IDS vs. IPS: Definitions, Comparisons & Why You Need Both | Okta
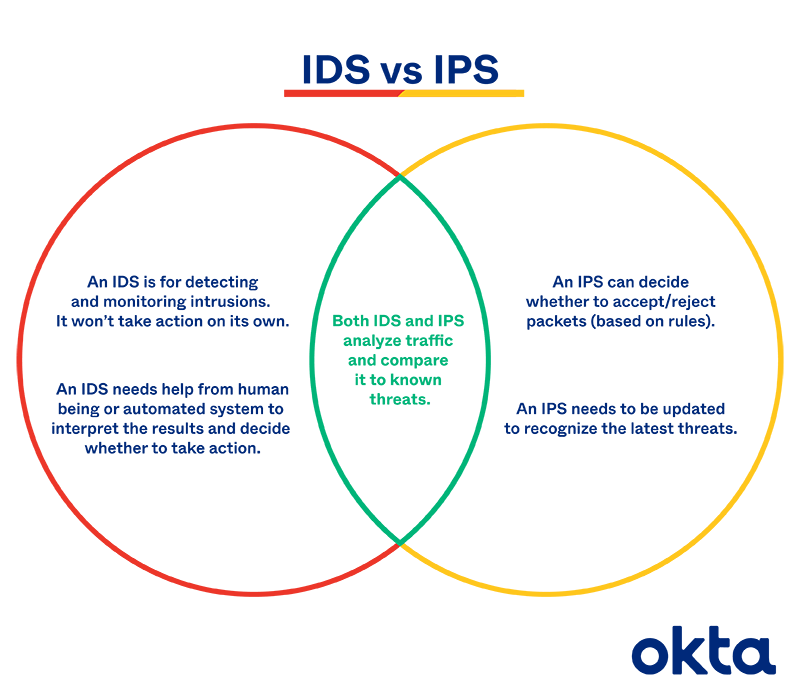
An intrusion detection system (IDS) monitors traffic on your network, analyzes that traffic for signatures matching known attacks, and when something suspicious happens, you’re alerted. In the meantime, the traffic keeps flowing.
An intrusion prevention system (IPS) also monitors traffic. But when something unusual happens, the traffic stops altogether until you investigate and decide to open the floodgates again.
What will you vote for in the IDS vs. IPS debate? If you work in the IT space, you’ll probably be asked this question at some point in your career. And if you’re not sure how to answer right now, you’re certainly not alone.
Both systems have advantages and disadvantages. Because of that, some experts believe an IDS/IPS combination is the best way to protect a server.
Mục Lục
What Is an IDS?
You want to protect the assets on your server. But you don’t want to slow down the traffic, even if a problem occurs. An intrusion detection system (IDS) could be the solution you’ve been looking for.
Five main types of IDS exist.
- Network: Choose a point on your network and examine all traffic on all devices from that point.
- Host: Examine traffic to and from independent devices within your network, and leave all other devices alone.
- Protocol-based: Place protection between a device and the server, and monitor all traffic that goes between them.
- Application protocol-based: Place protection within a group of servers and watch how they communicate with one another.
- Hybrid: Combine some of the approaches listed above into a system made just for you.
No matter what type of IDS you choose, the underlying function is similar. You’ll use passive technology to detect an intrusion. When something is found, you’ll get an alert about it.
Your system might detect problems with:
- Patterns. The technology flags unusual requests, very large packet sizes, or anything that seems out of the ordinary for your system at that time.
- Prior attacks. The technology flags anything on your server that’s been used in a known and successful attack on another server.
- Machine learning. The system picks up information about everything that happens on your server in an average day, and that data helps to refine the protections in place.
A system like this comes with plenty of advantages. You can set one up very quickly, and it’s hard for attackers to spot your protections. But by the time you’re notified of an attack in progress, you may have lost valuable time you could use to protect your assets.
What Is an IPS?
You want to stop an attack as soon as it’s discovered, even if that means closing down legitimate traffic for security concerns. An intrusion protection system (IPS) could be just right for you.
The goal of an IPS is to prevent damage. While you’re kept in the loop about the attack, the system is already working to keep things safe.
