7 Best Intrusion Detection Software – IDS Systems – DNSstuff
Safeguarding the security of your IT infrastructure is no easy task. There are so many components to protect, and no firewall is entirely foolproof. Cyberattacks are constantly evolving, with the express intention of breaching your defenses and compromising your systems, and more come to light every day. Keeping pace with these developments requires your security solution to be adaptable and comprehensive.
An intrusion detection system (IDS) is a vital element of a truly successful solution. It flags up inbound and outbound malicious traffic, so you can take proactive steps to safeguard your network. An effective IDS keeps your IT personnel informed, so they can respond rapidly and with precision to a potential threat.
In this guide, I’m going to walk you through the basics of intrusion detection software, following up with a list of my favorite tools. If you want an enterprise-grade program, you can’t do better than SolarWinds® Security Event Manager. This tool is feature-rich and user-friendly and incorporates a cyberthreat intelligence framework to make intrusion detection fast, easy, and accurate.
To learn more about how I reached this conclusion, and how my other favorite tools compare, check out my list.
Feel free to jump ahead to each tool review:
Mục Lục
What Is an Intrusion Detection System (IDS)?
An intrusion detection system, IDS for short, monitors network and system traffic for any suspicious activity. Once any potential threats have been identified, intrusion detection software sends notifications to alert you to them. The latest IDS software will proactively analyze and identify patterns indicative of a range of cyberattack types. An effective solution should be able to discover any threats before they fully infiltrate the system.
Firewalls and anti-malware programs are just one small part of a comprehensive approach to security. When a network grows, and unknown or new devices regularly jump in and out, you need intrusion detection software. This software should be capturing snapshots of your whole system, using knowledge of potential intrusions to proactively prevent them. Intrusion detection system software is usually combined with components designed to protect information systems as part of a wider security solution. A full-fledged security solution will also feature authorization and authentication access control measures as part of its defense against intrusion.
While this is the basic function and purpose of intrusion detection software, not all programs are created equal. Some let you implement rules, which the program then uses to inform and execute certain actions and tasks, while others do not. Open-source IDS options are also available, which can differ significantly from closed source software, so it’s important to understand the nuances of an open-source network intrusion detection system before choosing it.
The latest IDS software programs are likely to include specialist and advanced features, so it’s worth considering how useful these more sophisticated components would be to your business. After all, it may not be cost-effective for an organization with minimal network intrusion detection requirements to choose the most advanced and latest IDS software.
Before getting into my favorite intrusion detection software, I’ll run through the types of IDS (network-based and host-based), the types of detection methodologies (signature-based and anomaly-based), the challenges of managing intrusion detection system software, and using an IPS to defend your network.
Back to top
Types of IDS
An intrusion detection system comes in one of two types: a host-based intrusion detection system (HIDS) or a network-based intrusion detection system (NIDS). To put it simply, a HIDS system examines the events on a computer connected to your network, instead of examining traffic passing through the system. As its name suggests, it’s based around the host. A NIDS, on the other hand, examines the network traffic.
Network-Based Intrusion Detection System (NIDS)
As a system that examines and analyzes network traffic, a network-based intrusion detection system must feature a packet sniffer, which gathers network traffic, as standard. Though NIDSs can vary, they typically include a rule-based analysis engine, which can be customized with your own rules. In some cases, NIDSs have a user community producing rules you can import directly, to save you time. It may take some time to get familiar with the rule syntax of your chosen NIDS and being able to import from the user community can make the initial NIDS implementation feel like less of a steep learning curve.
NIDS rules also facilitate selective data capture. This is necessary because if you were to feed all your traffic into files or run it through a dashboard, data analysis would be pretty much impossible. So, if you have a rule designed to flag up suspicious HTTP traffic, your NIDS will filter out irrelevant data and only store HTTP packets with specific characteristics. This keeps the system from being overwhelmed.
A NIDS program usually gets installed on a specific piece of equipment. The high-end, enterprise-grade solutions typically come in the form of a network kit with the program built in. A NIDS requires a sensor module for picking up traffic, but you don’t necessarily need to pay out for expensive hardware. You could load a sensor module onto a LAN analyzer or specify a device to run the task. Just ensure the device you choose has enough clock speed; otherwise it will cause your network to lag.
