5G Security explained: 3GPP 5G core network SBA and Security Mechanisms – Technology Blog
by Akash Tripathi with Alan J Weissberger
Introduction:
5G networks were deployed in increasing numbers this past year. As of December 2021, GSA had identified 481 operators in 144 countries or territories that were investing in 5G, up from 412 operators at the end of 2020. Of those, a total of 189 operators in 74 countries/territories had launched one or more 3GPP-compliant 5G services, up by 40% from 135 from one year ago.
Despite 5G’s much advertised potential, there are significant security risks, especially with a “cloud native” service based architecture, which we explain in this article.
New 5G services, functions and features have posed new challenges for 5G network operators. For example, bad actors could set up “secure” wireless channels with previously issued 5G security keys.
Therefore, it’s imperative for 5G operators to address end-to-end cyber security, using an array of novel techniques and mechanisms, which have been defined by 3GPP and (to a much lesser extent) by GSMA.
5G Security Requires 5G SA Core Network:
It’s important to distinguish between 5G NSA network security (which use 4G security mechanisms and 4G core network/EPC) vs. 5G SA network security (which uses 5G core network serviced base architecture and new 5G security mechanisms as defined by 3GPP).
Samsung states in a whitepaper:
▪ With the launch of 5G Stand Alone (SA) networks, 3GPP mitigates some long-standing 4G vulnerabilities to enable much stronger security.
▪ At the same time, the way the Service Based Architecture ‘explodes’ the new 5G Core opens up potentially major new vulnerabilities. This requires a fundamentally new approach to securing the 5G Core, including comprehensive API security.
▪ Operators can communicate 5G SA’s new security features to some business users. Communication to consumers is more challenging because the benefit of new security enhancements will only come into effect incrementally over many years.
▪ Mobile network security cannot depend on 3GPP alone. Operators must apply robust cyber security hygiene and operational best practice throughout their operations.
In addition, the 5G network infrastructure must meet certain critical security requirements, such as the key exchange protocol briefly described below.
There are many other risks and challenges, such as the rising shortage of well-trained cyber security and cyber defense specialists. We will address these in this article. But first, a backgrounder….
5G Core Network Service Based Architecture (SBA):
To understand 5G security specifications, one has to first the 3GPP defined 5G SA/core network architecture.
5G has brought about a paradigm shift in the architecture of mobile networks, from the classical model with point-to-point interfaces between network function to service-based interfaces (SBIs).
The 5G core network (defined by 3GPP) is a Service-Based Architecture (SBA), whereby the control plane functionality and common data repositories of a 5G network are delivered by way of a set of interconnected Network Functions (NFs), each with authorization to access each other’s services.
Network Functions are self-contained, independent and reusable. Each Network Function service exposes its functionality through a Service Based Interface (SBI), which employs a well-defined REST interface using HTTP/2. To mitigate issues around TCP head-of-line (HOL) blocking, the Quick UDP Internet Connections (QUIC) protocol may be used in the future.
