stack (IPv4+IPv6). For details, see Overview of IPv6 for Azure Virtual Networks.
Q19. Can a VNet span regions?
No. A VNet is restricted to one region. A virtual network does, however, span availability zones. to find out more about availability zones, see Availability zones overview. you’ll be able to connect virtual networks in several regions with virtual network peering. For details, see Virtual network peering overview
Q20. Can I connect a VNet to a different VNet in Azure?
Yes. you’ll connect one VNet to a different VNet using either: Virtual network peering
Q21. What are my DNS options for VNets?
Use the choice table on the Name Resolution for VMs and Role Instances page to guide you thru all the DNS options available.
Q22. Can I specify DNS servers for a VNet?
Yes. you’ll specify DNS server IP addresses within the VNet settings. The setting is applied because the default DNS server(s) for all VMs within the VNet.
Q23. How many DNS servers am i able to specify?
Reference Azure limits.
Q24. Can I modify my DNS servers after i’ve got created the network?
Yes. you’ll change the DNS server list for your VNet at any time. If you modify your DNS server list, you wish to perform a DHCP lease renewal on all affected VMs within the VNet, for the new DNS settings to require effect. For VMs running Windows OS you’ll be able to try this by typing ipconfig /renew directly on the VM. For other OS types, confer with the DHCP lease renewal documentation for the precise OS type.
Q25. What is Azure-provided DNS and does it work with VNets?
Azure-provided DNS could be a multi-tenant DNS service offered by Microsoft. Azure registers all of your VMs and cloud service role instances during this service. This service provides name resolution by hostname for VMs and role instances contained within the identical cloud service, and by FQDN for VMs and role instances within the same VNet. to be told more about DNS, see Name Resolution for VMs and Cloud Services role instances.
There is a limitation to the primary 100 cloud services during a VNet for cross-tenant name resolution using Azure-provided DNS. If you’re using your own DNS server, this limitation doesn’t apply.
Q26. Can I override my DNS settings on a per-VM or cloud service basis?
Yes. you’ll set DNS servers per VM or cloud service to override the default network settings. However, it’s recommended that you simply use network-wide DNS the maximum amount as possible.
Q27. Can I bring my very own DNS suffix?
No. you can’t specify a custom DNS suffix for your VNets.
Q28. Can I connect a virtual machine scale set to a VNet?
Yes. you want to connect a virtual machine scale set to a VNet.
Q29. Is there a whole list of Azure services which will I deploy resources from into a VNet?
Yes, For details, see Virtual network integration for Azure services.
Q30. Can I move my services in and out of VNets?
No. you can not move services in and out of VNets. to maneuver a resource to a different VNet, you have got to delete and redeploy the resource.
Q31. What is the safety model for VNets?
VNets are isolated from each other, and other services hosted within the Azure infrastructure. A VNet could be a trust boundary.
Q32. Can I restrict inbound or outbound traffic flow to VNet-connected resources?
Yes. you’ll be able to apply Network Security Groups to individual subnets within a VNet, NICs attached to a VNet, or both.
Q33. Can I implement a firewall between VNet-connected resources?
Yes. you’ll be able to deploy a firewall network virtual appliance from several vendors through the Azure Marketplace.
Q34. Is there information available about securing VNets?
Yes. For details, see Azure Network Security Overview.
Q35. Do Virtual Networks store customer data?
No. Virtual Networks doesn’t store any customer data.
Q36. Can I peer my VNet with a VNet during a different subscription?
Yes. you’ll peer VNets across subscriptions and across regions.
References
Next Task For You
Begin your journey towards becoming a Microsoft Azure Solutions Architect Expert. Just click on the register now button below to register for a Free Class on Microsoft Azure Solutions Architect Expert Certification [AZ-305], which will help you to understand better, so you can choose the right path and clear the certification exam.
















![Toni Kroos là ai? [ sự thật về tiểu sử đầy đủ Toni Kroos ]](https://evbn.org/wp-content/uploads/New-Project-6635-1671934592.jpg)