Host-Based Intrusion Detection System (HIDS)
Instead of examining the traffic, host-based intrusion detection systems examine the events on a computer connected to your network, by looking into admin file data. This usually includes configuration and log files. A HIDS will back up your configuration files, so you can restore previous settings if a virus affects system security by altering the device setup. You’ll also want to defend yourself against root access on Unix-like platforms or Windows system registry changes. A HIDS can’t block these alterations, but it should notify you so you can act to rectify or prevent them.
Hosts monitored by HIDSs must have software installed. Your HIDS can monitor just one device if you’d like, but it’s common to install a HIDS on every piece of equipment connected to your network. This prevents any configuration changes on devices from being overlooked. However, if you have a HIDS on every device, logging in to each one individually to access data is time-consuming and labor-intensive. That’s why you’ll need a distributed HIDS system with a centralized console or control module, so you can view the feedback for each host from one location. It is important for the system you choose to encrypt the information passing between the hosts and the centralized console.
NIDS vs. HIDS
So, should you opt for a NIDS or a HIDS? The short answer: you should probably have both. A NIDS gives you far more monitoring capacity than a HIDS can, allowing you to intercept cyberattacks in real time. A HIDS, on the other hand, is only able to identify if something is wrong once a setting or file has already been altered. By combining these two systems, you can achieve a preventive and responsive solution. Having a HIDS is important because HIDS activity is less aggressive than NIDS activity—for a start, a HIDS should not use as much CPU. Neither type of system generates network traffic.
Back to top
Types of Intrusion Detection Methodologies
Both a host-based intrusion detection system and a network-based intrusion detection system will have two modes of operation: signature-based and anomaly-based. Almost all IDSs use both modes, though some may only use one or the other.
Signature-Based IDS
The signature-based approach to IDS focuses on identifying a “signature” of an intrusion event. This could be in the form of a known identity, or perhaps a pattern. Most IDSs use the signature-based approach.
For this mode to be successful, it needs to be updated regularly, so it understands which identities and signatures are common. These identities and signatures are changing and evolving. In other words, if an attacker changes details about how the attack is executed regularly enough, they may be able to evade the attention of a signature-based IDS, because the IDS cannot keep up with the alterations. Brand-new attack types may also slip through, because they don’t yet exist in the IDS database. Bear in mind, as the database grows, the processing load gets higher.
Anomaly-Based IDS
Anomaly-based detection, as its name suggests, focuses on identifying unexpected or unusual patterns of activities. This method compensates for any attacks that slip past the signature-based model’s pattern identifying approach. However, previously unknown but nonetheless valid behavior can sometimes be flagged accidentally.
Anomaly-based IDS is good for identifying when someone is sweeping or probing a network, which can provide a strong indication of an imminent attack. Examples of an anomaly include multiple failed login attempts and unusual port activity.
With NIDSs, an anomaly-based approach means you will need to establish a behavior baseline, so the system knows what’s considered “standard” activity. This assists the system in flagging anything that does not fit in, or that would be considered abnormal.
Signature-Based vs. Anomaly-Based IDS
The signature-based methodology tends to be faster than anomaly-based detection, but ultimately a comprehensive intrusion detection software program needs to offer both signature and anomaly procedures. This is because there are merits and disadvantages to both signature-based and anomaly-based intrusion detection software, which are largely compensated for when the two are combined.
Back to top
How to Use an IPS
IPS is short for “intrusion prevention system.” IPS and IDS software are branches of the same tree, and they harness similar technologies. Detection facilitates prevention, so IPSs and IDSs must work in combination to be successful.
The key difference between these intrusion systems is one is active, and the other is passive. A typical intrusion monitor alerting you when something is unusual or suspicious might be referred to as a passive IDS. A system that detects and acts to prevent damage and further attacks would be referred to as reactive. This is because it reacts to the intrusion rather than merely identifying it.
A reactive IPS or IDS does not typically implement solutions itself but communicates with applications and firewalls by tweaking their settings. A reactive HIDS can communicate with multiple network aids, with the aim of restoring device settings. This could be SNMP settings, or the settings of a configuration manager installed on the device. If an attack is launched on the administrator, this cannot be responded to with an automatic block on admin use, or by altering the password for the system. This is because doing so would lock the root user out of the servers and network.
