Best Firewall Security Zone Segmentation Free Guide
Hardware firewalls are the cornerstone of network security for almost all TCP/IP networks. From SOHO and SMB networks, to big Enterprise environments, the network firewall provides the basic defense against attacks to I.T systems and digital information assets. Although the boundaries of modern networks are expanding outside the firewall perimeter, most networks still have a well defined structure which includes the internal network zone, the external untrusted network zone and other optional intermediate security zones.
A security zone can be defined as a network segment which hosts a group of systems with similar requirements for information protection. In other words, a security zone is usually a Layer3 network subnet on which several hosts (servers, workstations etc) are connected to. Traffic to and from this specific network is then controlled by a Firewall on the IP and Port level or even on the Application level.
Enhance your network security – Try WebTitan web filtering solution for free today
Try for Free
Mục Lục
Perimeter Security Zone Segmentation for Enterprise Networks
There is no single perimeter network topology that will fit any enterprise network. Each network has its own unique requirements and functionalities; therefore the network needs to adopt accordingly to satisfy the business needs.
However, there is a “best practice” approach to implement a network perimeter which offers enhanced security and data protection from network attacks. This approach is illustrated on the diagram below. Again, the above network topology is just an example that we have seen implemented in many enterprise environments but it can have different variations (such as using two firewall devices instead of one, only one DMZ zone instead of two etc).
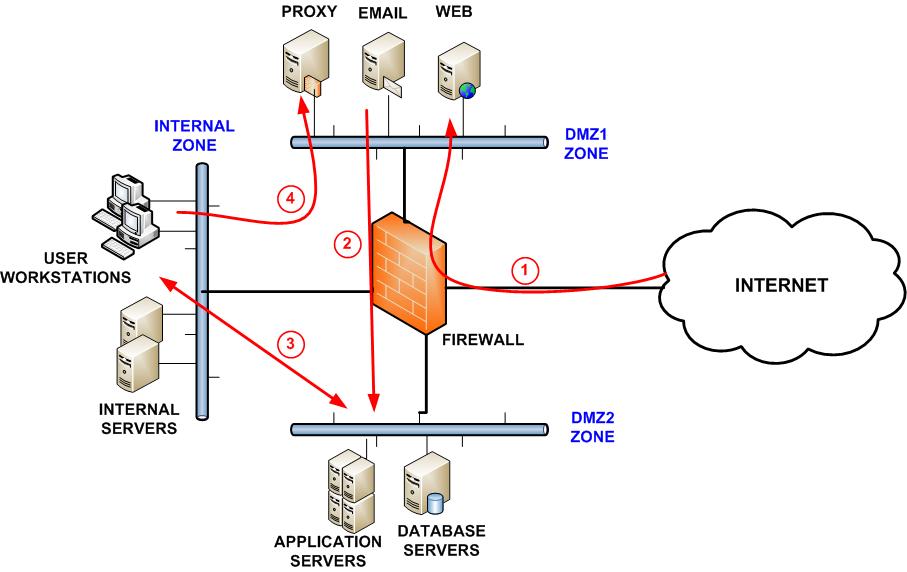
The suggested perimeter network above includes two DMZ (Demilitarized Zones), namely DMZ1 and DMZ2, and also an Internal Zone. The red line arrows indicate the allowed traffic flow from the Firewall.
DMZ Zones
A DMZ zone is an isolated Layer3 subnet on which the hosts connected are usually exposed to the public Internet in order to provide services to users (Web, Email, DNS etc). Therefore they are the most vulnerable to attacks. Because of the increased potential of these hosts suffering an attack, they are placed in a Demilitarized Zone (DMZ) in order to minimize the damage to the internal protected network in case one of these servers gets compromised.
In the perimeter segmentation network we suggest on the diagram above, we have two DMZ zones in order to provide the best protection to the Internal Zone.
Enhance your network security – Try WebTitan web filtering solution for free today
Try for Free
DMZ1
This zone hosts the public-facing servers which must be accessible from the Internet. This zone usually hosts services such as Web, Email, DNS, Proxy etc. The firewall should allow traffic from the Internet towards DMZ1 only (see Traffic Line 1 above). Also, only the required TCP/UDP ports must be allowed (such as 80, 443, 25 etc).
DMZ2
This is an intermediary zone required to host Application Servers, Database Servers etc which are indirectly accessed from the Internet via the DMZ1 zone. For example, security best practices suggest that a Web server which accesses data from a Database must not be installed on the same physical machine as the Database Server. Therefore, we suggest placing the Database Server on DMZ2.
Also, a front-end Web Server which communicates with a web application server should be placed in two separate security zones as well.
The above arrangement protects the Internal Zone even further since any compromise of the Database or Application servers (via the DMZ1 servers) will not result in access to the protected Internal network.
The firewall should allow access to DMZ2 from DMZ1 only on the required ports (see Traffic Line 2 on the diagram). Also, DMZ2 can have limited access to and from the Internal Zone (Traffic Line 3) for some special cases (such as accessing maybe an internal management server, for backup, for authentication to an internal Active Directory etc).
Internal Security Zone
This zone usually hosts the internal user workstations and other important servers such as file servers, Active Directory servers, internal databases, specialized applications (ERP, accounting software) etc. The firewall must not allow direct access from the Internet towards this Internal network. Moreover, outgoing Web traffic from users in this network can use an HTTP Proxy server (see Traffic Line 4) located in DMZ1 in order to access the Internet. There are countless network perimeter topologies that can be implemented by companies to facilitate their business needs. The discussion above is a suggestion of a solid firewall zone segmentation to achieve strong network security in an enterprise environment. Use this and it should ensure you have solid network security.
Are you an IT professional that wants to ensure sensitive customer and staff data and devices are protected? Talk to a security specialist or Email us at [email protected] with any questions.

Enhance your network security – Try WebTitan web filtering solution for free today
Try for Free















![Toni Kroos là ai? [ sự thật về tiểu sử đầy đủ Toni Kroos ]](https://evbn.org/wp-content/uploads/New-Project-6635-1671934592.jpg)