Here’s an illustration of 5G core network SBA:
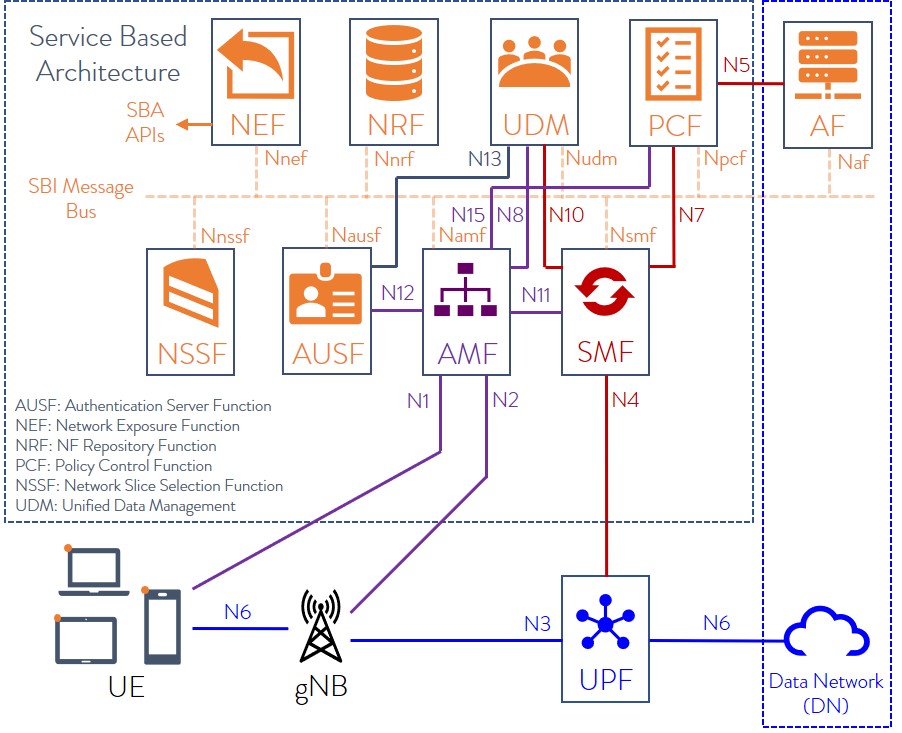
The 5G core network architecture (but not implementation details) is specified by 3GPP in the following Technical Specifications:
TS 23.501
System architecture for the 5G System (5GS)
TS 23.502
Procedures for the 5G System (5GS)
TS 23.503
Policy and charging control framework for the 5G System (5GS); Stage 2
The 5G network consists of nine network functions (NFs) responsible for registering subscribers, managing sessions and subscriber profiles, storing subscriber data, and connecting user equipment to the Internet using a base station. These technologies create a liability for attackers to carry out man-in-the-middle and DoS attacks against subscribers.
Overview of 3GPP 5G Security Technical Specifications:
The 5G security specification work are done by a 3GPP Working Group named SA3. For the 5G system security mechanisms are specified by SA3 in TS 33.501. You can see all versions of that spec here.
3GPP’s 5G security architecture is designed to integrate 4G equivalent security. In addition, the reassessment of other security threats such as attacks on radio interfaces, signaling plane, user plane, masquerading, privacy, replay, bidding down, man-in-the-middle and inter-operator security issues have also been taken in to account for 5G and will lead to further security enhancements.
Another important 3GPP Security spec is TS 33.51 Security Assurance Specification (SCAS) for the next generation Node B (gNodeB) network product class, which is part of Release 16.
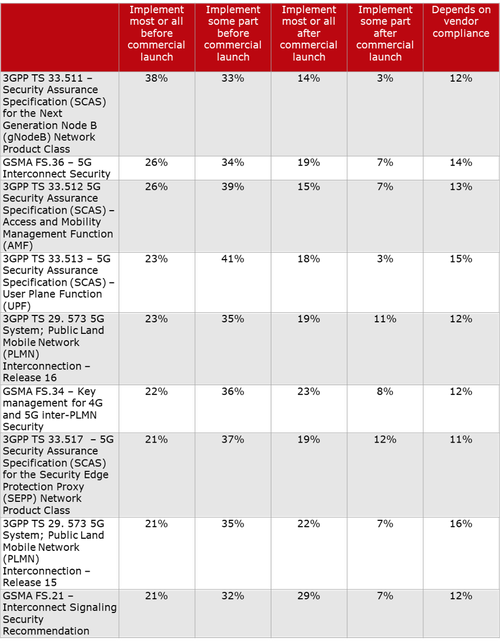
It’s critically important to note that ALL 3GPP security spec features and functions are required to be supported by vendors, but the are ALL OPTIONAL for 5G service providers. That has led to inconsistent implementations of 5G security in deployed and planned 5G networks as per this chart, courtesy of Heavy Reading:
Scott Poretsky, Ericsson’s Head of Security, wrote in an email to Alan:
“The reason for the inconsistent implementation of the 5G security requirements is the language in the 3GPP specs that make it mandatory for vendor support of the security features and optional for the operator to decide to use the feature. The requirements are defined in this manner because some countries did not want these security features implemented by their national telecoms due to these security features also providing privacy. The U.S. was not one of those countries.”
………………………………………………………………………………………………..

Overview of Risks and Potential Threats to 5G Networks:
A few of the threats that 5G networks are likely to be susceptible to might include those passed over from previous generations of mobile networks, such as older and outdated protocols.
-
Interoperability with 2G-4G Networks
For inter-operability with previous versions of software or backward compatibility, 5G must still extend interoperability options with mobile gadgets adhering to the previous generation of cellular standards.
This inter-operability necessity ensures that vulnerabilities detected in the outmoded Diameter Signaling and the SS7 Interworking functions followed by 2G-4G networks can still be a cause of concern for the next-generation 5G network.