IDS users sometimes complain they get floods of false positives when they first set up the IDS. Your IPS will implement a defense strategy automatically, based on the detection of alert conditions and thresholds. If the IPS isn’t calibrated correctly, this can cause chaos and result in your authentic network activity halting entirely.
You can reduce the number of false positives, and minimize disruption to the network, by implementing your IDS and IPS in stages. You can customize triggers, combine warning conditions, and create tailored alerts. By combining conditions, they become more complex, which can reduce the likelihood of false positives occurring.
It’s difficult, however, to eradicate false positives entirely without risking suspicious activity slipping through your defenses. You should aim for striking a fair balance, without compromising your security. Intrusion detection and prevention processes should be able to interact with firewalls in a fine-tuned way, to ensure genuine users aren’t locked out and authentic network activity is not disrupted.
Challenges of Managing an IDS
There are three main challenges associated with managing an IDS. When choosing your intrusion detection software, look for a program that minimizes these challenges as much as possible.
- Identifying false positives. The first challenge concerns the identification of false positives, which I’ve already addressed in part. False positives can put pressure on IT teams, who must update their IDS continually, so it has the information required to detect genuine threats and distinguish those threats from genuine traffic. This is a constant battle against false positives, which is time-consuming and labor-intensive. If the IDS is not up to date and suitably fine-tuned, which takes a lot of time in and of itself, then more time is lost coping with false positives.
Many organizations use a secondary analysis platform, like a security incident and event manager, to help them analyze and investigate alerts in a more efficient way. Essentially, when an IDS generates an alert, it’s sent to the secondary analysis system, which helps contend with the issue of false positives. - Staffing. The second issue is staffing. Understanding the context of threats and suspicious activity is an extremely important aspect of IDS management. The wider context is changing every day, as cybercriminals try to keep pace with security software. In addition, every IDS is implemented within the specific context of the organization in question.
To manage the complexities of the business-specific context and the wider context, you must have access to a knowledgeable and trained system analyst. The IDS analyst will tailor the IDS to the context but finding someone who has the credentials and experience to do this effectively is no easy task. - Identifying genuine risks. False positives can be time-consuming and cumbersome but missing a legitimate threat can be worse. With an IDS, you have to know the nature of the attack to identify and prevent it. Experts refer to this as the “patient zero” problem: someone has to get sick before you can identify the illness in the future.
These are the three key challenges intrusion detection software is always trying to combat. Some tools do this better than others. Read on to check out the intrusion detection software programs I’ve found to be the most effective at managing these challenges.
Back to top
Best Intrusion Detection System Software
The best intrusion detection system software has to be able to manage the three challenges listed above effectively. It also has to be designed in an intuitive and user-friendly way, to reduce the amount of time and labor spent on intrusion detection and prevention. The following tools are the best of the best, with SolarWinds Security Event Manger (SEM) coming out on top.
SEM, which combines intrusion detection system software with intrusion prevention measures, is sophisticated and easy to use, capable of responding to events, and useful in achieving compliance. This highly versatile tool strips intrusion detection of its difficulty and complexity as much as possible. Keep reading to find out how my other picks measure up.
