An investigation into SS7 Exploitation Services on the Dark Web – SOS Intelligence
In this latest investigative article we will be taking a look at alleged SS7 exploitation services on the Dark Web and diving into their credibility using our SOS Intelligence analytics toolkit.
If you don’t want to miss the latest post, then please sign up to our newsletter here.
SS7 Significance & Background
Signalling System 7 is a telecommunications protocol adopted internationally that defines how the network elements in a public switched telephone network (PSTN) exchange information and control signals.
The signalling transport (SIGTRAN) protocols proved interoperability of SS7 signalling to operate over IP based networks. This enables PSTN services to operate analogue telephone systems and modern IP network equipment. SIGTRAN uses its own Stream Control Transmission Protocol (SCTP) as opposed to TCP or UDP (Transmission Control Protocol or User Datagram Protocol)
With the flexibility of SIGTRAN operating over IP this has given rise to the commoditisation of SS7 access through SS7 gateways, that bridge TCP based service such as VoIP, SMS gateways etc. providing interconnectivity through to SS7 Link providers.
SS7 offers the following key services (but not limited to):
- Call set up, routing and tear-down
- Caller ID
- SMS
- Mobile phone roaming and tracking
- Call forwarding
- Voicemail and call waiting
- Conference calling
The primary security defence of a SS7 network is that it is a closed system, no real message integrity or security exists and therefore messages transmitted across the SS7 network are easily intercepted or forged. End users, even SMS gateway providers do not have access to it.
However, given the feature rich tooling of SS7 it is ripe for abuse and a target for not only government run intelligence agencies but also organised crime groups that operate partly or wholly in the cyber domain, therefore access to SS7 is a sought after wildcard for any criminally minded hacker.
SS7 enabled crime and abuse
There are a number of significant abuses of SS7 that are possible with a compromised gateway or with clandestine access to a SS7 network.
We will discuss some of the SS7 enabled abuses as an overview. Please read on!
SMS 2FA Interception
SS7 plays a part in the transportation of SMS messages. An attacker may be able to register a victims MSISDN (mobile number) on a fake MSC (Mobile Switching Centre), the victims operator’s HLR (Home Location Register) that works as a kind of telephone directory for MSISDNs, operators and SMS service centres (SMSC) will set the new location for the Victim’s MSISDN.
When, for this example the victims Bank sends them a 2FA authentication token the MSC transfers the SMS to the SMSC the real MSMSC asks the victims opeartor’s HLR for the victims location, the HLR replies with the attacker operated MSC. The real operator’s SMSC transfers the SMS to the fake MSC operated by the attack.
Therefore the attacker is able to obtain the original 2FA token and respond to the victim’s Bank authentication prompt.
Call Intercept
Likewise a similar attack is possible with Call interception where an attacker can using the first part of the spoofing process redirect a victims call to a VoIP provider or their own IP-PBX (for example Asterisk) and handle the call much like any VoIP call.
This attack can also surface in other ways, such as WhatsApp and other ‘end to end’ encrypted messaging services where the attack may be able to redirect WhatsApp enrolment to another device and intercept, by redirecting messages to their own attacker controlled phone.
SMS Spoofing
By far the simplest of attacks and an attack that doesn’t require direct SS7 access is the spoofing of SMS messages to a sender. Most are unaware that the “from” part of a SMS message has no authentication and can easily be spoofed, in fact the SMS sender can put any alpha numeric word in the “from” of an SMS message.
SMS spoofing attacks can be easily and cheaply performed by obtaining access to an SMS gateway service (on the clear web). Nearly all of the ones that SOS Intelligence were able to asses appeared to have no abuse monitoring or prevention. It is therefore possible to very easily and cheaply (in some cases for free) send a spoofed message much like a phishing email to a victim and prompt a call to action.
Location Tracking
There are a number of free or paid for clear web services that allow some basic HLR lookup services, none of these services necessary provide an exact location fix of a Mobile Subscriber however they do in part allow some one to see if a MSISDN is roaming, assigned to its home operator, active or deactivated.
Within the SS7 network of a network operator it may be possible to request the LAC (Location Area Code) and Cell ID and with that information get a reasonably good location for a victim. However, this may require the prior knowledge of the subscribers IMEI (International Equipment Identity) or and IMSI (International Mobile Subscriber Identity) – A MSISDN alone may not be sufficent to be able to query this information. However, a LHR lookup may provide an attacker with an IMSI.
It understood that it is fairly common and universal for an operator to provide specific LAC/CID, information to a GSM MAP (Mobile Application Part) message where an attack could send a “provideSubscriberinfo” message asking for the subscribers location and spoofing a SMSC. The LAC, CID and other information can then be looked online for example using Ofcoms website or service such as cell mapper.
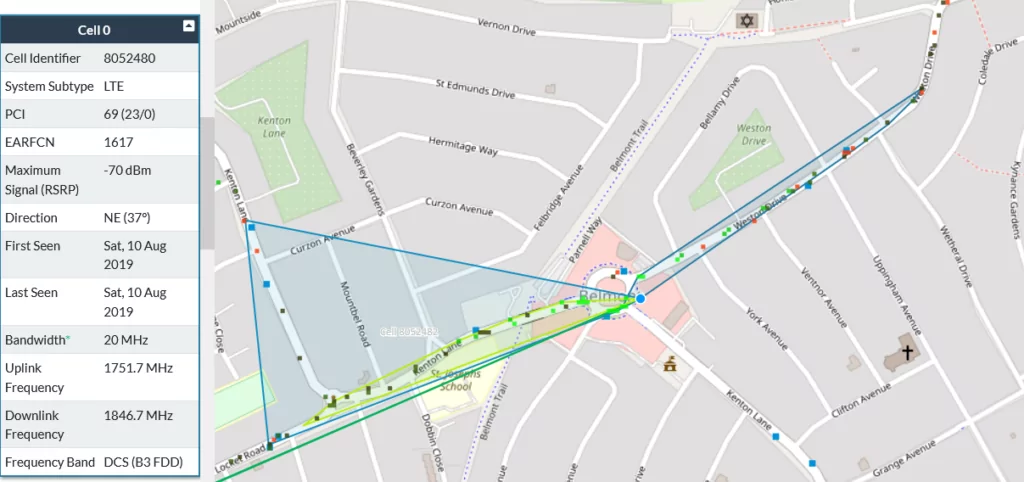 cellmapper.net tower locator
cellmapper.net tower locator
It may be possible to automate the process of mapping LAC/CID [along with MCC&MNC information] to a geographic location such as with joining together of services provided by cellmapper.net for example.
