Network Protocols Concept
Mục Lục
Network Protocols Concept
What is Network and Network Protocol?
Let’s start with a fundamental question, what is a network in computer networking? It’s a group of interconnected devices, such as computers and servers, that are connected through various communication channels like wired or wireless connections. The main idea behind having a network is to allow for resource sharing, data exchange, and communication among the connected devices. Networks can vary in size, from small home networks to large networks like the Internet.
The devices within a network communicate with each other by following certain rules or protocols, known as network protocols. These protocols are standardized methods for exchanging data and ensuring reliable and efficient communication between devices.
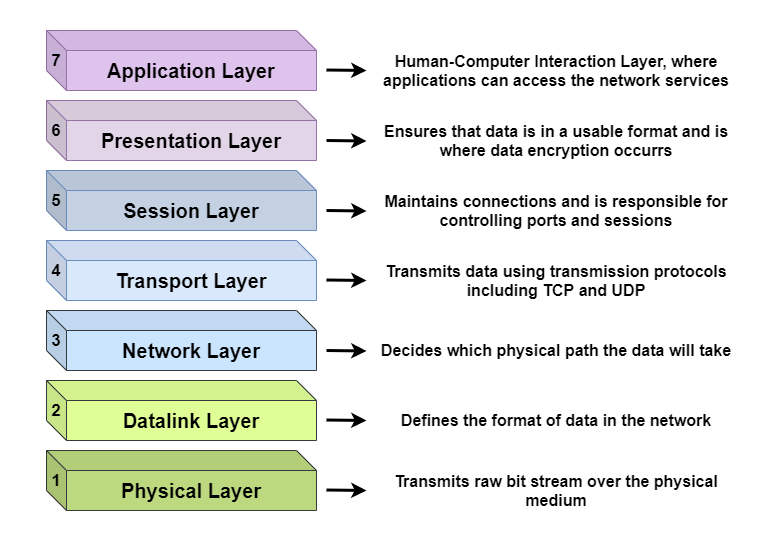
The OSI model of Computer Networking
Have you heard of the Open Systems Interconnection (OSI) model? It’s a useful framework for understanding how computer systems communicate over a network. The OSI model consists of seven layers, each of which represents a different aspect of networking.
- Application layer provides an interface between the network and the applications that use it.
- Presentation layer takes care of formatting and encoding data so that both the sender and receiver can understand it.
- Session layer establishes and terminates connections between devices, while the
- Transport layer ensures that data is delivered reliably and in the correct order.
- Network layer is responsible for routing data between different networks
- Data Link layer ensures reliable data transmission between devices on the same network.
- Physical layer deals with the transmission of raw data over a physical connection.
So network protocols are like the rules of the road for network communication. For example, Internet Protocol (IP) is in charge of directing data from its source to its destination, and it’s considered a network layer protocol. Another important protocol is the Transmission Control Protocol (TCP), which helps ensure that data packets are transmitted smoothly through networks. TCP operates at the transport layer.
Types of Network Protocols in Networking
Internet Protocols (IP)
As discussed above, Internet Protocol (IP) is a network layer protocol that allows data packets to be routed and addressed in order to pass through networks and reach their destination. When one machine wants to send data to another machine, it sends it in the form of IP packets. An IP packet is the basic unit of data that’s sent from one machine to another, and it’s made up of bytes. The IP packet has two main parts: the IP header and the data. The IP header holds information about the packet’s origin, destination, and other details, while the data section holds the actual payload of the packet.
What is IP address?
You might have heard of IP addresses, which are used to route data packets over the Internet and allow devices to communicate with each other. They’re like digital addresses that identify and locate devices on a network. IP addresses are unique and assigned to each device or domain that connects to the Internet.
IP addresses are written as four numbers separated by periods, such as 192.168.1.1. These numbers represent the numerical value of the address. There are two main types of IP addresses: IPv4 and IPv6. IPv4 addresses are 32-bit numbers written in decimal form, while IPv6 addresses are 128-bit numbers written in hexadecimal form.