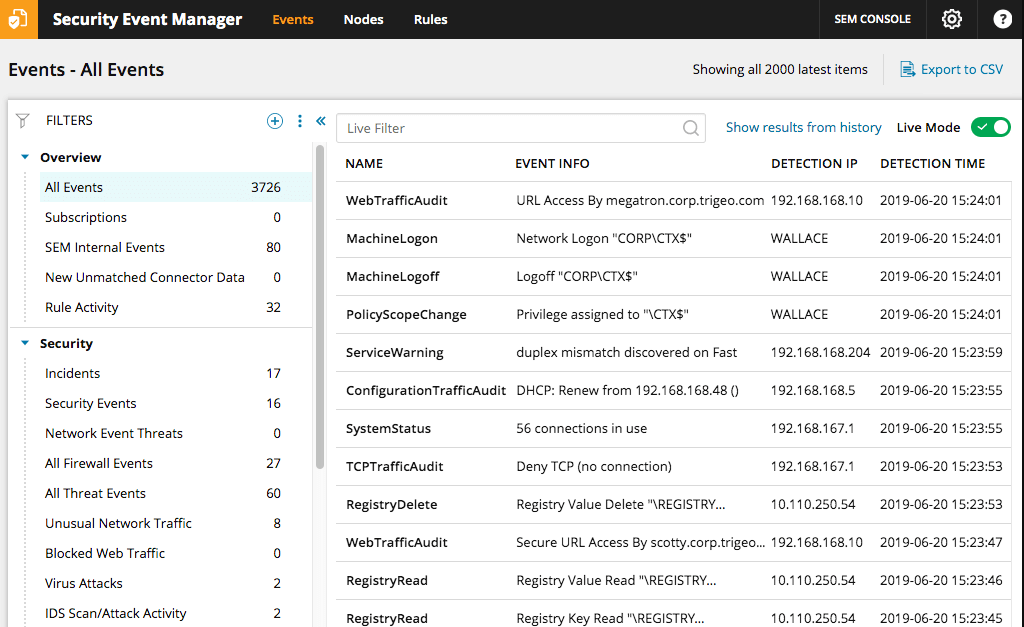
SolarWinds Security Event Manager (SEM) takes a highly intelligent approach to threat detection. By collecting network intrusion detection system logs, SEM collates information on attack types and amounts. This information is then integrated with other infrastructure logs, creating a vast network of data to contribute to threat detection. This data is constantly optimizing the security systems and processes of your IDS or informing the creation of more efficient procedures better equipped to protect your network. With SEM, you can identify problematic devices on the network, use the data to create risk assessment reports for stakeholders, and identify highly advanced threats before they wreak havoc on your system.
As is clear from the first part of this guide, manual network intrusion detection can be exhausting. And no matter how hard you work, the system will never be entirely foolproof. You’re in a race against constantly evolving threats and managing them manually is an uphill battle.
SEM uses native technology to save you time that would otherwise be spent performing routine tasks. It does this by monitoring and alerting you to any suspicious events or activities, and by acting automatically when specific events are detected. It deploys network sensors to assist with detecting intrusions, conducts data analysis, identifies services being consumed, and automates asset discovery. By automating the process wherever possible, these capabilities reduce the need for you to manually detect and respond to threats and suspicious activity.
SEM also helps you demonstrate compliance. The IDS solution SEM provides is network-based, which gives you maximum visibility into your network. You receive detailed information, which can be packaged into hundreds of out-of-the-box reporting templates. This makes standard reporting processes quick and easy. Moreover, you can customize these reports to suit the specific needs of your business, and schedule reports to be delivered to stakeholders.
Network intrusion detection software is only as good as its console. If a program isn’t user-friendly, then it doesn’t matter how sophisticated or feature rich it is, because the average user won’t be able to interact with the system. SEM, despite offering some seriously advanced utilities, is one of the most user-friendly programs on this list. Its interface is simple, with events, nodes, and rules accessible in the top bar. All the tabs are super quick to navigate, and data is presented in a graphical, easy-to-read way. The dashboard is colorful, uncluttered, and dynamic.
SolarWinds offers a 30-day free trial of SEM, which you can access by inputting a few of your details. You will then receive a link to the free trial. SEM is available for Windows, Unix, Linux, and Mac OS.
Back to top
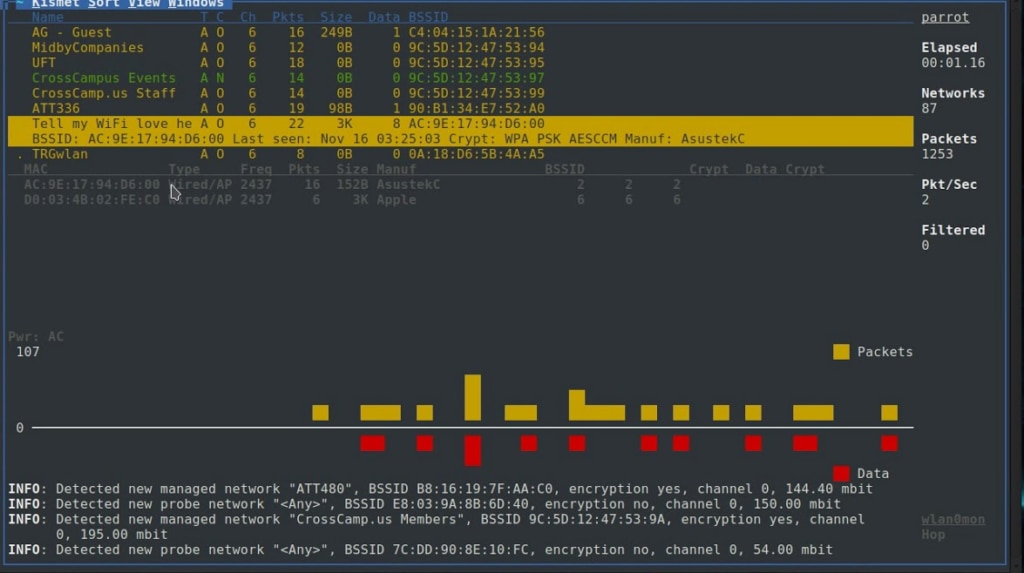
If you’re looking for an open-source IDS, Kismet might be a good option for you. Kismet is a wireless IDS, which means it focuses on wireless protocols like Bluetooth and Wi-Fi. This program tracks down and exposes unauthorized access points, which are more common than you might think. Unauthorized access points can be created accidentally by employees surprisingly easily. Kismet detects configuration gaps and default networks, hopping channels to extend its range.
