What is a DMZ Network in CCNA? – GeeksforGeeks
DMZ Network stands for the demilitarized zone it is a perimeter network that protects along with adding an extra layer of security to an organization’s internal local-area network from untrusted traffic present in the network. DMZ is a subnetwork that works between what is called private networks and public internet. A DMZ is a network barrier between trusted and untrusted networks within an organization’s private and public networks. DMZ acts as a protective layer that prevents external users from accessing company data. The DMZ receives requests for access to a company’s information and its website from external users or public networks. For this type of request, the DMZ coordinates the session over the public network. Sessions cannot start on private networks. If someone tries to do malicious activity in your DMZ, your website will break, but your other information will remain safe. The purpose of the DMZ is to provide access to untrusted networks by ensuring the security of private networks. A DMZ is not required, but we recommend using it with a firewall.
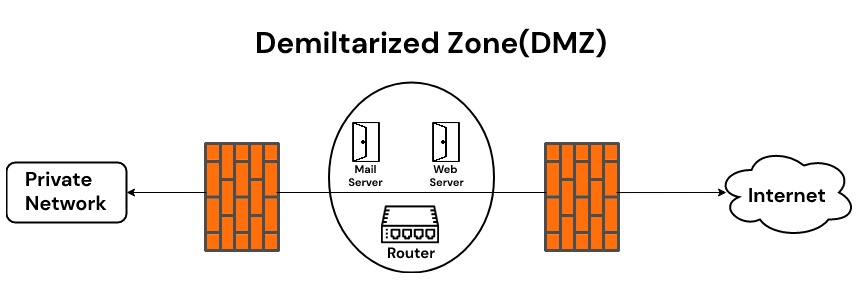
Some services of a DMZ are:
The purpose of demilitarized zones is to allow access to resources from untrusted networks while keeping the private network secure. DMZ can be used as a router, DMZ router becomes a LAN, with computers and other devices connecting to it. This ensures that the firewall in the system does not disturb the performance.
Benefits of using DMZ:
A key benefit of a DMZ is that it adds an extra layer of security to your internal network by restricting access to sensitive data and servers. DMZ allows website visitors to subscribe to certain services while providing a buffer to and from your organization’s private network.
- The primary benefit of using DMZ is a secure network connection.
- It provides access control.
- It provides protection against Internet Protocol (IP) spoofing.
Uses of DMZ:
DMZ networks are an important part of corporate network security for as long as firewalls have existed. They are used for similar reasons. Protect sensitive organizational systems and resources. DMZ networks are commonly used for:
- Reduce and control access to the systems by external users
- Host corporate resources to make them available to authorized external users.
Examples of DMZ are:
- Cloud networks: This approach is generally used when an organization’s applications run slightly on-premises and partly in a virtual network. It is further used when outbound traffic inspection is required, or when fine-grained traffic control is required between virtual networks and on-premises data centers.
- Home Services: A DMZ is also useful in home networks where computers and other devices are connected to the Internet through a broadband router and configured on a LAN. Some home routers include DMZ host functionality. This is in contrast to DMZ subnets used by organizations with more devices than they have at home. The DMZ Host role represents a device on your home network outside your firewall. This device will act as a DMZ and the rest of your home network will be behind your firewall. In some cases, game consoles are chosen as DMZ hosts to prevent firewalls from interfering with games. Consoles also tend to contain less sensitive information than PCs, making them a good choice for DMZ hosts.
- Industrial control systems: A DMZ offers a potential solution to ICS security risks. Industrial equipment such as turbines and his ICS are integrated with information technology (IT), making the manufacturing environment smarter and more efficient, but also expanding the attack surface. Many Internet-connected industrial or industrial engineering (OT) devices are not designed to handle attacks in the same way as IT devices. DMZs provide enhanced network segmentation, making it difficult for ransomware and other network threats to bridge the gap between IT systems and more vulnerable OT-enabled systems.
For further information, you can also refer to the link below:
My Personal Notes
arrow_drop_up















![Toni Kroos là ai? [ sự thật về tiểu sử đầy đủ Toni Kroos ]](https://evbn.org/wp-content/uploads/New-Project-6635-1671934592.jpg)