Availability and Legitimacy of SS7 hacking services on the Dark Web
With the initial introduction to SS7 background and the significance of hacking SS7 out of the way lets start by taking a look into what SS7 hacking or exploitation services are available on the Dark Web.
If we start off with using our DARKSEARCH too and searching for SS7 in page titles across the last year of our index we see some 84 unique onion domains.
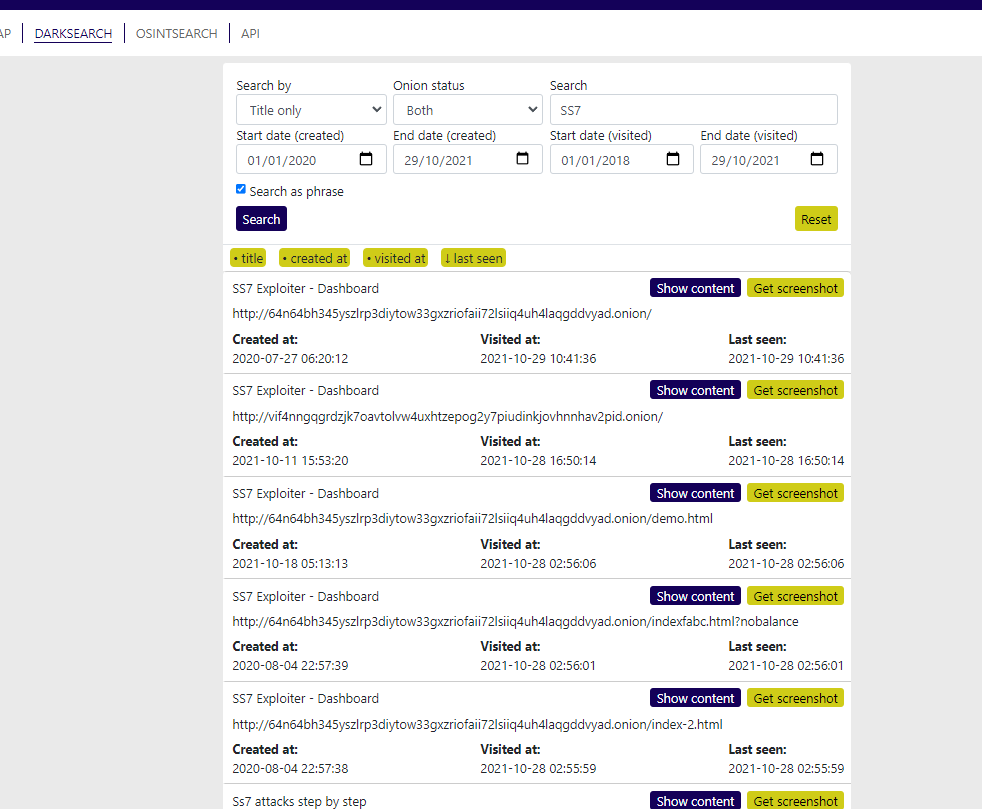 SS7 Title Search
SS7 Title Search
Narrowing down on only onions that we’ve seen to be up recently further reduces our results to a manageable amount.
Key providers of alleged SS7 exploitation services
It would appear that there are a few main key providers of alleged SS7 exploitation services.
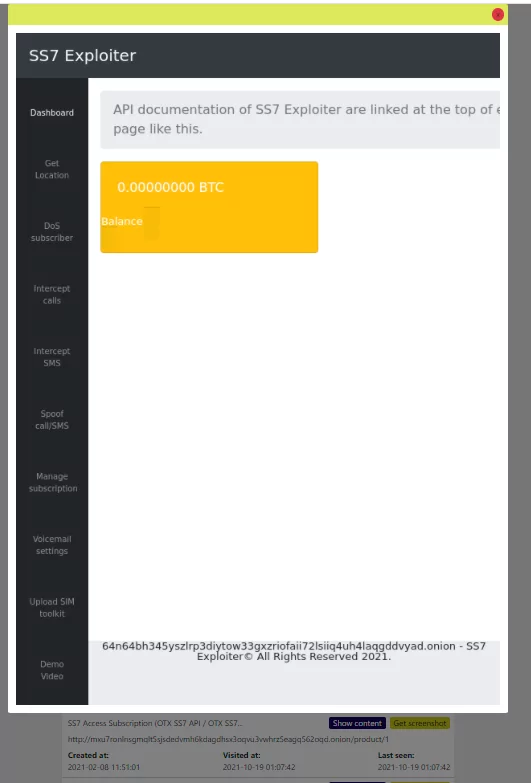
1) SS7 Exploiter
64n64bh345yszlrp3diytow33gxzriofaii72lsiiq4uh4laqgddvyad.onion
vif4nngqgrdzjk7oavtolvw4uxhtzepog2y7piudinkjovhnnhav2pid.onion
xpll5hy2jlze25w2.onion
Services Offered:
- Get Location
- DoS subscriber
- Intercept calls
- Intercept SMS
- Spoof call/SMS
- Manage subscription
- Voicemail settings
- Upload SIM toolkit
2) SS7 ONLINE Exploiter
3zx4rwy3izy2zhywz2vm5krc2zqmrahc7sv7ps2ekqvfxv62skueruid.onion
Services Offered:
- Get Location
- DoS subscriber
- Intercept calls
- Intercept SMS
- Spoof call/SMS
- Manage subscription
- Voicemail settings
- Upload SIM toolkit
3) SS7 Hack
ss7hxvtum6iyykshcefjmm5pvb2y3lsvcfh2lzml2vtdhqlseqhqnpqd.onion/
ss7hfyqn7fv7kjs7.onion
Services Offered:
- SMS Intercept
- Call Intercept and Redirect
- Location Tracking
Services appear to be offered on time bases (1 day, 7 days, 30 days)
 SS7 Hack
SS7 Hack
All onions associated with this provider appear to be offline at time of writing. All information of this service is gained from the historic SOS Intelligence Dark Web index.