One of the best things about Kismet its extended plugin support. You can use plugins to extend the web user interface functionality via browser-side enhancements and JavaScript, as well as server functionality at the low level, and incorporate external tools. Kestrel is a popular Kismet plugin for adding live mapping functionalities to the Kismet interface. It uses a leaflet library and overlays device and network locations on a live map. Pin grouping is used for dense areas on the map.
IoD Screwdriver is another useful plugin, although it features more advertising than I’d like. There’s also a report generator plugin for grouping devices by SSID or BSSID, with the ability to export to CSV or PDF. As an open-source IDS, Kismet has a community of users who are continually adding to these plugins.
Being able to connect with the community is another benefit of Kismet. You can chat with members of the Kismet community on Discord and on IRC. This means support is easily accessible.
The main drawback of Kismet is that it can take a while to search networks. It can run on Android and iOS, but its support for Windows is limited. Though it’s impressive in many ways, it’s worth noting an open-source network intrusion detection system can’t offer the same level of sophistication and dependability as closed-source tools. This usually means open-source IDS tools are not especially well suited to business use.
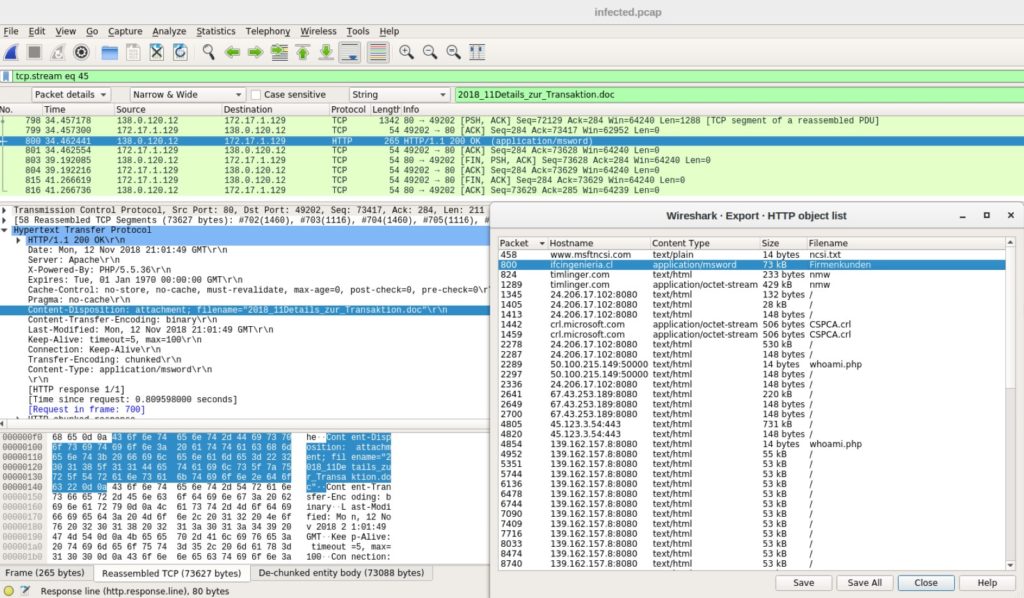
Zeek is the new name for the Bro system, and certain components retain the “Bro” name. This network security monitor distinguishes itself from traditional IDSs in a number of ways. This open-source network intrusion detection system uses a domain-specific scripting language, which facilitates site-specific monitoring policies and makes it highly adaptable as an IDS tool. It exchanges information in real time by interfacing with other applications, logs activity stored in a high-level archive, and features analyzers for numerous protocols, so you can conduct semantic analysis at the application layer.