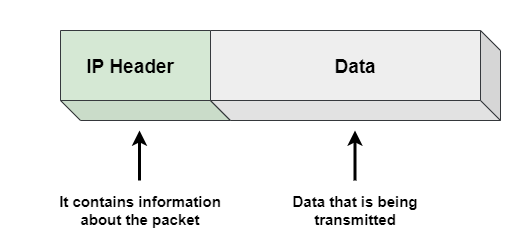
IP header section of an IP packet holds vital information about the packet itself, such as the source and destination IP addresses, total size of the packet, and the version of IP being used.
When you send a packet from your device to another, the source IP address in the IP header will show your device’s address and the destination IP address will show the address of the device you’re sending it to. Additionally, the size of the packet in the header includes the size of both IP header and data section.
Other important information in the IP header includes the time-to-live (TTL) field, which determines the number of hops a packet can make before it’s discarded, and the protocol field, which specifies the protocol being used for the data section. These bits of information are crucial for the routers on the network to properly direct the packet to its destination.
IPv4 vs. IPv6
IPv4, which was first introduced in 1983, was the first version of IP. It uses a 32-bit address scheme, meaning it can accommodate a maximum of 4,294,967,296 unique addresses. Despite its limitations, IPv4 still carries a significant chunk of internet traffic today, around 94%. The benefits of using IPv4 include encrypted data transmission for added security and privacy, as well as cost-effective and efficient routing of data.
With the increasing demand for internet addresses, IPv6 was developed in the 1990s to address the limitations of IPv4. It uses 128-bit address space, capable of accommodating 3.4 x 10^38 unique addresses. Also known as IPng (Internet Protocol next generation), IPv6 offers improved routing and packet processing compared to its predecessor, as well as enhanced security features. However, it is important to note that IPv6 is not compatible with IPv4, and upgrading can present a challenge.
Note: When sending large files, such as images or emails, a single IP packet may not suffice. In these cases, multiple packets are used to transmit the data. Unfortunately, this increases the risk of packets not reaching their destination, getting lost, or arriving in the wrong order.
Transmission Control Protocols (TCP)
Transmission Control Protocol (TCP) is a transport layer protocol used to transmit data over a network. It is built on top of the Internet Protocol (IP) and is used to solve problems above problems. When a machine wants to communicate with another machine using TCP, it establishes a connection with the destination machine through a handshake process. Once connection is established, two machines can communicate freely. Note: IP is responsible for delivering the packets, while TCP helps put them back in the correct order.
TCP provides a reliable stream delivery service to applications through sequenced acknowledgement. It is a connection-oriented protocol i.e. a connection must be established between applications before data transfer. TCP also provides extensive error checking through flow control and acknowledgement of data, and it ensures that data packets arrive in correct order at the receiving end. Lost data packets can also be retransmitted using TCP.
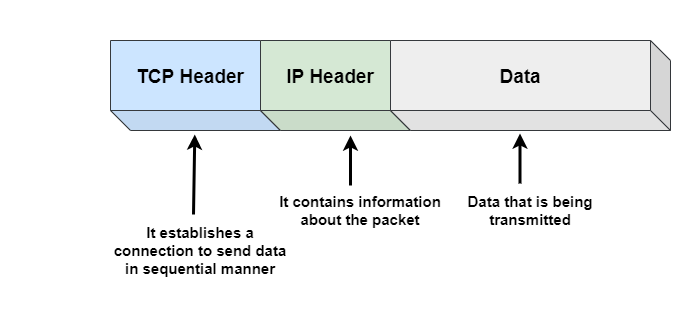
Some advantages of TCP include its ability to ensure that data reaches its destination, arrives on time, and does not have duplicates. However, TCP cannot be used for broadcast or multicast connections.
TCP is widely used for communication over a network and has many applications, including emails, file transfer protocol (FTP), and streaming media. The two protocols are often referred as TCP/IP when used with IP.