An IPS can protect against exterior intruders. But people within your organization can also take steps that harm your security. An IPS can protect against these actions too, so it can help train your employees about what is allowed and what is not.
Four main types of IPS exist:
- Network: Analyze and protect traffic on your network.
- Wireless: Observe anything happening within a wireless network and defend against an attack launched from there.
- Network behavior: Spot attacks that involve unusual traffic on your network.
- Host-based: Scan events that occur within a host you specify.
Most administrators install an IPS right behind the firewall. But it’s clear that you can set up different configurations to protect your company’s assets in a very customized way.
No matter what type you choose, the IPS will take a predictable set of steps.
An IPS monitors your network for suspicious activity or attacks in progress. When an anomaly is spotted, you’re alerted. But in the interim, the system springs to action. It might:
- Close sessions. It can identify the entry point for the unusual activity and block it from continuing. That might mean terminating the TCP session, blocking an IP address, or some similar step.
- Strengthen firewalls. The system might identify the gap in the firewall that allowed the attack to enter. A change in programming could prevent something similar in the future.
- Clean up. The system can scan for damaged or malicious content within the server and remove it.
The IPS works in real time, and the technology inspects every packet moving through the protected space. It can take swift and significant action in response to an attack, and while that can keep you protected, these systems can throw up false positives. When that happens, traffic can slow for no reason whatsoever.
At the end of an attack and cleanup, you have a report of what went wrong and what the system did to fix it. You can use this data to help you strengthen your system against a future attack. And you can walk back through the protections the system made and undo them if you feel they aren’t worthwhile.
IDS vs. IPS: Differences & Similarities
Should you choose an IDS or an IPS? Let’s examine how they’re alike and what sets them apart.
Both systems can:
- Monitor. After setup, these programs can look over traffic within parameters you specify, and they will work until you turn them off.
- Alert. Both programs will send a notification to those you specify when a problem has been spotted.
- Learn. Both can use machine learning to understand patterns and emerging threats.
- Log. Both will keep records of attacks and responses, so you can adjust your protections accordingly.
But they differ due to:
- Response. An IDS is passive, while an IPS is an active control system. You must take action after an IDS alerts you, as your system is still under attack.
- Protection. Arguably, an IDS offers less help when you’re under threat. You must figure out what to do, when to do it, and how to clean up the mess. An IPS does all of this for you.
- False positives. If an IDS gives you an alert about something that isn’t troublesome at all, you’re the only one inconvenienced. If an IPS shuts down traffic, many people could be impacted.
Scan through these lists, and you may immediately understand which system is best for you. If your company can’t handle a disruption due to a technical error, for example, an IDS may be best. But if you can’t endure even a second of an attack without losing trade secrets or your reputation, an IPS may be better.
IDS & IPS Working Together
Many companies avoid the IDS vs. IPS problem by deploying both solutions to protect their assets and servers.
Choose an option like this, and you could use the IPS for active network security while the IDS gives you a deep understanding of how the traffic moves across your network.
A solution like this gives you information you can build on to keep your entire system safe. But you’ll also avoid letting an attack go unchecked.
At Okta, we use identity context to offer a lightweight IDS/IPS combination to ensure our clients’ privacy and safety. Deploying a combination like this gives your customers the best of both worlds, protecting assets while eliminating too many false positives.
We’d love to tell you more about how this works. Contact us to learn more today.
References
Intrusion Detection System (IDS). (January 2020). Geeks for Geeks.
What Is an Intrusion Detection System? How an IDS Spots Threats. (February 2018). CSO.
How Do Intrusion Detection Systems (IDS) Work? (May 2020). EC-Council.
Intrusion Detection and Prevention Systems. (September 2014). The InfoSec Handbook.
Intrusion Prevention System. (September 2019). Geeks for Geeks.
7 Ways to Get the Most from Your IDS/IPS. (April 2019). DarkReading.















![Toni Kroos là ai? [ sự thật về tiểu sử đầy đủ Toni Kroos ]](https://evbn.org/wp-content/uploads/New-Project-6635-1671934592.jpg)