Zeek is driven by a powerful analysis engine that converts traffic into a series of events, proactively detecting anomalies and suspicious signatures. You can create tasks for the policy engine, meaning you can customize what’s automated and what’s not. You could, for example, set the tool up to automatically download suspicious files identified on the network, send them to be analyzed, notify relevant team members if there’s an issue, backlist the source, and shut down the device that conducted the download.
With Zeek you can track DNS, HTTP, and FTP activity. You can also monitor SNMP traffic, which enables you to check SNMP trap conditions and any changes to device configurations. Event data mining is performed by policy scripts. Each policy is essentially a collection of rules, and you can have as many active policies or protocol stack layers as you want. Zeek functions as a network traffic analyzer and an intrusion prevention system, with alert conditions provoking predefined actions. Policy scripts are customizable, but they’re limited by the standard framework, which involves anomaly detection, analysis of connections, and signature matching.
This is a surprisingly flexible tool: it doesn’t restrict users to a specific detection methodology, nor does it depend on traditional signatures. As an open-source IDS, Zeek comes with a BSD license, which means it’s free to use and has barely any restrictions on it. The biggest issue with this tool is it comes with a steep learning curve, so it isn’t particularly friendly to the average user. To make the most of it, you’ll have to take the time to teach yourself.
Back to top
OpenDLP is an open-source program with a focus on data loss prevention (DLP). This tool scans database and file system data at rest and searches for sensitive organizational data to expose unauthorized data transmission or data replication. It can identify sensitive data at rest on thousands of Unix systems, MySQL databases, Microsoft Windows systems, and Microsoft SQL databases. All of this is conducted from a centralized web application.
OpenDLP is effective at finding malicious insiders and identifying employees who are making frequent mistakes, like sending out data when they’re not authorized to do so. This tool supports Linux and Windows, and it can be deployed as an agentless program or via agents. There are two main OpenDLP components. The web application component manages Windows agents and Windows/database/Unix agentless scanners. The second component is a Microsoft Windows agent, which can perform rapid scans of thousands of systems at once. Agentless database scans can be implemented on MySQL and Microsoft SQL Server databases.
The disadvantage of this program is, like most open source IDS tools, it’s not especially suitable for enterprise-grade requirements. The installation process isn’t intuitive, and the application requires manual intervention.
Sagan is another open-source network intrusion detection system, featured in my list of favorites because it offers high performance and real-time log analysis. Sagan is powered by a robust analysis and correlation engine running under *nix operating systems, so it’s available for FreeBSD, Linux, and OpenBSD, among others. I like Sagan because it uses a multi-threaded architectural approach to facilitate optimal performance levels.
This application was designed so its structure and rules function similarly to those of Suricata IDS/IPS (which will feature later in my list) and Snort, because this assists in maintaining compatibility with rule management software like Oinkmaster, PulledPork, and others. This similarity also means you can correlate log events with a Suricata or Snort system. Sagan can write to Snort databases and is compatible with Suricata and Snort consoles.
I like this tool because it’s lightweight, using minimal CPU and memory resources; is compatible with common graphical-base security consoles (like EveBox, Sguil, BASE, and Snorby); and can monitor usage based on time of day. Sagan also features an IP locator, which lets you view the geographical locations of detected IP addresses. This insight helps you aggregate IP address actions appearing to be working together to launch an attack.
Sagan enables script execution upon detection of an event, log normalization, automatic firewall, multi-line log support, and alerting. The highly feature-rich program supports both the syslog protocol and NXLog, for sending Sagan Microsoft Windows logs. It also supports multiple output formats.
The disadvantage of this tool is that, being open-source, it’s not suited for enterprise use, and it can take a while to learn how to make the most of it. It could even be argued there are too many features, which overcomplicates the program. Sagan is generally considered to be a log analyzer, so it’s often overlooked as a potential IDS solution. However, its combination of HIDS and NIDS approaches means it functions well as a hybrid IDS tool.
