Advantages and Disadvantages of Cyber Security – javatpoint
← prev
Mục Lục
Advantages and Disadvantages of Cyber Security
Cyber Security is the combination of two words, cyber + security, where cyber refers to the internet and security means the protection of cyber. The human personal, professional, social, and working space is ruled and controlled by the internet. Being surrounded by the internet makes its growth a never-ending era because it has become essential to the day-to-day human lifestyle. Now we can’t even imagine our life without the internet, and the advancement of technologies is making it fast and easy.

The COVID-19 pandemic has proven the vital role of the internet, as 90% of the work has been conducted from home with the use of the internet. Various software applications and browsers work while the system is connected to the internet, not only for communication but even for storing a large amount of data the internet is used. For example, Emails, cloud storage (including Microsoft one drive, IDrive, Dropbox, Next cloud, Tresorit), Google Drive, etc. With this storage facility, we should only write down and remember some things; we can rely on the system for every detail. But this ease of information always comes with a risk of leaking confidential, personal, and professional information that takes humans to the stage of compromise. To deal with this situation, cyber security has started its role.
Cyber security is the assurance of confidentiality, integrity, and authentication of information or data, network, and system connected to the internet. Cyber security protection layers enhance cyberspace security, speed up cyber data, and improve cyber resilience and information protection for businesses and individual users. This protection shield defends networks, servers, electronic systems, computers, data, mobile devices, and communication from malicious attacks. Cyber security is categorized in various contexts, including operational security, end-user education, information security, disaster recovery, business continuity, operational security, application security, and network security.
Cyber security protects our digital assets and safeguards companies’ information and system against theft and other harms that rely on computers, the internet, and websites. Cyber security deals with cybercrime, cyber terrorism, botnets, adware, denial-of-services, Man-in-middle attack, SQL injection, Trojans, malware, and another kind of cyber threats too. To maintain and identify potential threats and valuable data in cyber security, cyber security experts are appointed that find, test, and repair weaknesses in a company’s infrastructure.
Some of the important principles of cyber security:
All the cyber security principles are grouped under governing, detecting, protecting, and responding to activity, and these principles are:
- It secure configuration
- Provide network security
- Manage user privileges
- User education and awareness
- Monitoring
- Malware prevention
- Incident management
- Home and mobile working
- Removable media controls
- Acceptance of security breaches
- Open design
- Fail-safe defaults
- Work factor
- Economy of mechanism
- Complete mediation

Advantages of the cyber security
Cyber security has numerous advantages in industries and daily professional and personal life. We all enjoy these kinds of benefits:

