What is an Azure Security Group? | Aviatrix
As you read through this article, you are going to learn the following:
Mục Lục
Azure Network Security Group
Billions of bits of data are traversing across the internet every second, and this has made the internet a global village for easy access and quick transfer of information over several interconnected networks (both public and private network).
For this reason, it is becoming harder and harder to monitor, manage and control the different kinds of internet traffic. With this rapid advancement, creating smooth communication between network devices has become a pipe dream. It’s resulting in higher demand of network devices, more cumbersome network architecture and more cost in maintaining smooth connectivity between networks and their respective endpoints.
Discussed in this Article:
- Virtual Networking Technology
- Basics of the Azure Network Security Group
- Key Functions that can be enabled by implementing Azure Virtual Network Group
Virtual networking technology
Virtual networking technology is a technology that makes it possible to control one or more remotely located computers or servers over the internet. It makes it possible to store data and retrieve data, run and operate software through a web browser as though the distant hardware were on-site.
As compared to the administration of numerous devices connected in widely separated geographical locations, Virtual networking has created a centralized control for these devices connected to a network; it mitigated the cost of setting up, managing and controlling hardware and software over a network. Made it possible for system administrators to install drivers, perform the test and solve problems on remote machines from a single location.
This technology has opened the opportunity to several tech vendors to adopt and offer comprehensive virtual networking services, allowing network administrators to outsource the labor of securely managing their networks to these vendors.
Microsoft is one example of some of these vendors that have stood out in terms of efficiency creating virtual networking tools, of which Azure Networking Security Group is one that has turned out to be one of their major contributions to network group security.
Basics of Azure Network Security Group
An azure network security group is merely a set of access control rules that can be wrapped around a virtual network or a subnet; these rules inspect inbound and outbound traffic to determine whether to allow or deny a package. The Azure network security is comprised of two layers: the VM-level and subnet level Network security group. It uses specific properties such as source and destination IP, source and destination port, priority, protocol, direction (specify if the traffic is inbound and outbound), action (determine if the packet should be allowed or denied), etc.
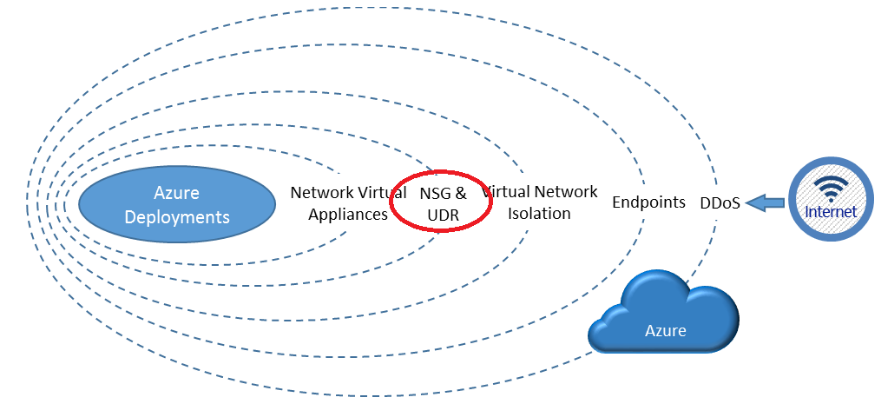
Key Functions that can be enabled by implementing Azure Virtual Network Group
This tool is user-friendly and extremely easy to implement, the tool has made it possible to perform the following function over a virtual network;
Isolate traffic between two virtual networks: Administrators can create multiple virtual networks with each Azure region. Each virtual network is isolated from others. For each virtual network you’re able to do the following.
- Specify a custom private IP
- Segment virtual network into multiple sinners and also assign a part of the virtual network’s address space to each subject.
- Specify your DNS server for use by Azure resources in the virtual network
Filter Network Traffic: They could be used to allow only specific traffic between two subnets, thereby limiting access between the two subnets. This is also known as network filtering, which can be done by either or both of the following. Security Groups and Network virtual appliances. The former allows you to filter traffic to and from resources by using source and destination IP, port and protocol, while the latter performs network functions such as firewalling, WAN optimization, etc.
Route Network Traffic: Route Network traffic between subnets, virtual networks, on-premise network, and the internet, by default. However, either of the following options can be implemented to override the default routes azure creates: Route Tables and by using Border Gateway Protocol.
Connect virtual networks: It able network administrators to connect several virtual networks, hence allowing the resources in each Virtual Network to communicate with each other using virtual peering. This connection can be achieved between resources in the same, or different Azure regions.
Communicate With On-Premise Resources: Communicate with on-premises resources to a virtual network using any of the following combinations. Point-to-site virtual private network (VPN), Site-to-site VPN and Azure ExpressRoute.
Some additional functions include Block or control traffic from the internet and communication with the internet.















![Toni Kroos là ai? [ sự thật về tiểu sử đầy đủ Toni Kroos ]](https://evbn.org/wp-content/uploads/New-Project-6635-1671934592.jpg)


