Online social networks security and privacy: comprehensive review and analysis | SpringerLink
Being the technology-based society that we are, and with the prevalence of the internet, we have extended our interaction through the electronic world of the internet. Following are the attacks which users have been observing right from the beginning of social networks.
We have divided threats into three categories i.e. conventional threats, modern threats, and targeted threats (as shown in Fig. 7). Conventional threats include threats that users have been experiencing from the beginning of the social network. Modern threats are attacks that use advanced techniques to compromise accounts of users and targeted attacks are attacks that are targeted on some particular user which can be committed by any user for varied personal vendettas.
Fig. 7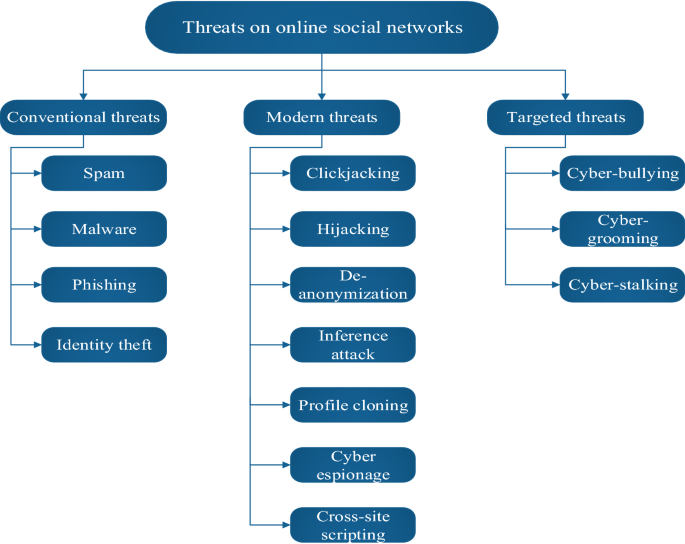
Classification of threats
Full size image
Mục Lục
Conventional threats
Spam attack
Spam is the term used for unsolicited bulk electronic messages [39]. Although email is the conventional way to spread spam, social networking platform is more successful in spreading spam [40]. The communication details of legitimate users can easily be obtained from company websites, blogs, and newsgroup [27]. It is not difficult to convince the targeted client to read spam messages and trust it to be protected [41]. Most of the spams are commercial advertisements but they can also be used to collect sensitive information from users or may contain viruses, malware or scams [28].
Malware attack
Malware is a noxious programming which is explicitly evolved to contaminate or access a computer system, ordinarily without the information of the user [42]. An intruder can utilize numerous ways to spread malware and contaminate devices and networks [43]. For instance, malware may get installed by clicking a malicious URL, on the client’s framework or it might divert the client to a phony site which endeavors to acquire private data from the client. An attacker can inject some malicious script in URLs and clicking on that URLs can make that script run on a system that may collect sensitive information from that system [44]. In social networking platforms, the malware uses Online Social Network’s (OSN) structure to propagate itself such as the number of vertices, number of edges, average shortest path, and longest path.
Phishing
A phishing attack is a kind of social engineering attack where the aggressor can acquire sensitive and confidential information like username, password and credit card details of a user through fake websites and emails which appears to be real [45]. An invader can impersonate an authentic user and may use his/her identity to send fake messages to other users via a social networking platform which contains malicious URL [46]. That URL might readdress a consumer to the phony website where it asks for personal information [47]. In the case of SNS, an assailant needs to attract the client to a phony page where he can execute a phishing attack. To accomplish this, the assailant uses different social engineering methodologies. For example, he can send a message to a user which says, “your personal pictures are shared on this website, please check!”. By clicking on that URL, the user is redirected to a fake website which looks like some legitimate social networking site.
Identity theft
In this sort of assault, the assailant utilizes someone else’s identity like social security number, mobile, number, and address, without their permission to commit attackers [48]. With the help of these details, the attacker can easily gain access to a victim’s friend list and demand confidential information from them using different social engineering techniques [49]. Since the attacker impersonates a legitimate user, he can utilize that profile in any conceivable way which could seriously affect authentic clients [50].
Modern threats
Cross-site scripting attack
Cross-site scripting is a very prevalent attack vector among infiltrators. The attack is abbreviated as XSS and is also known as “Self-XSS” [51]. Fundamentally, the attack executes a malicious JavaScript on the victim’s browser through different techniques. These are classified as persistent, reflected, and DOM-based XSS attacks [52]. The browser can be hijacked with just a single click of a button which may send a malicious script to the server [53]. This script is boomeranged back to the victim and gets executed on the browser. Attractive links and buttons in popular social media sites like Twitter and Facebook can trick the user into following URLs [54]. Worse yet, some users may feel compelled to copy and paste JavaScript containing links onto their browser’s address bar [55]. These attacks can either steal information or act as spyware. Such attacks can also hijack computers to launch attacks on unsuspecting users. The real perpetrator of the attack is hidden behind the compromised machine.
Profile cloning attack
In this attack, the assaulter clones the users’ profile about which he has a prior knowledge. The attacker can use this cloned profile either in the same or in a different social networking platform to create a trusting relationship with the real user’s friends [56]. Once the connection is established, the attacker tricks the victim’s friends to believe in the validity of the fake profile and catch confidential information successfully which is not shared in their public profiles. This attack can also be used to commit other types of cyber-crimes like cyberbullying, cyber-stalking, and blackmailing [45].
Hijacking
In hijacking, the adversary compromises or takes control of a user’s account to carry out online frauds [57]. The sites without multifactor authentication and accounts with weak passwords are more vulnerable to hijacking as passwords can be obtained through phishing [58]. If we do not have multifactor authentication, then we lack a secondary line of defense [59]. Once an account is hijacked, the hijacker can send messages, share the malicious link, and can change the account information which could harm the reputation of the user [60].