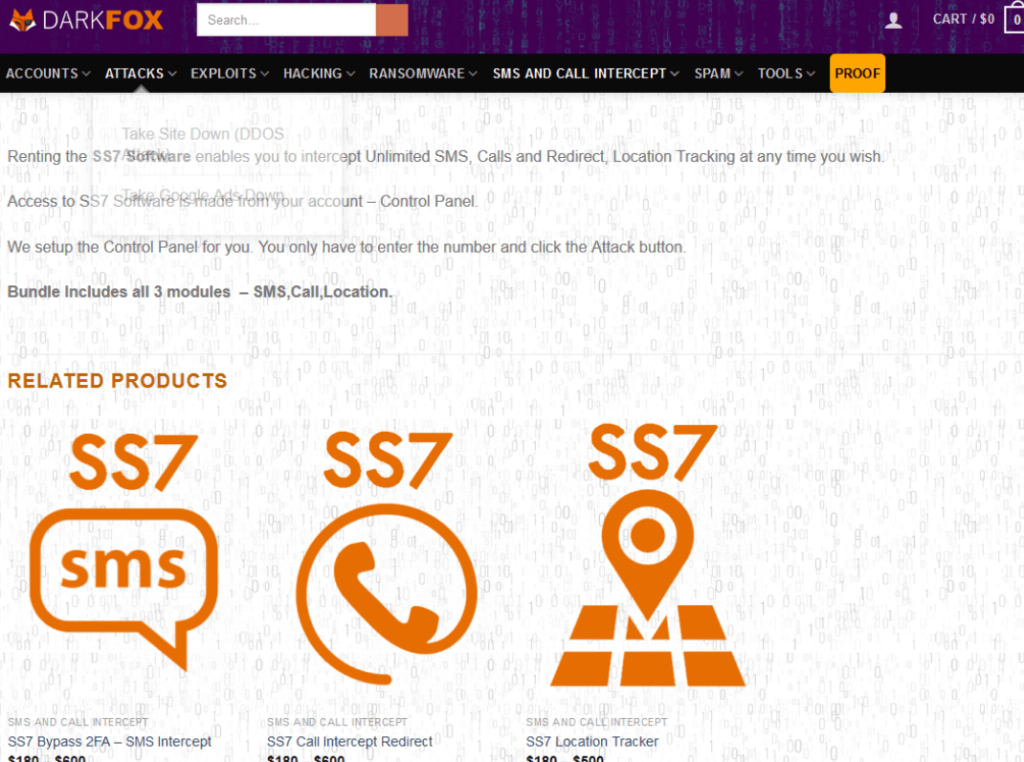
4) Dark Fox Market
darkfoxt5pv4gjak.onion/index.php/product/ss7-software/
http://darkfoxikqntsbpi4olzks26o5ejvej7lhy3mxhfltonbh2k2wrlumad.onion/
Services Offered:
- SS7 Bypass 2FA (SMS Intercept)
- SS7 Call Intercept
- SS7 Location Tracker
Lets dig into these and see what we can find.
Looking at the “SS7 Exploiter Dashboard” service
SS7 Exploiter Dashboard
The oldest reference we have in our index, from June 6th 2020, we see that the HTML source of that page appears to have been Mirrored using HTTrack (A common website mirroring tool used by ‘419’ Advance Fee Fraud scammers) on the 14th of May 2019 mirroring another domain, xpll5hy2owj4zj22.onion
HTTrack Mirror of xpll5hy2owj4zj22
and likewise the other domain for the SS7 Exploiter Service: 64n64bh345yszlrp3diytow33gxzriofaii72lsiiq4uh4laqgddvyad.onion
Appears also to have been a copy of xpll5hy2owj4zj22.onion
This then leaves the SS7 ONLINE Exploiter an almost identical looking website, as the SS7 Exploiter Service but without the Demo Video
We see that this page has a contact email address of “[email protected]”
But these pages have no HTTrack comments in them, suggesting that they may be the original pages and that the “SS7 Exploiter – Dashboard” are copies.
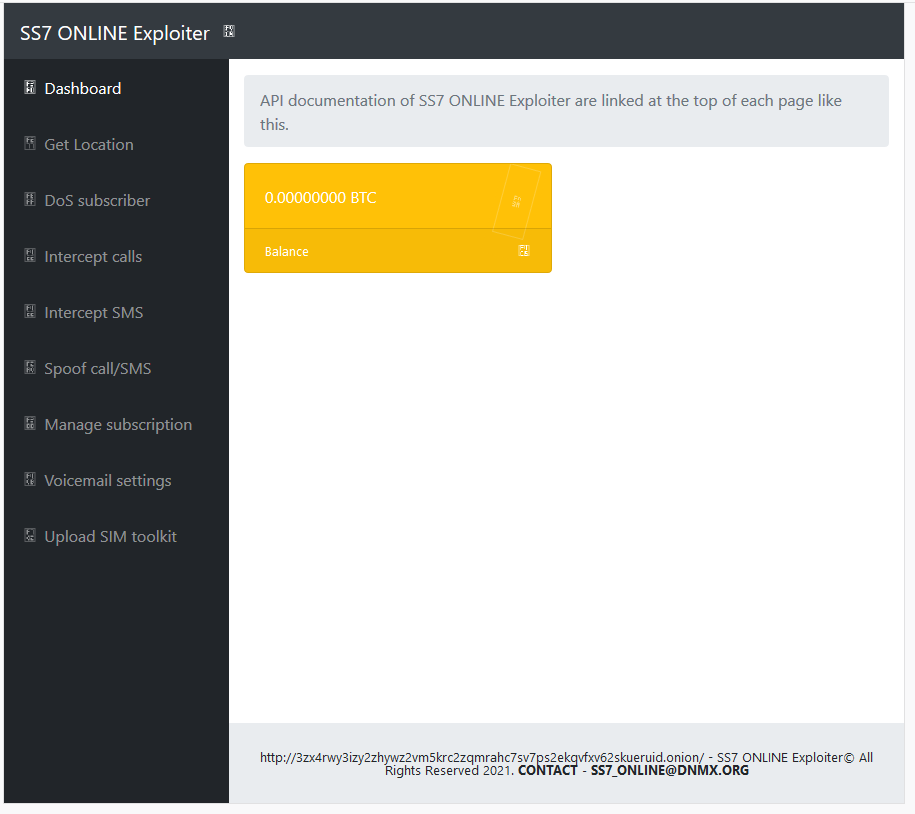 SS7 Exploiter Dashboard
SS7 Exploiter Dashboard
We can use our dark web email search API to locate any reference to that email address across the dark web
So far we only see one result.
Email Dark Web Search API
It would appear that the “SS7 ONLINE Exploiter” services came after SS7 the cloned “SS7 Exploiter” and may in fact just be clones of a clone with the HTTrack parts stripped out and demo video link removed and with the contact email address added.
 SOS Intelligence DARKMAP tool
SOS Intelligence DARKMAP tool
Using our DARKMAP tool we see the xpll5hy2jlze25w2.onion website on the very edges of the Dark Web with no known links in or out.
