Objective 3.1: Common Network Devices – Wikibooks, open books for an open world
Objective 3.1: Install, configure, and differentiate between common network devices
 Network switches
Network switches
Computer networking devices are units that mediate data in a computer network and are also called network equipment. Units which are the last receiver or generate data are called hosts or data terminal equipment.
 Hub
Hub
Hubs connect computers together in a star topology network. Due to their design, they increase the chances for collisions. Hubs operate in the physical layer of the OSI model and have no intelligence. Hubs flood incoming packets to all ports all the time. For this reason, if a network is connected using hubs, the chances of a collision increases linearly with the number of computers (assuming equal bandwidth use). Hubs pose a security risk since all packets are flooded to all ports all the time. If a user has packet sniffing software, they can extract data from the network and potentially decode it and use it. Hubs make it easy to “spy” on users on the same LAN as you.
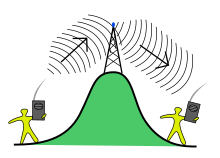 A wireless repeater.
A wireless repeater.
A repeater is an electronic device that receives a signal and retransmits it at a higher level and/or higher power, or onto the other side of an obstruction, so that the signal can cover longer distances without degradation. Because repeaters work with the actual physical signal, and do not attempt to interpret the data being transmitted, they operate on the physical layer, the first layer of the OSI model. Repeaters are majorly employed in long distance transmission to reduce the effect of attenuation. It is important to note that repeaters do not amplify the original signal but simply regenerate it.
Modem (from modulator-demodulator) is a device that turns the digital 1s and 0s of a personal computer into sounds that can be transmitted over the telephone lines of Plain Old Telephone Systems (POTS), and once received on the other side, converts those sounds back into a form used by a USB, Ethernet, serial, or network connection. Modems are generally classified by the amount of data they can send in a given time, normally measured in bits per second, or “bps”.
 Network Interface Card
Network Interface Card
A network interface card is a computer hardware component designed to allow computers to communicate over a computer network. It is both an OSI layer 1 (physical layer) and layer 2 (data link layer) device, as it provides physical access to a networking medium and provides a low-level addressing system through the use of MAC addresses. It allows users to connect to each other either by using cables or wirelessly. Most motherboards today come equipped with a network interface card in the form of a controller, with the hardware built into the board itself, eliminating the need for a standalone card.
Media converters are simple networking devices that make it possible to connect two dissimilar media types such as twisted pair with fiber optic cabling. They were introduced to the industry nearly two decades ago, and are important in interconnecting fiber optic cabling-based systems with existing copper-based, structured cabling systems. Media converters support many different data communication protocols including Ethernet, T1/E1, T3/E3, as well as multiple cabling types such as coaxial, twisted pair, multimode and single-mode fiber optics. When expanding the reach of a Local Area Network to span multiple locations, media converters are useful in connecting multiple LANs to form one large “campus area network” that spans over a limited geographic area. As local networks are primarily copper-based, media converters can extend the reach of the LAN over single-mode fiber up to 130 kilometers with 1550 nm optics.

Switches are often confused with bridges because they also operate at the data link layer of the OSI model. Similar to a hub, switches provide a central connection between two or more computers on a network, but with some intelligence. They provide traffic control for packets; rather than forwarding data to all the connected ports, a switch forwards data only to the port on which the destination system is connected. They use a database of MAC addresses to determine where computers are located and very efficiently send packets only where they need to go. The database is created dynamically as computers communicate on the network. The switch simply watches the incoming packets and memorizes the MAC address and port a packet arrives on. If a packet arrives with a destination computer that the switch does not have an address for in its MAC address table, it will flood the packet out all connected ports. A switch creates separate collision domains for each physical connection. A switch will only create separate broadcast domains if separate VLANs (Virtual Local Area Networks) are assigned to different ports on the switch. Otherwise, a broadcast received on one port will be flooded out all ports except the one it came in on.