Back to top
Suricata is a very sophisticated, seriously fast, free open-source IDS. It can conduct real-time intrusion detection, inline intrusion prevention, offline pcap processing, and network security monitoring. By combining IDS with IPS, it’s highly effective as a security tool.
With its extensive rules and signature language, Suricata can investigate network traffic. It offers Lua scripting support, which assists with detecting especially complex and advanced threats. Suricata supports all standard output and input formats and can be easily integrated with other databases (like Splunk, Logstash, and Kibana).
Like many open-source programs, Suricata is community-driven, meaning it’s constantly being developed by the users, for the users. This approach is great for facilitating continuous improvement, because customer feedback directly informs how the program evolves and changes.
Suricata focuses on efficiency, usability, and security. These are the three pillars of its evolution. And for an open-source program, it’s surprisingly user-friendly. The dashboard is dynamic yet simple, and data is represented in the form of pie charts, dials, and bar graphs. This makes data easier to interpret and keeps the interface from looking cluttered, making it easy to navigate.
This tool collects data at the application layer, which prevents blindness to signatures split over multiple TCP packets. Suricata postpones moving information over to analysis until the packets have been assembled. Though Suricata functions at the application layer, it can also monitor activity on the lower levels—this includes TLS, UDP, TCP, ICMP, and IP. This is a highly intelligent monitor, because it doesn’t just observe the structure of the packets. It also examines TLS certificates, with a focus on DNS calls and HTTP requests. Files can even be extracted, so you can isolate and examine them.
Suricata uses both anomaly-based and signature-based detection methods. Its clever processing architecture uses multiple processes for multi-threaded, simultaneous activities, which accelerates hardware. It can run on your graphics card, in part, and distributes tasks to keep single hosts from bearing the full load. This is a welcome feature, because Suricata can unfortunately be heavy on processing.
Lastly, we have Security Onion. This tool is an open-source, free Linux distribution designed for log management, intrusion detection, and enterprise security monitoring. Security Onion is essentially a suite of security tools, each popular in their own right; these include Snort, Kibana, Zeek, Wazuh, CyberChef, NetworkMiner, Suricata, and Logstash. The benefit of this approach is, of course, it makes the tool highly comprehensive and versatile, covering pretty much every aspect of IT security. The problem with a suite of tools, however, is it’s difficult to streamline their integration and compatibility. Because of this, a unified solution is sometimes preferable.
Another problem with collections of tools is setting them up can be complicated. This isn’t an issue with Security Onion, because its setup wizard makes it easy to get up and running.
Security Onion is a NIDS/HIDS hybrid written to run on Ubuntu but can integrate front-end system elements and analysis utilities. It offers both signature-based and anomaly-based alert rules, and provides you with ample device status information, as well as insight into traffic patterns.
The reason Security Onion hasn’t ranked higher on this list is because, though the individual tools included are impressive, collectively they can become overwhelming. Some of the tools have overlapping utilities and navigating between tools is tricky. Unfortunately, Security Onion lacks action automation.
In some instances, like on the “Dashboard Overview” tab, this tool’s front end looks sophisticated and well designed. In other instances, like under “Views,” however, data is cluttered and difficult to read. This is a notable disadvantage, in part because the interface lacks consistency, but also because it means key data is sometimes hard to interpret.
How to Choose the Best Intrusion Detection System
Hopefully this guide has given you insight into how intrusion detection systems work, and how the latest IDS software measures up. There are several challenges associated with intrusion detection system management, particularly because the threats to IT infrastructure are constantly evolving. As security technology advances, so too do cyberattacks, meaning they’re difficult to predict and prevent. However, with the right tool supporting your business and your IT team, you can effectively combat the false positives, staffing issues, and overlooked threats any IDS system comes up against.
Overall, SolarWinds Security Event Manager stands out as the most versatile, user-friendly, and flexible program. Its user interface has been cleverly designed, making the dashboard easy to navigate and data interpretation simple and fast. As a closed-source program, it’s highly dependable and suited to enterprise-grade requirements, which means it can cope with the weight of your business’s expectations. Setting up SEM is quick and easy, and a 30-day free trial is available.















![Toni Kroos là ai? [ sự thật về tiểu sử đầy đủ Toni Kroos ]](https://evbn.org/wp-content/uploads/New-Project-6635-1671934592.jpg)


