Access Control Models – Westoahu Cybersecurity
Access Control Models
By Robert Townsend on November 21, 2018
Background –
Considered one of the most crucial assets in a company, access control systems hold significant value. The term ‘access control’ refers to “the control of access to system resources after a user’s account credentials and identity have been authenticated and access to the system has been granted.” Access control is used to identify a subject (user/human) and to authorize the subject to access an object (data/resource) based on the required task. These controls are used to protect resources from unauthorized access and are put into place to ensure that subjects can only access objects using secure and pre-approved methods. Three main types of access control systems are: Discretionary Access Control (DAC), Role Based Access Control (RBAC), and Mandatory Access Control (MAC).
Discretionary Access Control (DAC) –
DAC is a type of access control system that assigns access rights based on rules specified by users. The principle behind DAC is that subjects can determine who has access to their objects. The DAC model takes advantage of using access control lists (ACLs) and capability tables. Capability tables contain rows with ‘subject’ and columns containing ‘object’. The security kernel within the operating system checks the tables to determine if access is allowed. Sometimes a subject/program may only have access to read a file; the security kernel makes sure no unauthorized changes occur.
Implementation –
This popular model is utilized by some of the most popular operating systems, like Microsoft Windows file systems.
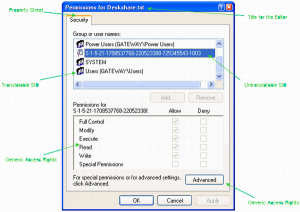
Figure 1 – https://www.codeproject.com/Articles/10811/The-Windows-Access-Control-Model-Part-4
Role-Based Access Control (RBAC) –
RBAC, also known as a non-discretionary access control, is used when system administrators need to assign rights based on organizational roles instead of individual user accounts within an organization. It presents an opportunity for the organization to address the principle of ‘least privilege’. This gives an individual only the access needed to do their job, since access is connected to their job.
Implementation-
Windows and Linux environments use something similar by creating ‘Groups’. Each group has individual file permissions and each user is assigned to groups based on their work role. RBAC assigns access based on roles. This is different from groups since users can belong to multiple groups but should only be assigned to one role. Example roles are: accountants, developer, among others. An accountant would only gain access to resources that an accountant would need on the system. This requires the organization to constantly review the role definitions and have a process to modify roles to segregate duties. If not, role creep can occur. Role creep is when an individual is transferred to another job/group and their access from their previous job stays with them.

Figure 2 – https://www.docops.ca.com/ca-identity-governance/12-6-02-cr1/EN/getting-started/access-governance-and-rbac
Mandatory Access Control (MAC) –
Considered the strictest of all levels of access control systems. The design and implementation of MAC is commonly used by the government. It uses a hierarchical approach to control access to files/resources. Under a MAC environment, access to resource objects is controlled by the settings defined by a system administrator. This means access to resource objects is controlled by the operating system based on what the system administrator configured in the settings. It is not possible for users to change access control of a resource. MAC uses “security labels” to assign resource objects on a system. There are two pieces of information connected to these security labels: classification (high, medium, low) and category (specific department or project – provides “need to know”). Each user account is also assigned classification and category properties. This system provides users access to an object if both properties match. If a user has high classification but is not part of the category of the object, then the user cannot access the object. MAC is the most secure access control but requires a considerable amount of planning and requires a high system management due to the constant updating of objects and account labels.
Implementation-
Other than the government’s implementation of MAC, Windows Vista-8 used a variant of MAC with what they called, Mandatory Integrity Control (MIC). This type of MAC system added integrity levels (IL) to process/files running in the login session. The IL represented the level of trust the object would have. Subjects were assigned an IL level, which was assigned to their access token. IL levels in MIC were: low, medium, high, and system. Under this system, access to an object was prohibited unless the user had the same level of trust, or higher than the object. Windows limited the user to not being able to write or delete files with a higher IL. It first compared IL levels, then moved on to checking the ACLs to make sure the correct permissions are in place. This system took advantage of the Windows DAC system ACLs and combined it with integrity levels to create a MAC environment.
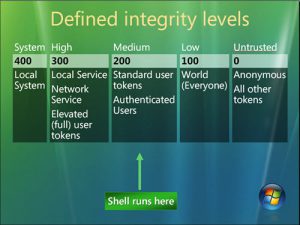
Figure 3 – https://www.thewindowsclub.com/mandatory-integrity-control
Conclusion –
Access controls are used to prevent unauthorized access to system resources. By implementing access control systems that fit your organization, you can better manage your assets. DAC, RBAC, and MAC access control systems are models that have been used to create access control systems that provide reliability and security. Businesses with smaller applications will find DAC to be easier to implement. Others with highly confidential or sensitive information may decide to use RBAC or MAC systems.
Sources –
https://www.tedsystems.com/3-types-access-control-which-right-building/
https://www.stor-guard.com/article/types-of-access-control-systems-for-effective-personnel-security-43
https://searchsecurity.techtarget.com/feature/CISSP-online-training-Inside-the-access-control-domain
https://searchsecurity.techtarget.com/definition/mandatory-access-control-MAC
https://resources.infosecinstitute.com/cissp-access-control-domain/#gref
https://www.techotopia.com/index.php/Mandatory,_Discretionary,_Role_and_Rule_Based_Access_Control
https://searchdatacenter.techtarget.com/answer/DAC-and-MAC-safety
http://www.cs.cornell.edu/courses/cs5430/2015sp/notes/dac.php















![Toni Kroos là ai? [ sự thật về tiểu sử đầy đủ Toni Kroos ]](https://evbn.org/wp-content/uploads/New-Project-6635-1671934592.jpg)