 Dark Map location of xpll5hy2jlze25w2.onion
Dark Map location of xpll5hy2jlze25w2.onion
However, the identical copy of the website but under the 64n64bh345yszlrp3diytow33gxzriofaii72lsiiq4uh4laqgddvyad.onion address we see in a much more central part of the Dark Web:
 Dark Map location of 64n64bh345yszlrp3diytow33gxzriofaii72lsiiq4uh4laqgddvyad.onion
Dark Map location of 64n64bh345yszlrp3diytow33gxzriofaii72lsiiq4uh4laqgddvyad.onion
And we see it with 3 inbound links
inbound Links from:
sz5h6tiqkdkfl55qa3kcxgzck3xeffo6cso7sjpc7hc7sr3vghdyicqd.onion “The Dark Web Links Directory “
linkdir7ekbalksw.onion “The Dark Web Links Directory v2 Onion Address “
toponiibv4eo4pctlszgavni5ajzg7uvkd7e2xslkjmtcfqesjlsqpid.onion “Hidden Link Directory “
Dark Map 64n64bh345yszlrp3diytow33gxzriofaii72lsiiq4uh4laqgddvyad.onion inbound Links

SS7 Hack
As for the SS7 Hack service. This too appears to have been a copy clone, this time of a clear web website www[.]ss7[.]dev made on Friday the 18th 2021
HTTrack clone of ss7.dev website

Indeed, both of the “SS7 Hack” websites appear to be identical
 Dark Map location of SS7 Hack
Dark Map location of SS7 Hack
SS7 Hack has one inbound link from:
e6wzjohnxejirqa2sgridvymv2jxhrqdfuyxvoxp3xpqh7kr4kbwpwad.onion “TorNode – Onion Links Directory “
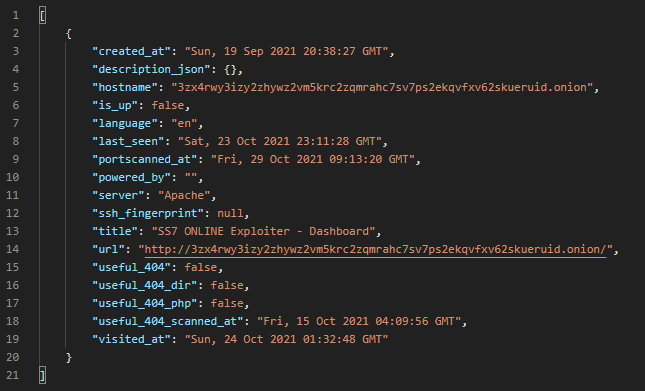
On the cached front page of SS7 Hack website we find an email address and as before using our Email Search API we see there are 3 results, 1 being a Tor Search service and the other two being the SS7 Hack website duplicates.
[
{
“created_at”: “Mon, 22 Feb 2021 16:30:49 GMT”,
“description_json”: {},
“hostname”: “searchgf7gdtauh7bhnbyed4ivxqmuoat3nm6zfrg3ymkq6mtnpye3ad.onion”,
“is_up”: false,
“language”: “en”,
“last_seen”: “Sat, 09 Oct 2021 08:42:11 GMT”,
“portscanned_at”: “Tue, 23 Feb 2021 02:59:20 GMT”,
“powered_by”: “”,
“server”: “nginx”,
“ssh_fingerprint”: null,
“title”: “The Deep Searches”,
“url”: “http://searchgf7gdtauh7bhnbyed4ivxqmuoat3nm6zfrg3ymkq6mtnpye3ad.onion/”,
“useful_404”: true,
“useful_404_dir”: false,
“useful_404_php”: true,
“useful_404_scanned_at”: “Wed, 29 Sep 2021 18:15:38 GMT”,
“visited_at”: “Sat, 09 Oct 2021 08:43:37 GMT”
},
{
“created_at”: “Fri, 25 Jun 2021 21:19:08 GMT”,
“description_json”: {},
“hostname”: “ss7hfyqn7fv7kjs7.onion”,
“is_up”: false,
“language”: “en”,
“last_seen”: “Tue, 07 Sep 2021 19:02:07 GMT”,
“portscanned_at”: “Tue, 29 Jun 2021 18:23:08 GMT”,
“powered_by”: “”,
“server”: “Apache”,
“ssh_fingerprint”: null,
“title”: “SS7 Hack – SMS Intercept – WhatsApp, Telegram, GMAIL, Facebook, Instagram, Twitter, Phone Tapping, Call, Tracking.”,
“url”: “http://ss7hfyqn7fv7kjs7.onion/”,
“useful_404”: true,
“useful_404_dir”: true,
“useful_404_php”: true,
“useful_404_scanned_at”: “Mon, 06 Sep 2021 17:46:32 GMT”,
“visited_at”: “Wed, 06 Oct 2021 15:28:34 GMT”
},
{
“created_at”: “Tue, 05 Oct 2021 21:35:23 GMT”,
“description_json”: {},
“hostname”: “ss7hxvtum6iyykshcefjmm5pvb2y3lsvcfh2lzml2vtdhqlseqhqnpqd.onion”,
“is_up”: false,
“language”: “en”,
“last_seen”: “Fri, 15 Oct 2021 21:21:48 GMT”,
“portscanned_at”: “Wed, 06 Oct 2021 02:31:26 GMT”,
“powered_by”: “”,
“server”: “Apache”,
“ssh_fingerprint”: null,
“title”: “SS7 Hack – SMS Intercept – WhatsApp, Telegram, GMAIL, Facebook, Instagram, Twitter, Phone Tapping, Call, Tracking.”,
“url”: “http://ss7hxvtum6iyykshcefjmm5pvb2y3lsvcfh2lzml2vtdhqlseqhqnpqd.onion/”,
“useful_404”: true,
“useful_404_dir”: true,
“useful_404_php”: true,
“useful_404_scanned_at”: “Thu, 07 Oct 2021 23:26:02 GMT”,
“visited_at”: “Tue, 26 Oct 2021 21:19:15 GMT”
}
]
The clear web “original” website appears to have almost identical services and pricing:
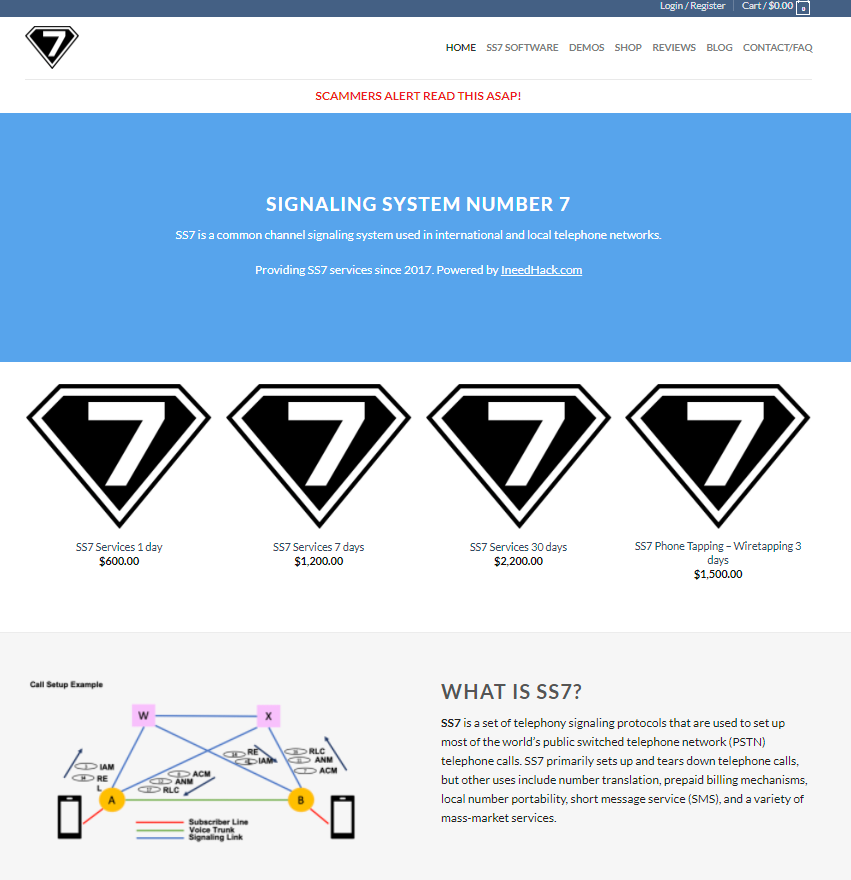 Screenshot of the “original” website.