-
Issues related to data protection and privacy
There is a likely possibility of a cyber security attack such as Man-in-the-Middle (MITM) attack in a 5G network where a perpetrator can access personal data through the deployment of the International Mobile Subscriber Identity (IMSI)-catchers or cellular rogue base stations masquerading as genuine mobile network operator equipment.
-
Possibility of rerouting of sensitive data
The 5G core network SBA itself could make the 5G network vulnerable to Internet Protocol (IP) attacks such as Distributed Denial of Service (DDoS). Similarly, network hijacking, which involves redirecting confidential data through an intruder’s network, could be another form of attack.
-
Collision of Politics and Technology
Government entities can impact 5G security when it comes to the production of hardware for cellular networks. For instance, various countries have new regulations that ban the use of 5G infrastructure equipment that are procured from Chinese companies (Huawei and ZTE) citing concerns over possible surveillance by the Chinese government.
-
Network Slicing and Cyberattacks
Network slicing is a 5G SA core network function (defined by 3GPP) that can logically separate network resources. The facility empowers a cellular network operator to create multiple independent and logical (virtual) networks on a single shared access. However, despite the benefits, concerns are being raised about security risks in the form of how a perpetrator could compromise a network slice to monopolize resources for compute-intensive activities.
3GPP
Public Key based Encryption Schemes:
3GPP has introduced more robust encryption algorithms. It has defined the Subscription Permanent Identifier (SUPI) and the Subscription Concealed Identifier (SUCI).
- A SUPI is a 5G globally unique Subscription Permanent Identifier (SUPI) allocated to each subscriber and defined in 3GPP specification TS 23.501.
-
SUCI is a privacy preserving identifier containing the concealed SUPI.

The User Equipment (UE) generates a SUCI using a Elliptic Curve Integrated Encryption Scheme (ECIES)-based protection scheme with the public key of the Home Network that was securely provisioned to the Universal Subscriber Identity Module (USIM) during the USIM registration.
Through the implementation of SUCI, the chance of meta-data exploits that rely on the user’s identity are significantly reduced.
Zero Trust architecture:
As 5G will support a massive number of devices, Zero Trust can help private companies to authenticate and identify all connected devices and keep an eye on all the activities of those devices for any suspected transgression within the network. While it has been successfully tested for private enterprise networks, its capability for a public network like open-sourced 5G remains to be gauged.
Private 5G Networks:
A private 5G network will be a preferred mode for organizational entities that require the highest levels of security taking into account national interests, economic competitiveness, or public safety. A fully private 5G network extends an organization with absolute control over the network hardware as well as software set-up. All of those mechanisms can be proprietary as the 5G private network deployment is only within one company’s facilities (campus, building, factory floor, etc).
Future of 5G Security:
The next-generation 5G-based wireless cellular network has put the spotlight on new opportunities, challenges, and risks, which are mandatorily required as the 5G technology makes great strides.
The 5G security mechanisms will continue to evolve in 3GPP (with Release 17 and above). Many of them will be transposed to become (“rubber stamped”) ETSI standards.
Note that 3GPP has not submitted its 5G core network architecture or 5G security specifications to ITU-T which is responsible for all 5G (IMT 2020) non-radio standards.
Europe’s General Data Protection Regulation (GDPR), applicable as of May 25th, 2018 in all EU member states, harmonizes data privacy laws across Europe. It could serve as a model for network security and data protection initiatives outside the European Union.
Conclusions:
The 5G network has the possibility to enhance network and service security. While 5G comes with many built-in security controls by design, developed to enhance the protection of both individual subscribers and wireless cellular networks, there is a constant need to remain vigilant and a step ahead in terms of technological innovation to thwart possible new cyber-attacks.
An end-to-end security framework across all layers and all domains would be essential. Introducing best practices and policies around security and resilience will remain imperative to future-proof 5G networks.
References:
https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3169
Author Bio:
Akash Tripathi is a Content Marketing strategist at Top Mobile Tech. He has 10+ years of experience in blogging and digital marketing. At Top Mobile Tech, he covers various how-to and tips & tricks related to iPhone and more related to technologies. For more about Akash, please refer to:
https://www.linkedin.com/in/akash-tripathi-42315959/
https://www.facebook.com/akash.tripathi.562
https://www.instagram.com/akashtripathi8/















![Toni Kroos là ai? [ sự thật về tiểu sử đầy đủ Toni Kroos ]](https://evbn.org/wp-content/uploads/New-Project-6635-1671934592.jpg)