a) Data safety from hackers
Cyber security is designed to reduce the chance of data breaches against criminals. It uses tools and techniques like the DLP technique in conjunction with firewalls, web servers, and access control methods for protection. It also restricts resource access based on user tasks and powers or network connections.
b) Reduces computer crash
While working with technology, the user must deal with various harmful attacks that may result in freezing screens and computer crashes. This can bring the work life of people working with tight deadlines at risk. These kinds of problems can be diminished by cyber security and lower the hindrance of working with technology.
c) Decreased data theft hazard
The major benefit of cyber security is that it prevents unauthorized or malicious user access to the system. The high-security protocol is implemented to protect against major data theft and makes the experience a lot more relieving.
d) System availability and improved data
If a system is free from threats due to cyber security, it can boost the effectiveness of data and its network. It also improves the quality of data as it is less harmful.
e) Protect business reputation
Every organization’s primary strategy is to win customers’ trust, but a data breach can weaken the whole effort and bond of trust. Various examples have proved that data breaches have badly spoiled the business reputation because, after an attack, they failed to get the customer retention needed to strengthen brand loyalty. Organizations use technologies like network security and cloud security to avoid these sudden setbacks in the system and strengthen the security, which can also open new paths to future recommendations, ventures and expansions.
f) Assist remote working
Cyber securities always protect analytics, strategies, and sensitive data that risk being leaked or hacked. Rather some organizations or business uses multiple remote models for their workflows. Still, it became more popular after COVID-19, where 80% of workers worked from home with their personal or professional devices, Wi-Fi, and IoT. This result in the increase of average data breach costs that make it necessary for a business to protect its sensitive data.
g) Saves the bottom line
Cybercriminals or cyber crimes are the prime rivals of any business or individual that can suddenly take everything from bed to floor, including its sales and revenue. With low, competitive criteria, a business can’t survive its continuity. Therefore cyber security has some developed technologies that defend businesses from reaching their bottom line.
h) Cyber posture is improved
Digital protection provided by cyber security to the firms provides safety, liberty, and flexibility to the employees in freely accessing the internet. Cybersecurity technology continuously increases its safety posture by tracking all the systems with a single click. Cyber security organizations can protect and respond during and after a cyber-attack. Cyber security protocols are strengthened to prevent threats.
i) Handles data management
Losing data at the last minute due to a data breach may take the company to ground level and start all the work from scratch. To avoid this situation, the organization must constantly monitor its data and check whether data security regulations are implemented perfectly in the system. Cyber security training help in managing data and preventing access loss of money and time in the organization. Because once organizational data is lost or stolen, it takes excessive time and effort to get back on track.
j) Improve customer’s and stakeholders’ trust
If a company has a great dense mechanism against internal and external threats or malpractices, it is considered the most secure to boost stakeholders’ and investors’ trust. Cyber security makes people invest in the company without may doubt.
k) Detection and deletion of unwanted and harmful programs
Cyber security not only works on current files but also scans and detects vulnerabilities in the system, files, network, and application before installation. It detects spyware, malware, or virus in the files and immediately takes action by deleting them to remove any threat to the system.
l) Deny unwanted access from the possible threat
Cyber security shields security against the slightest threat to the system by denying unwanted access. Not only denying and saving the hazard, but cyber security also notifies about the possible threat to the user that helps them to build a stronger defensive system.
m) Recovery of the system
Any kind of disruption in the system due to malware, virus, other threats, etc., can be recovered, and stability is continuity by implementing cyber security as a savior. Without it, the result should be total disruption.
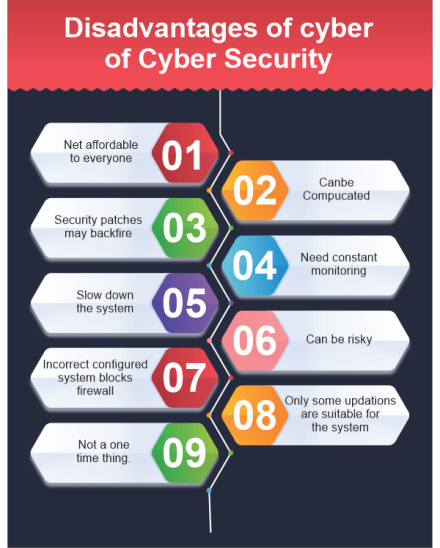
a) Not affordable to everyone
Users or businesses have to buy their services and pay for maintenance, which seems an expenditure to them. Usually, small or medium business needs more finances to protect their system and data from internal or outside cyber-attacks. They need to be aware of the advantage of using cyber security in business and invest less in cyber security. Even an individual using a system and internet couldn’t afford an antivirus or firewall for their system and doesn’t feel the need for it. Rather some free antivirus and window defender already installed in window help in prevention, but nothing is 100% secure.
b) Can be complicated
Cyber security measures are hard to understand for its user, normal persons, or business persons as they require a lot of time and effort. Suppose the user needs help understanding how to use cyber security, then instead of benefit. In that case, it can damage data loss, or hackers can easily take advantage of it. If a business doesn’t have a proper security mechanism, it can be easily trapped and attacked by hackers with various methods. Cyber security experts must break the complexity of getting through cyber security to avoid damage.
c) Security patches may backfire
To secure the system, security experts always work on designing security patches against vulnerabilities, and once they release a new security update or patch, the hackers start their work. They try to find the weakness mended in patched files by comparing the patches and unpatched files. Then unpatched files are attacked, which is why patches can backfire on the system it was meant to secure.
d) Need of constant monitoring
As we know, hackers and cybercriminals continuously work to penetrate a business network. To tackle them, businesses have to monitor their cyber security constantly. It has two benefits. One, it keeps the system up to date, finding threats before they create harm and ensuring everything is in place.
e) Slow down the system
One of the best and most dedicated security systems consists of several passwords and checks all the system files. This can consume lots of time, resulting in slow system processing and the productivity of the person working on it.
f) Can be risky
Sometimes implementing cyber security measures can be risky for individuals or businesses because they have to compromise their data. It also increases the risk of security breaches that result in loss of money, customer trust, and the company’s reputation.
g) Incorrect configured system blocks firewall
A firewall is a great cyber security tool that access can block certain services and actions of the user when it is not configured incorrectly. This situation can be reversed after the correct configuration of the firewall in the system requires the arbitration of a professional security person unfamiliar with technology can’t make it possible.
h) Only some updations are suitable for the system
It is optional that every update or version may work as per expectation after installation. Therefore, analysts must wait for some time to function or work around the system as it was intended to while complying with the security system.
i) Not a one-time thing
Cyber security requires constant monitoring and updating with regular intervals of time for its benefit because it is not designed in a few minutes. This states that cyber security is not a one-time installation process that you set and forget. It takes years of effort, study, and experimentation to make a cybersecurity program and put it into place. It needs constant attention.
Note: When using the internet, Google is the first option for everyone to start an internet search. Google has occupied our devices and has a hold on the user’s, company, or government’s confidential information as every piece of information is stored on its platform and applications. That’s why Google needs a top level of cyber security and follows a different cyber security culture. This starts form hiring an employee and by giving training and internship to them. Before hiring an employee, their background is properly checked, and their qualification, credit records, criminal records, etc., are confirmed. Every employee has to go through this process as the company wants to protect users’ data from them.
Conclusion
Living in this digital world where every area, from education to medical inquiries, from entertainment to banking, is incomplete without computers as we can do everything and anything on a digital basis in these. Woking domain (private or personal) is investing in this domain heavily across the world. But everything has some advantages and disadvantages same applies to cyber security. Cyber security is a blessing to the cyber world, but despite several advantages, sit has disadvantages too. Hackers are also system experts who plan attacks for their benefit. They can be from other countries who try to fetch confidential information about the government, defenses, or individuals for attacking the country.
Next Topic
#
← prev
next →















![Toni Kroos là ai? [ sự thật về tiểu sử đầy đủ Toni Kroos ]](https://evbn.org/wp-content/uploads/New-Project-6635-1671934592.jpg)