Screenshot of the “original” website.
This supplier boasts a good reputation rating on securedhacks.com
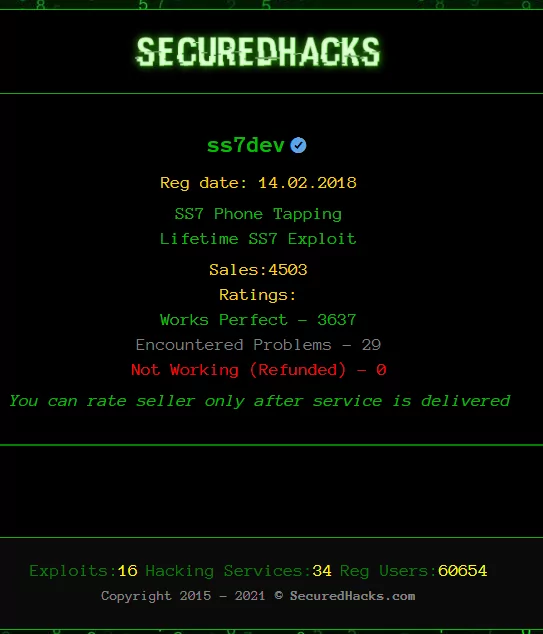 Secured Hacks
Secured Hacks
DarkFox Market
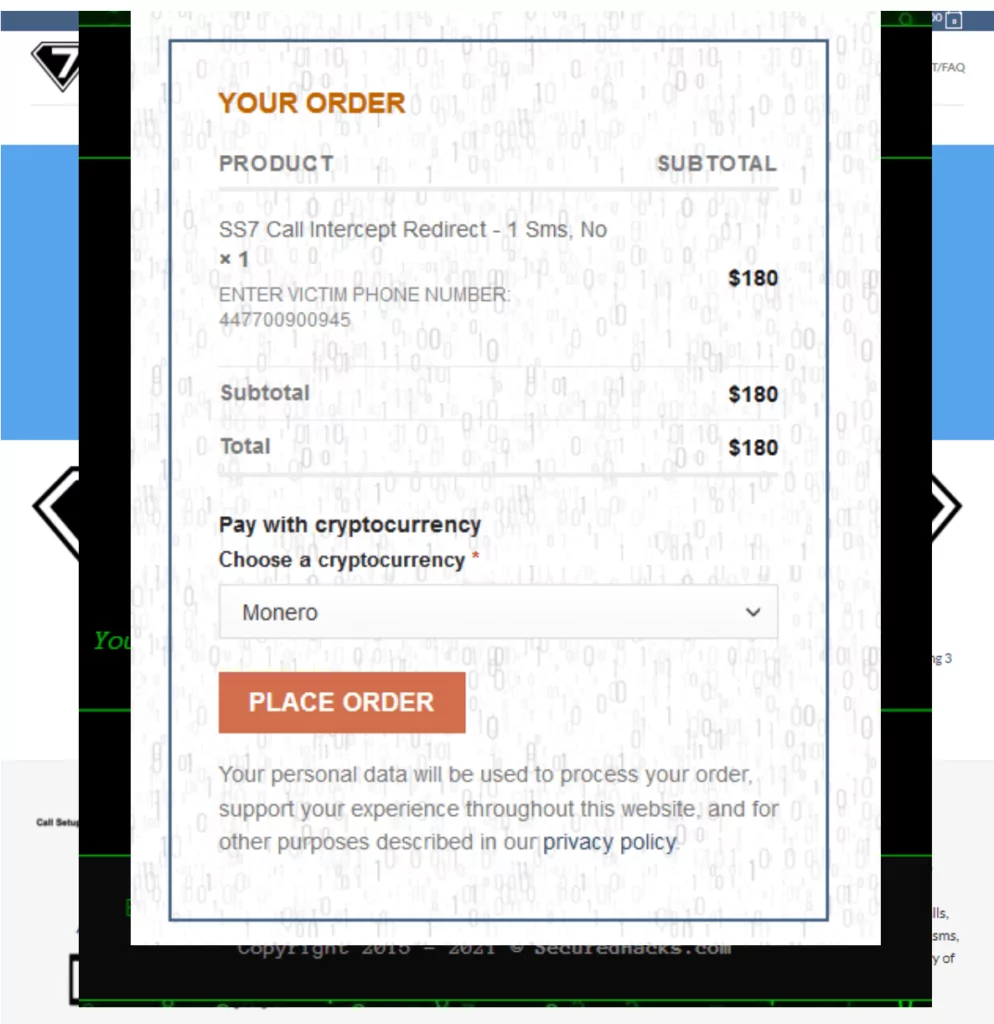
They appear to have a fairly e-commerce style webpage, payment is in either Bitcoin or Monero.
