Virtual Private Network (VPN) | An Introduction – GeeksforGeeks
VPN stands for the virtual private network. A virtual private network (VPN) is a technology that creates a safe and encrypted connection over a less secure network, such as the internet. A Virtual Private Network is a way to extend a private network using a public network such as the internet. The name only suggests that it is a Virtual “private network” i.e. user can be part of a local network sitting at a remote location. It makes use of tunneling protocols to establish a secure connection.
Lets understand VPN by an example:
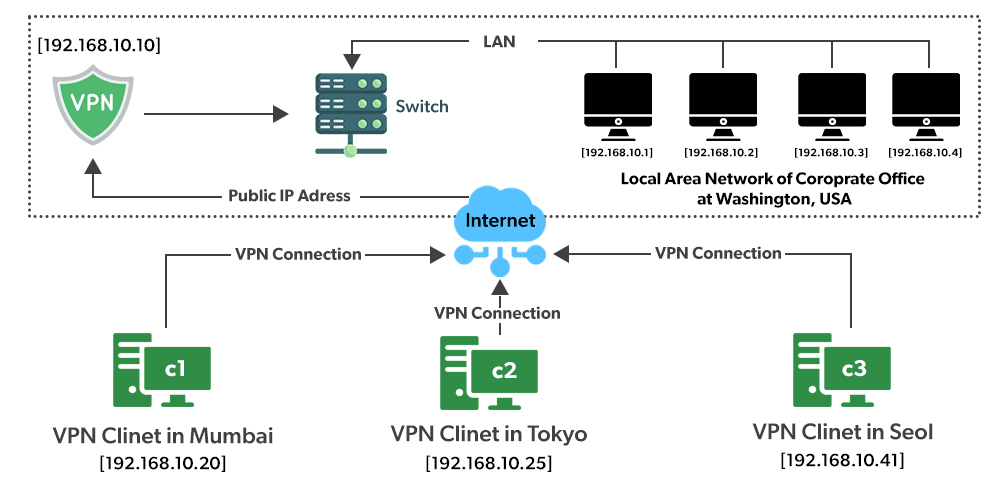
Think of a situation where corporate office of a bank is situated in Washington, USA. This office has a local network consisting of say 100 computers. Suppose other branches of the bank are in Mumbai, India, and Tokyo, Japan. The traditional method of establishing a secure connection between head office and branch was to have a leased line between the branches and head office which was a very costly as well as troublesome job. VPN lets us overcome this issue in an effective manner.
The situation is described below:
- All 100 hundred computers of the corporate office at Washington are connected to the VPN server(which is a well-configured server containing a public IP address and a switch to connect all computers present in the local network i.e. in US head office).
- The person sitting in the Mumbai office connects to The VPN server using a dial-up window and the VPN server returns an IP address that belongs to the series of IP addresses belonging to a local network of the corporate office.
- Thus person from the Mumbai branch becomes local to the head office and information can be shared securely over the public internet.
- So this is the intuitive way of extending the local network even across the geographical borders of the country.
VPN is well exploited all across the globe
We will explain to you with an example. Suppose we are using smartphones regularly. Spotify-a Swedish music app which is not active in India But we are making full use of it sitting in India. So how ?? VPN can be used to camouflage our geolocation.
- Suppose the Ip address is 101.22.23.3 which belongs to India. That’s why our device is not able to access the Spotify music app.
- But the magic begins when we used the Psiphon app which is an android app and is used to change the device IP address to the IP address of the location we want(say US where Spotify works in a seamless manner).
- The IP address is changed using VPN technology. Basically what happens is that your device will connect to a VPN server of the respective country that you have entered in your location textbox of the Psiphon app and now you will inherit a new IP from this server.
Now we typed “what is my IP address”? Amazingly the IP address changed to 45.79.66.125 which belongs to the USA And since Spotify works well in the US, so we can use it now being in India (virtually in the USA). Is not that good? obviously, it is very useful.

- VPN also ensures security by providing an encrypted tunnel between client and VPN server.
- VPN is used to bypass many blocked sites.
- VPN facilitates Anonymous browsing by hiding your ip address.
- Also, most appropriate Search engine optimization(SEO) is done by analyzing the data from VPN providers which provide country-wise stats of browsing a particular product. This method of SEO is used widely my many internet marketing managers to form new strategies.
VPN and its legality
Using VPN is legal in most of the countries,. The legality of using a VPN service depends on the country and its geopolitical relations with another country as well. A reliable and secure VPN is always legal if you are not intended to use it for any illegal activities like committing fraud online, cyber theft, or in some countries downloading copyrighted content.
China has decided to block all VPN(Virtual private network)s by next year, as per the report of Bloomberg. Many Chinese Internet users use VPNs to privately access websites that are blocked under China’s so-called “great firewall”. This is done to avoid any information leakage to rival countries and so as to tighten the information security.
This article is contributed by Shivam Shukla. If you like GeeksforGeeks and would like to contribute, you can also write an article using write.geeksforgeeks.org or mail your article to [email protected]. See your article appearing on the GeeksforGeeks main page and help other Geeks.
Please write comments if you find anything incorrect, or you want to share more information about the topic discussed above.
My Personal Notes
arrow_drop_up















![Toni Kroos là ai? [ sự thật về tiểu sử đầy đủ Toni Kroos ]](https://evbn.org/wp-content/uploads/New-Project-6635-1671934592.jpg)