Bridges can be identified by the fact that they operate at the data link layer of the OSI model. Bridges have intelligence and can “bridge” two of their ports together at very high speed. They use a database of MAC addresses to determine where computers are located and very efficiently send frames only where they need to go. The database is created dynamically as computers communicate on the network. A bridge simply watches the incoming frame and memorizes the MAC address and port a frame arrives on. It uses this information to locate a computer if a packet comes in that must be forwarded to it. If a frame arrives at the bridge and the bridge does not know where to send it, the bridge will flood the frame just like a hub does. Bridging is often inaccurately called switching.

A wireless access point (WAP or AP) is a device that allows wireless communication devices to connect to a wireless network using Wi-Fi, Bluetooth or related standards. The WAP usually connects to a wired network, and can relay data between the wireless devices (such as computers or printers) and wired devices on the network.
A typical corporate use involves attaching several WAPs to a wired network and then providing wireless access to the office Local Area Network. Within the range of the WAPs, the wireless end user has a full network connection with the benefit of mobility. In this instance, the WAP functions as a gateway for clients to access the wired network.
A Hot Spot is a common public application of WAPs, where wireless clients can connect to the Internet without regard for the particular networks to which they have attached for the moment. The concept has become common in large cities, where a combination of coffeehouses, libraries, as well as privately owned open access points, allow clients to stay more or less continuously connected to the Internet, while moving around. A collection of connected Hot Spots can be referred to as a lily-pad network.
Home networks generally have only one WAP to connect all the computers in a home. Most are wireless routers, meaning converged devices that include a WAP, router, and often an Ethernet switch in the same device. Many also converge a broadband modem. In places where most homes have their own WAP within range of the neighbors’ WAP, it’s possible for technically savvy people to turn off their encryption and set up a wireless community network, creating an intra-city communication network without the need of wired networks.
 Cisco 1800 series router
Cisco 1800 series router
Routers operate at the network layer of the OSI model and efficiently route information between Local Area Networks. Since routers operate in the third layer, the network layer, they must understand layer 3 addressing… such as TCP/IP. A router will divide a broadcast domain by not forwarding broadcasts on one connected network to another connected network. Routers operate in two different planes: the control plane, in which the router learns the outgoing interface that is most appropriate for forwarding specific packets to specific destinations, and the forwarding plane, which is responsible for the actual process of sending a packet received on a logical interface to an outbound logical interface.

A firewall is a part of a computer system or network that is designed to block unauthorized access while permitting outward communication. It is also a device or set of devices configured to permit, deny, encrypt, decrypt, or proxy all computer traffic between different security domains based upon a set of rules and other criteria.
Firewalls can be implemented in both hardware and software, or a combination of both. Firewalls are frequently used to prevent unauthorized Internet users from accessing private networks connected to the Internet. All messages entering or leaving the Local Area Network pass through the firewall, which examines each message and blocks those that do not meet the specified security criteria. Without proper configuration, a firewall can often become worthless. Standard security practices dictate a “default-deny” firewall ruleset, in which the only network connections which are allowed are the ones that have been explicitly allowed.
ods#DHCP_.28Dynamic_Host_Configuration_Protocol.29|DHCP]]-configured client (be it a computer or any other network-aware device) connects to a network, the DHCP client sends a broadcast query requesting necessary information from a DHCP server. The DHCP server manages a pool of IP addresses and information about client configuration parameters such as the default gateway, the domain name, the DNS (Domain Name System) servers, other servers such as time servers, and so forth. Upon receipt of a valid request the server will assign the computer an IP address, a lease (the length of time for which the allocation is valid), and other IP configuration parameters, such as the subnet mask and the default gateway. The query is typically initiated immediately after booting and must be completed before the client can initiate IP-based communication with other hosts.















![Toni Kroos là ai? [ sự thật về tiểu sử đầy đủ Toni Kroos ]](https://evbn.org/wp-content/uploads/New-Project-6635-1671934592.jpg)