DarkFox Market appears to be a more “holistic” hacking service provider, offering a wider range of non SS7 services from DDoS to Ransomware As a Service.
The check out process requires you to enter your “victim’s” Phone number.
In terms of inbound and outbound links the DarkFox Market website has the most out of all the services seen so far,
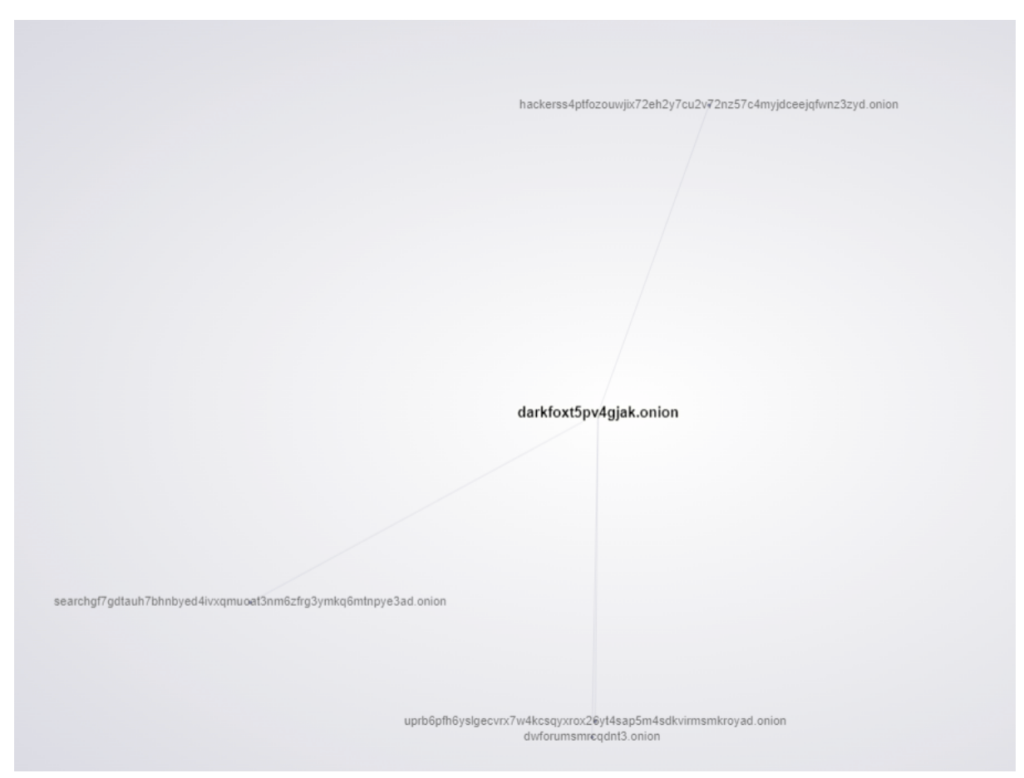 DarkFox DARKMAP links
DarkFox DARKMAP links
Inbound Links from:
uprb6pfh6yslgecvrx7w4kcsqyxrox26yt4sap5m4sdkvirmsmkroyad.onion “Dark Web Forums – “
dwforumsmrcqdnt3.onion “Dark Web Forums “
searchgf7gdtauh7bhnbyed4ivxqmuoat3nm6zfrg3ymkq6mtnpye3ad.onion “The Deep Searches “
Outbound Links to:
hackerss4ptfozouwjix72eh2y7cu2v72nz57c4myjdceejqfwnz3zyd.onion “DSM Hackers – All Hacking Tools And Services In One Place ”
The Proof videos on the DarkFox Proofs page for “Telegram hacking” show an SMS Intercept video. Part of this video actually shows a web portal similar to what’s shown on the SS7.dev “SS7 attack demos” web page! The video is actually stolen content from a journalist who wrote an article on this very attack back in June 2016, with the video along with a WhatsApp hack video uploaded originally in May 2016.
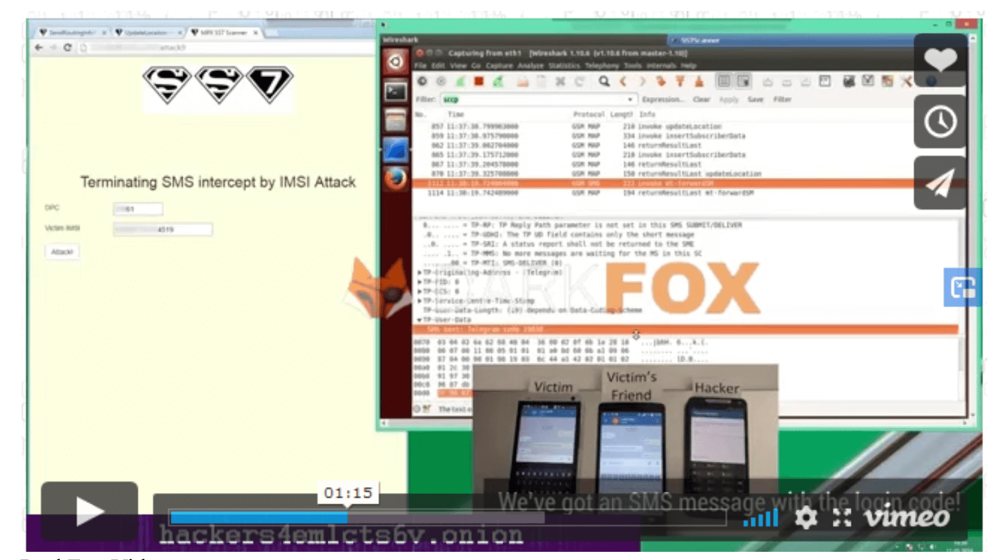 DarkFox Video
DarkFox Video
Original Youtube Video https://www.youtube.com/watch?v=dkvQqatURdM&t=1s
www[.]ss7[.]dev video analysis
Although not on the Dark Web the ss7.dev website carries probably the most ‘credibility’ out of all of the SS7 hacking services on the Dark Web.