Inference attack
Inference attack infers a handler’s confidential information which the user may not want to disclose, through other statistics that is put out by the user on some Social Networking Site (SNS) [61]. It uses data mining procedures on visibly available data like the user’s friend list and network topology [62]. Using this technique, an attacker can find an organization’s secret information or a user’s geographical and educational information [45].
Sybil attack
In Sybil attack, a node claims multiple identities in a network [63]. It can be harmful to social networking platforms as they contain a huge number of users who are coupled through a peer-to-peer network [64]. Peers are the computer frameworks which are associated with one another by means of the internet and they can share records straightforwardly without the need of a central server [32]. One online entity can make several fake identities and use those identities to distribute junk information, malware or even affect the reputation and popularity of an organization. For instance, a web survey can be manipulated utilizing various Internet Protocol (IP) delivers to submit an enormous number of votes, and aggressor can outvote a genuine client [33].
Clickjacking
Clickjacking is a procedure in which the invader deceives a user to click on a page that is different from what he intended to click [65]. It is also known as User Interface redress attack. The attacker exploits the vulnerability of the browsers to perform this attack [66]. He loads another page over the page which the user wants to access, as a transparent layer [67]. The two known variations of clickjacking are likejacking and cursorjacking. The front layer shows the substance with which the client can be baited. At the point when the client taps on that content he actually taps the like button. The more individuals like the post, the more it spreads.
In cursorjacking attacker replaces the actual cursor with a custom cursor image. The actual cursor is shifted from its actual mouse position. In this manner, the intruder can trick a consumer to click on the malicious site with clever positioning of page elements [68].
De-anonymization attack
In quite a lot of social networking sites like Twitter and Facebook, users can hide or protect their real identity before releasing any data by using an alias or fabricated name [69]. But if a third party wants to find out the real identity of the user, it can be done by simply linking the information leaked by these social networking sites [70]. They use strategies such as tracking cookies, network topologies, and user group enrollment to uncover the client’s genuine identity [71]. It is a sort of information mining method in which mysterious information is cross-referred to other information sources to re-recognize the unknown information [60]. An attacker can collect information about the group membership of a user by stealing history from their browser and by combining this history with the data collected. Thus the attacker can de-anonymize the user who visits that attacker’s website [72].
Cyber espionage
Cyber espionage is an act that uses cyber capabilities to gather sensitive information or intellectual property with the intention of communicating it to opposing parties [73]. These attacks are motivated by greed for monetary benefits and are popularly used as an integral part of military activity or as a demonstration of illegal intimidation [74]. It might bring about a loss of competitive advantage, materials, information, foundation or death toll. A social engineer can perform social engineering assaults using social networking sites. He can acquire important data like worker’s assignment, email address, and so forth utilizing social networking sites [75].
Targeted threats
Cyberbullying
Cyberbullying is the use of electronic media such as emails, chats, phone conversations, and online social networks to bully or harass a person [76]. Unlike traditional bullying, cyberbullying is a continuous process [77]. It is continuously maintained through social media [78]. The attacker repeatedly sends intimidating messages, sexual remarks, posts rumors, and sometimes publishes embarrassing pictures or videos to harass a person [79]. He can also publish personal or private information about the victim causing embarrassment or humiliation. Cyberbullying can also happen accidentally. It is very difficult to find out the tone of the sender over text messages, instant messages, and emails. But the repeated patterns of such emails, texts, and online posts are rarely accidental [80].
Cyber grooming
Cyber grooming is establishing an intimate and emotional relationship with the victim (usually children and adolescents) with the intention of compelling sexual abuse [81]. The principle point of cyber grooming is to acquire the trust of the youngster and through which intimate and individual information can be attained from the child [82]. The data is often voluptuous in nature through sexual conversations, pictures, and videos which gives the attacker an advantage to threaten and blackmail the child [83]. Assailants frequently approach teenagers or kids through counterfeit identity in child-friendly sites, leaving them vulnerable and uninformed of the fact that they have been drawn closer with the end goal of cyber grooming. However, the victim can also unknowingly initiate the grooming process when they get rewarding offers, for example, cash in return for contact details or personal photographs of themselves. In some cases, the victim knows about the fact that he/she is conversing with an adult which can prompt further commitment in sexual activities. However, it is with the individual under the age of consent and in this manner constitutes a crime. The anonymity and accessibility of advanced media permit groomers to move toward various youngsters simultaneously, exponentially increasing the instances of cyber grooming. Despite what might be expected, there are a couple of instances of feelings for the crime of cyber grooming worldwide, as 66% of the world’s nations have no particular laws with respect to cyber grooming of children [84].
Cyberstalking
Cyberstalking is the observing of an individual by the means of internet, email or some other type of electronic correspondence that outcomes in fear of violence and interferes with the mental peace of that individual [85]. It involves the invasion of a person’s right to privacy. The attacker tracks the personal or confidential information of the victims and uses it to threaten them by continuous and persistent messages throughout the day. This conduct makes the victim exceptionally worried for his own safety and actuates a type of trouble, fear or disturbance in him [86]. Most of the individuals these days share their personal information like telephone number, place of residence, area, and schedule in their social networking profile. In addition, they likewise share their location-based data. An assailant can gather this data and use it for cyberstalking [87].















![Toni Kroos là ai? [ sự thật về tiểu sử đầy đủ Toni Kroos ]](https://evbn.org/wp-content/uploads/New-Project-6635-1671934592.jpg)