User Datagram Protocol (UDP)
UDP is a connectionless transport layer protocol. Unlike Transmission Control Protocol(TCP), UDP does not provide any reliability, flow control, or error recovery functions. As a result, UDP is useful in situations where reliability mechanisms of TCP are not necessary and faster transmission is desired, such as in video streaming and gaming.
UDP is also suitable for multicast and broadcast connections i.e. sending a single message to multiple recipients. However, there are some disadvantages to using UDP. For example, It is possible for packets to be lost, delivered twice, or not delivered at all.
HyperText Transfer Protocol (HTTP)
Hypertext Transfer Protocol (HTTP) is an application layer protocol used for communication in distributed, collaborative, and hypermedia information systems. It is built on top of Transmission Control Protocol (TCP) and provides a higher level of abstraction that allow developers to focus on their applications rather than the details of TCP and IP packets. Some common HTTP methods include PUT, GET, POST, and DELETE.
- HTTP protocol operates on a request-response model i.e. one machine sends a request for information, and the other machine sends back a response with the requested information. This is how text, images, and other multimedia files are shared all across the World Wide Web.
- HTTP is a stateless protocol i.e. the client and server only maintain awareness of each other during the active connection. Once the connection is terminated, both parties forget about each other’s existence.
Despite some limitations, HTTP has several benefits that make it a popular choice for transmitting information over the web. It requires low memory and CPU usage due to its few concurrent connections. Additionally, it has the ability to report errors without closing connections, which can reduce network congestion. However, it’s important to keep in mind that HTTP is not equipped with encryption capabilities, so it may not be the most secure option for transmitting sensitive information.
Hypertext Transfer Protocol Secure (HTTPS)
Hypertext Transfer Protocol Secure (HTTPS) is a secured version of Hypertext Transfer Protocol (HTTP). Unlike HTTP, which transfers data in a plain text format, HTTPS transfers data in an encrypted format and protect it from interpretation or modification by hackers during the transfer of packets.
It is often used when sensitive information, such as passwords and financial transactions, is transmitted. However, HTTPS may be slower than HTTP due to the overhead of encryption and decryption process.
File Transfer Protocol (FTP)
File Transfer Protocol (FTP) is used for transferring files between hosts, both local and remote. It runs on top of Transmission Control Protocol (TCP) and creates two TCP connections: control connection and data connection. Control connection is used to transfer control information, such as passwords and commands to retrieve and store files, while data connection is used to transfer the actual file. Both connections run in parallel during the entire file transfer process.
FTP has several advantages like ability to share large files and multiple directories at the same time, ability to resume file sharing if it is interrupted, and ability to recover lost data and schedule file transfers. However, FTP has some disadvantages as well. It lacks security, as data, usernames, and passwords are transferred in plain text, making them vulnerable to malicious actors. FTP also lacks encryption capabilities, which makes it non-compliant with industry standards.
Remote Procedure Call (RPC)
Remote Procedure Call (RPC) is a protocol that allows a program on one device to request a service from a program on another device over a network, without the need to understand details of the network. It is used for interprocess communication in client-server based applications and is also known as a subroutine call or function call.
RPC works on a client-server model, where requesting program is the client and service providing program is the server. It uses either Transmission Control Protocol (TCP) or the User Datagram Protocol (UDP) to carry messages between communicating programs.
There are several advantages to using RPC. It can improve performance by omitting many protocol layers and minimize code rewriting or redevelopment efforts. However, RPC has not yet been proven to work effectively over wide-area networks and does not support other transport protocols besides TCP/IP.
We are looking forward to your feedback in the message below. Enjoy learning, Enjoy system design!















![Toni Kroos là ai? [ sự thật về tiểu sử đầy đủ Toni Kroos ]](https://evbn.org/wp-content/uploads/New-Project-6635-1671934592.jpg)