The SS7.dev proof videos show web pages that look extremely similar to that of the original demo hack videos from 2016, with a distinctive “superman” SS7 logo however, the page background is white rather than a light yellow
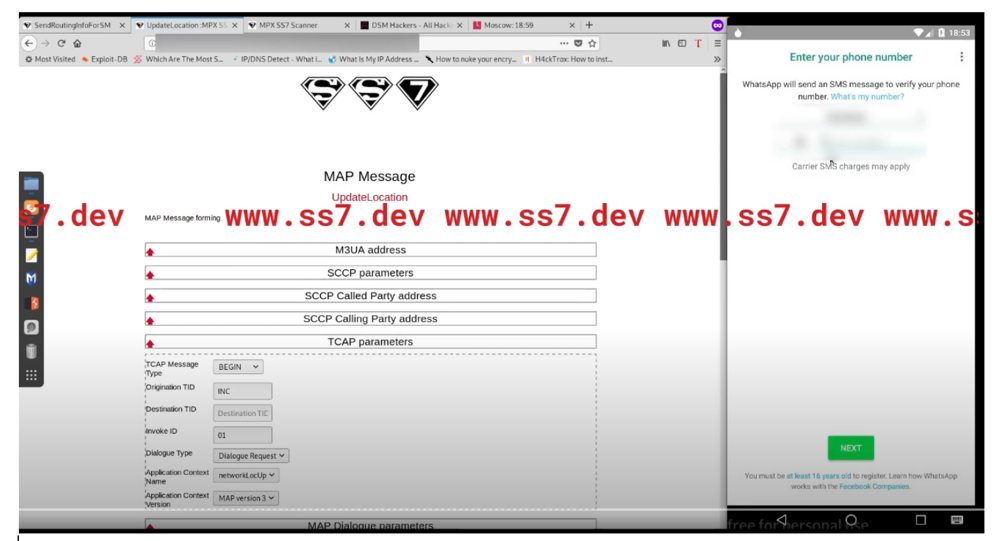 ss7.dev proof video uploaded 2nd August 2020
ss7.dev proof video uploaded 2nd August 2020
In one of the tabs from the proof video we see an open page to the DSM Hackers forum
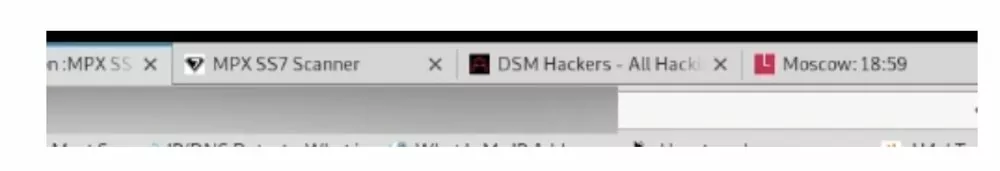 Proof video tabs
Proof video tabs
We know that this was one of the outbound links from the DarkFox market, although this could be coincidental, we are not quite sure of the relevance for the Moscow local time web page tab.
In the SS7.dev service demo video, the first 6 minutes are spent showing how to set up an account and pay for the services.
The most unconvincing of all the services, “SS7 Exploiter ” has to no surprise one of the most unconvincing demo videos. Like the SS7.dev, it spends the first nearly 3 minutes out of 5:23 showing how to buy bitcoin and pay for the service.
It then shows what is meant to be the supposed “SS7 Exploiter” CLI interface.
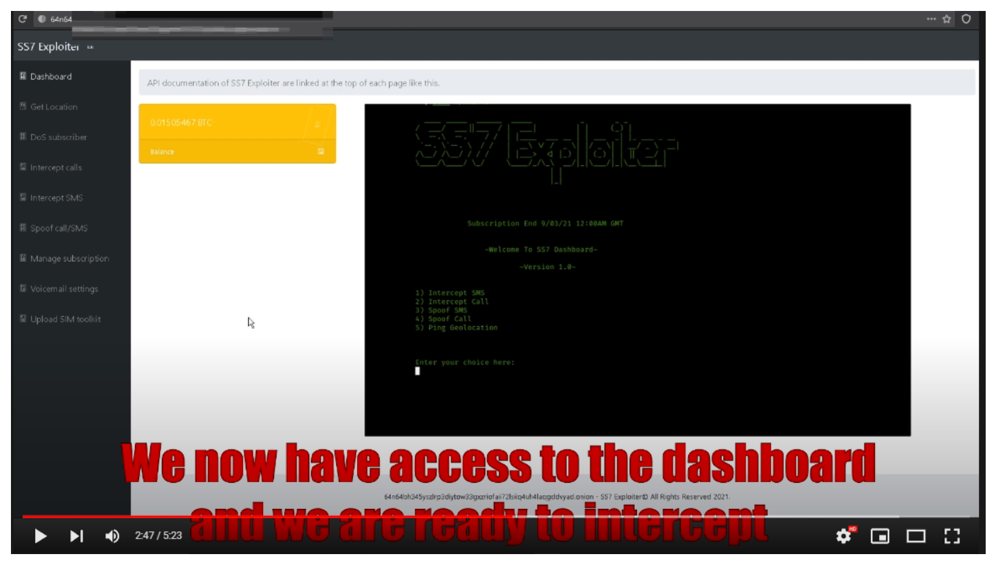 SS7 Exploiter Demo Video
SS7 Exploiter Demo Video
Note that this version of the web page, at the time of it being recorded does not show a demo video link in the navigation menu on the left hand side.
Note also the Subscription End date “9/03/21 12:00AM GMT”
If the operator purchased a subscription “out of their own pocket” of 1 Month then that would put the recording of the video at around the 9th of February assuming a DD/MM format.
Assuming a MM/DD format, this puts the recording at around the 3rd of August. The video itself was uploaded on the 16th of October 2021 to YouTube. It is possible that the video was re-uploaded, from an earlier time.
Interestingly looking back on our index history for this onion domain. We first added the domain to our index on the 23rd of July 2020 with pages crawled on the 27th and 4th of August 2020.
The demo.html page and link to it from the left navigation menu was only added to our index on the 18th of October 2021, a few days after the video is uploaded to Youtube.
With the entire website being originally mirrored by the HTTrack tool on the 13th of May 2019
Conclusion
There appear to be 4 main alleged SS7 Hacking/Exploitation services on the Dark Web, with one “SS7 Hack”, a clone of a clear web website “SS7.dev” being completely offline.
The other service appears to be a clone of another almost identical website offering a highly suspicious SS7 Exploiter service
With the last, DarkFox Market that offers more than just SS7 services showing nothing more than already stolen / faked videos.
With ironically the most ‘credible’ of all a clear web website, ss7.dev shows what appear to be spoofs / copies of SS7 hacking demos that were originally uploaded to YouTube back in May 2016.
Like most things on the Dark Web that promise a lot they are very likely all fake money making schemes for some one who is benefiting from all of those who failed to do even the smallest amount of due diligence, as they say Caveat Emptor.
Are there genuine SS7 hacking services on the Dark Web?
Most likely, but they are more than likely to be hidden behind membership only hacking services advertised by individuals for a very short period of time, an example of some posts related to SS7 hacking from our intelligence collection service:
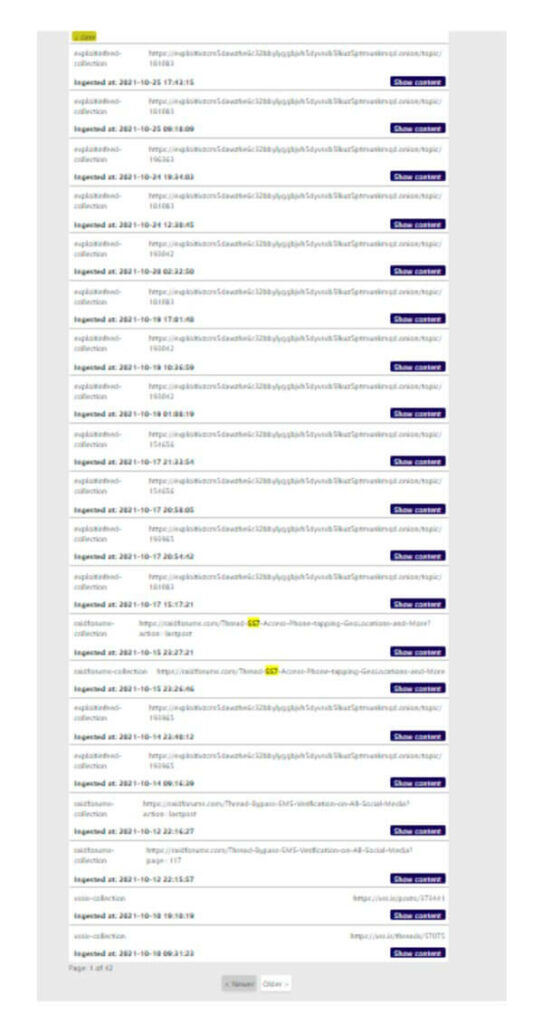 SOS Intelligence posts on SS7
SOS Intelligence posts on SS7
In any case it is very unlikely to find a long lived actual openly advertised service offering compromised SS7 gateway access
It would seem that there is a lot of interest in SS7 exploitation services but not a lot of genuine providers.
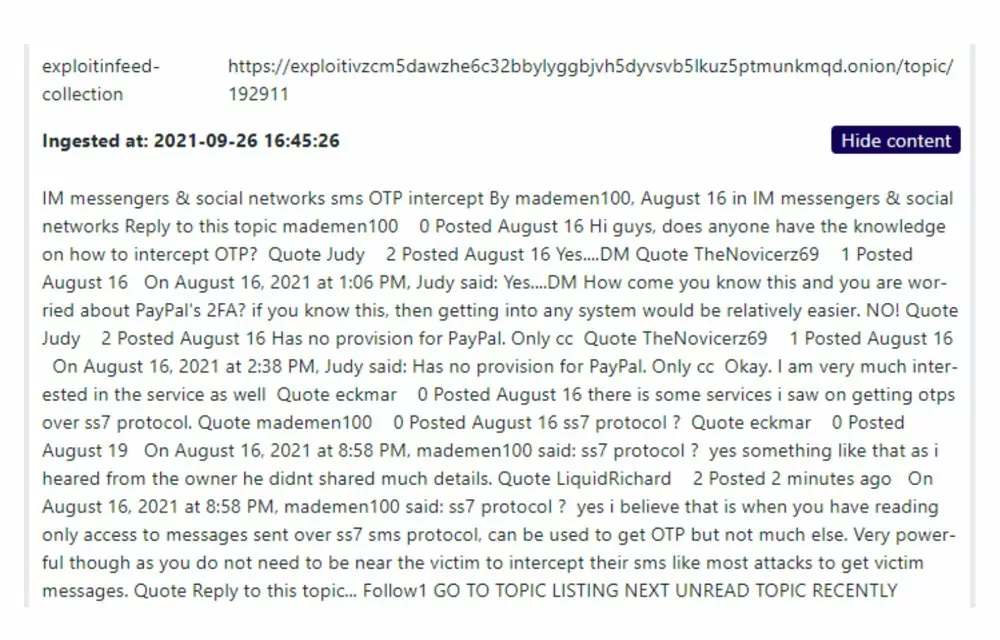 Exploit.in post about SMS OTP Interception
Exploit.in post about SMS OTP Interception
Of all of the fairly openly advertised services, clear web or dark we strongly believe to be complete fakes.
How much money could they have made?
Using the advertised bitcoin wallets and assuming they are not changing wallets with each transaction we can look at the Bitcoin blockchain explorer to see exactly when and how much bitcoin was sent these wallets
http://64n64bh345yszlrp3diytow33gxzriofaii72lsiiq4uh4laqgddvyad.onion/balance.html
3Dw3ZFDjVFCwn1siatB53ZbX2rWx7bYdaW
2x Transactions $159.62
http://vif4nngqgrdzjk7oavtolvw4uxhtzepog2y7piudinkjovhnnhav2pid.onion
38AFU5YCK8bjiNwoyRroGfLZbf4Tuh6a62
1x Transaction $10.09
DarkFox
It would appear that DarkFox e-commerce shop assigns a bitcoin wallet at time of transaction. It is difficult to tell if a wallet contains transactions specifically for SS7 hacking or other services. Upstream review of outbound transactions from these wallets reveal fairly large transactions suggesting that DarkFox is doing a reasonable amount of business.
1KU6c4ZuARpgypNMAdB4yDBxB873Yj5Bm8
2x Transactions $180.03
1DWX6ThGfVN8VNJiJPNhJiRjtXTxVFFvEf
4x Transactions $779.55
1CKvtyULCbf9iAeaxt7iuBSN7gChxcqqnz
2x Transactions $140.23
1MHXKbrCnBRQXTT5BTTJhLusGTQcxXNpmz
2x Transactions £319.50
http://3zx4rwy3izy2zhywz2vm5krc2zqmrahc7sv7ps2ekqvfxv62skueruid.onion/balance.html
3Qp7cTaLm2hnzsx8fYaTM76GWynM1YMZ4d
1x Transaction $389.57
32Gbi2p66PdyzZXpW2VxHk8jrWaCtBRcz7
No Transactions.
Featured image Photo by Mario Caruso on Unsplash















![Toni Kroos là ai? [ sự thật về tiểu sử đầy đủ Toni Kroos ]](https://evbn.org/wp-content/uploads/New-Project-6635-1671934592.jpg)


